tech news africa
How COVID-19 Has Driven a Cashless World Through Contactless Payments
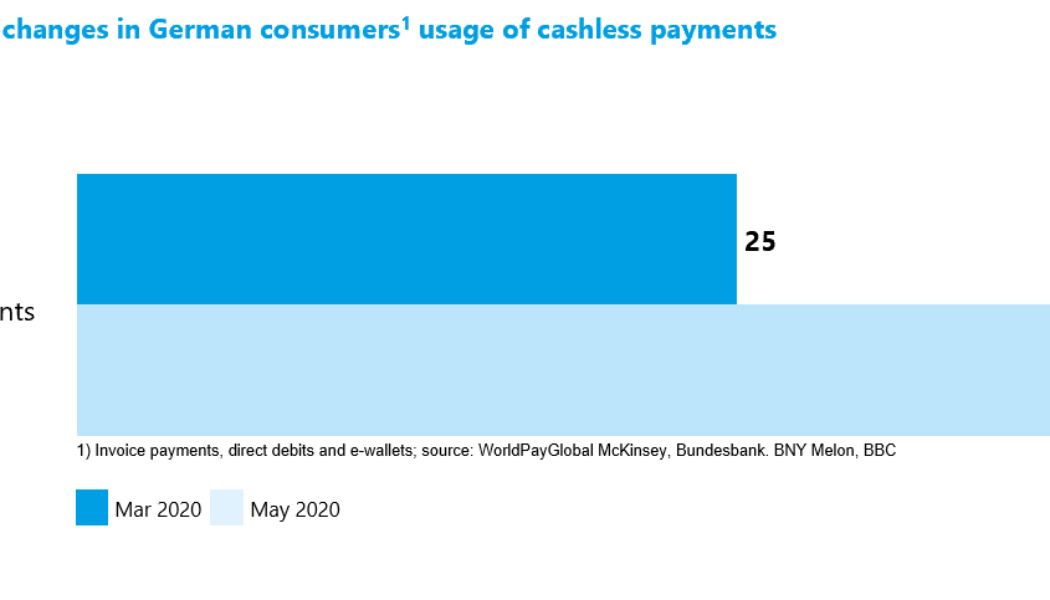
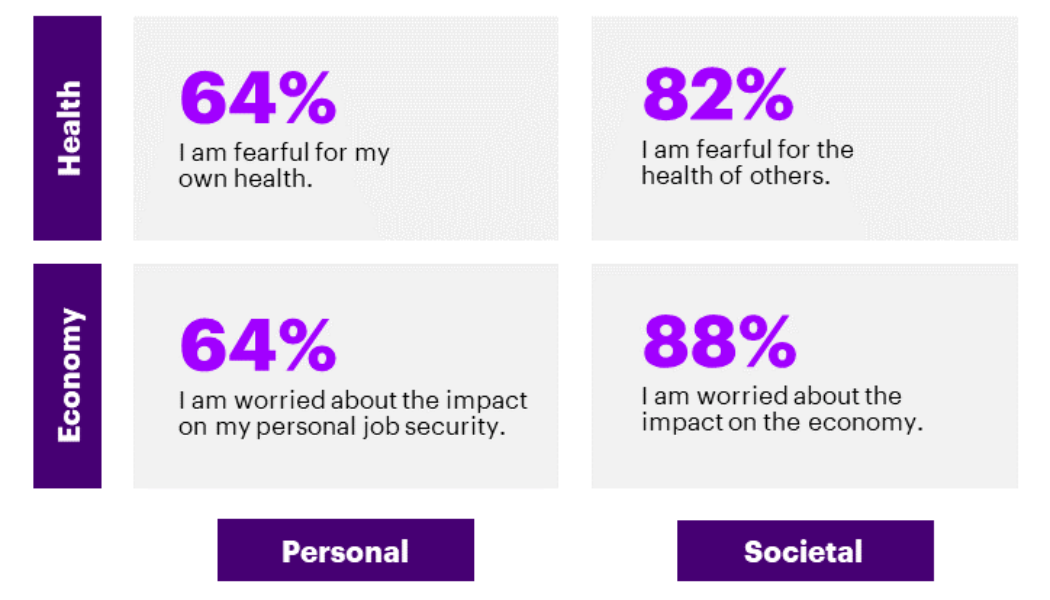
Image sourced from PYMNTS. /* custom css */ .tdi_4_560.td-a-rec-img{ text-align: left; }.tdi_4_560.td-a-rec-img img{ margin: 0 auto 0 0; } Driven by the COVID-19 pandemic, contactless payments have become the world’s preferred payment method. In addition to being safer from a viral transmission perspective, contactless payments are also faster, and integrating multiple contactless payment methods assists small businesses to better maintain financial liquidity. While choice in payment methods boosts Customer Experience (CX), we still have a way to go before South Africa fully embraces cashless payments. This will necessitate educating the population on card security and business owners on the benefits of contactless payments and the reduction of cash on hand. Formal vs Informal Trading /* c...
Location Intelligence is Key to Understanding New Customer Behaviours Post-Pandemic
Image sourced from Geospatial World. /* custom css */ .tdi_4_271.td-a-rec-img{ text-align: left; }.tdi_4_271.td-a-rec-img img{ margin: 0 auto 0 0; } The COVID-19 pandemic was a major disruptor for the retail sector. Practically overnight, customer buying patterns and behaviours changed, and have continued to shift ever since. This had made it challenging to meet customer expectations effectively. Retailers need to harness the power of location intelligence to help them better understand how their customers’ needs have changed and continue to change. What is Location Intelligence? Forrester, a research and advisory company, defines location intelligence as “the practice of collecting and managing customer location data, enriching it with other data sources, and analysing for contextual...
Vulnerabilities in Windows and Chrome Used in Series of Highly Targetted Attacks
In April, Kaspersky experts discovered a number of highly targeted attacks against multiple companies utilising a previously undiscovered chain of Google Chrome and Microsoft Windows zero-day exploits. One of the exploits was used for remote code execution in the Chrome web browser, while the other was an elevation of privilege exploit fine-tuned to target the latest and most prominent builds of Windows 10. The latter exploits two vulnerabilities in the Microsoft Windows OS kernel: Information Disclosure vulnerability CVE-2021-31955 and Elevation of Privilege vulnerability CVE-2021-31956. Microsoft has patched both today as part of Patch Tuesday. Zero-Day Attacks Recent months have seen a wave of advanced threat activity exploiting zero-days on the internet. In mid-April, Kaspersky experts...
Confidential Computing – Why Privacy Should be the Heart of Digital Experiences
Image sourced from Intel. In this past year, the consumer experience came to the forefront. As we faced various stages of lockdowns, we turned to online banking, seeing our doctors remotely, running our businesses using technology and socialising through a screen. Digital interactions became a part of our lives – ever-present and normalised as we navigated changes swept in by this pandemic. As our digital interaction became seamless and permeated through every aspect of our lives, privacy continued to be top of mind. We carried out our lives predominantly online – making many of us more vulnerable to fraudsters. As we navigated living our lives digitally, data theft dominated 2020 as the most common attack in the Middle East and Africa. Across the region, data theft and leaks accounted for...