With an inundation of information from all angles regarding The Protection of Personal Information Act (POPIA), and the 1 July commencement date quickly approaching, organisations could be forgiven for feeling more than a little overwhelmed.
Emmanuel Tzingakis, Technical Lead for Trend Micro Sub-Saharan Africa, contemplates how POPIA can assist organisations to secure their data and be better enabled to handle any potential cyber threats.
What is POPIA?
With personal information becoming a hot commodity on the dark web it is critical to understand exactly how to protect data from cybercriminals. A recent global survey revealed that 79% of organisations experienced disruptions, financial loss or other setbacks due to a lack of cyber preparedness in 2020.
As work from home strategies are becoming the reality for a large percentage of the workforce, rapid changes to infrastructure have left some organisations with security vulnerabilities that could significantly impact their day-to-day operations.
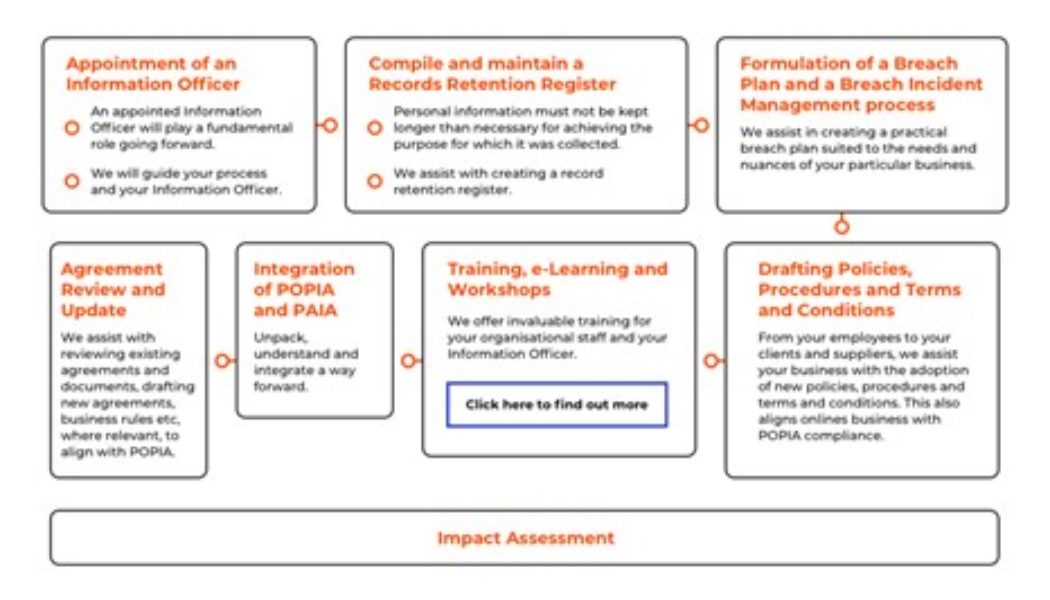
POPIA aims to protect the personal information of both consumers and employees by making sure businesses conduct the responsible collection, sharing and storage of information by holding them accountable should that information be breached. Although technology plays a pivotal role in helping organisations become compliant it must form part of a holistic security framework that includes people, information, systems, processes, physical surroundings, culture and processes.
First and foremost organisations must re-examine their security architecture, assess their industry, classify the information that is at the core of their business and what level of risk that information carries.
From there they can decide what measures need to be put in place to protect it. If they have a solid understanding of what information they are holding, which departments within the business should be privy to it and how and where it is going to be used, they will then gain a better understanding of what kind of security measures must be implemented to protect that data – and leave no question as to their POPIA compliance.
More and more businesses are now consolidating their data into a central repository such as the cloud. Understanding their roles and responsibilities versus those of the cloud service provider is also extremely important.
The cloud service provider is responsible for the security of the cloud, but organisations themselves are responsible for the security of the data in the cloud, which is why a full understanding of POPIA is essential to ensure that data is securely stored.
Cybercrime in South Africa
Cybersecurity breaches are happening on a daily basis. Organisations must have a 24/7 monitoring service so that data breaches can be detected immediately.
It has been shown that most companies aren’t aware of a data breach and that it can take as long as 175 days before they’re notified, and then it can take up to 55 days to respond and recover. By that time data has been severely compromised and millions of dollars may have been lost, not to mention the damage to reputation and subsequent lack of consumer trust. Vulnerability testing must be done regularly to make sure the technology and processes in place are robust with the ability to evolve as cybercrime becomes increasingly sophisticated.
Ensuring employee awareness is another crucial caveat when it comes to data protection. Training employees on how to handle personal information and secure any breaches is essential, especially since so many of them may be working in environments outside of the organisation which may not be secure.
Acquiring a cybersecurity expert or appointing a security officer to train employees on cybersecurity, and how POPIA impacts it, can mitigate risks and reduce vulnerabilities.
According to Accenture, South Africa has the third most cybercrime victims worldwide, losing billions of dollars a year. The commencement of POPIA will hopefully see this number drop.
But organisations cannot rely solely on the Act to keep them safe. Navigating the complexities around data protection, data privacy and the measures needed for cybersecurity is best done in collaboration with an expert that is properly equipped to give clear, accurate and actionable advice that is future-focused.
Edited by Luis Monzon
Follow Luis Monzon on Twitter
Follow IT News Africa on Twitter