Sponsored
Key Trends that Benefit Growing Businesses
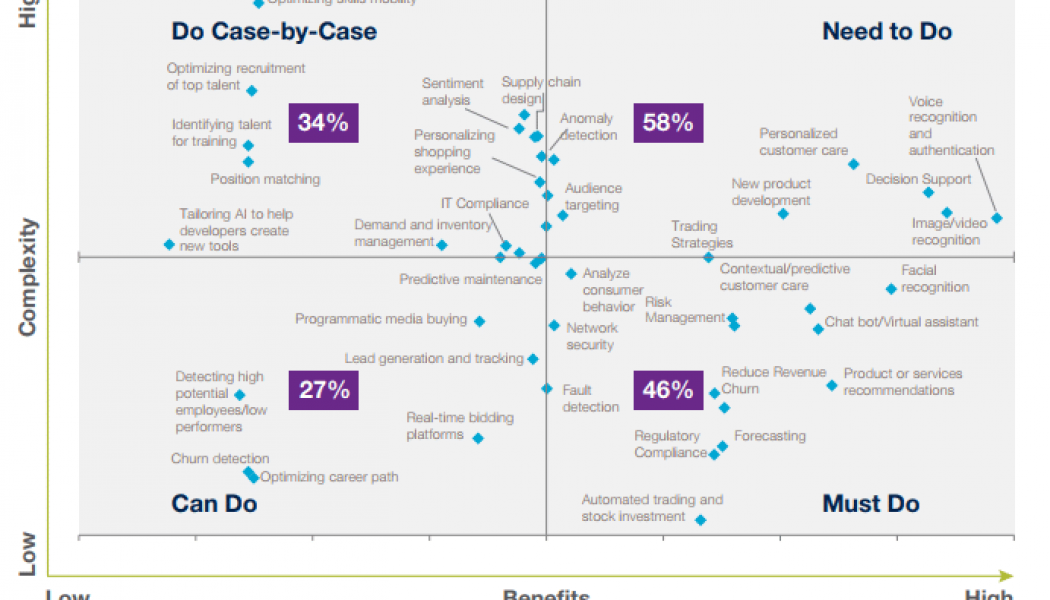
Sourced from HCAMag.com As everyone knows, trends are not permanent. However, just because certain business trends may not be here to stay, it doesn’t mean that savvy entrepreneurs can’t use them to achieve positive results in the meantime. Indeed, there are a number of key trends that are just now developing that can benefit growing businesses in significant ways. To that end, today we’ll review these exciting advancements and explain how growing companies can maximize their impact. Check it out here: Remote Employment There’s plenty of evidence to suggest that remote employment is more than just a passing fad. After all, remote employment has grown significantly over the past 10-15 years. However, COVID-19 has obviously forced many organizations to pursue a remote office set up –– ...
4 Keys to Successful Remote Management
Running a successful company is difficult even under the best of circumstances. Unfortunately, the past nine months have been far from ideal. Indeed, many business leaders have been forced to adopt a remote office setup to ensure the safety of their staff during the COVID-19 pandemic. As one can imagine, managing a team from a remote location is typically a daunting task –– to say the least. The good news is that it is possible to lead effectively despite these less-than-ideal conditions. To that end, here are four keys to successful remote management: Communication Obvious? Yes. Important? Absolutely. While communicating with your team might prove more difficult in a remote setup than in a traditional office environment, it’s nevertheless vital for business leaders to regularly conn...
The Role Of Artificial Intelligence In Enhancing Cybersecurity
The Cold War period fostered all sorts of technological advancements, whereas in contemporary times the more technologically advanced the world we have the more cybersecurity is at risk. Combining the quality of artificial intelligence (AI) with cybersecurity, security experts have extra assets to guard helpless systems and information against cyber assailants. After applying this innovation, it brought moment bits of knowledge, coming about in diminished reaction times. Artificial Intelligence And Bitcoins. We can barely avoid the role of artificial intelligence which is more beneficial in bitcoins trading. Bitcoin trader in the cryptocurrency market uses the exchange framework which is automatic in nature in order to earn confined wages. Valuable metals such as silver and gold are compar...
Set Schedule Reviews Market Data with AI
Have you ever wondered how real estate agents connect with home sellers? Lead generation is a big part of the business. Agents rely on a variety of techniques, including networking in order to get word-of-mouth referrals. But as with many fields, technology is changing the way that real estate agents do business. Real estate technology company Set Schedule uses artificial intelligence and machine learning to generate leads. How Set Schedule Reviews the Market Artificial intelligence and machine learning are well-suited to market analytics, and are already widely used in investing and trading. It’s only natural that there would also be applications for this technology in the world of real estate. Set Schedule reviews a variety of metrics, looking at historic market data, current housing pri...
7 Online Banking Security Tips for Africans
The Internet and the digital migration of the last three decades have pulled Africa closer to the rest of the world. Trends in various fields reach us more quickly now, and the continent is moving at the same rate as developed countries in markets such as online banking. Unfortunately, not many Africans know the risks they expose themselves to when accessing their bank accounts remotely and therefore go about making transactions without any caution whatsoever. In this article, we shall discuss top tips to avoid the security risks associated with online banking. 1. Use a VPN Do you have a device that you frequently use to access your online banking account? If you do, consider equipping it with a virtual private network. Virtual private networks (VPNs) anonymize internet connections, making...
Why it Pays to Invest in a Customer Acquisition Partner
The ability of technology vendors and service providers to attract new IT customers is critical to their survival. In 2020, the COVID-19 pandemic and subsequent lockdowns rapidly changed the everyday consumers’ life — forcing companies across the world to rethink the ways in which they generate leads and onboard new customers. In fact, a survey showed that 68% of organisations faced considerable challenges in this regard — marking one of the toughest times to reach a fresh audience. This, of course, has become a critical step to the survival of any organisation — albeit a costly one. Instead of relying on outdated and traditional strategies, an increasing number of businesses have opted to invest in a customer acquisition partner — a strategic partner that can persuade your prospects to pu...
Are there Signs of the Sudan Oil Industry Recovering?
IMAGE SOURCE: https://www.pexels.com/photo/gray-industrial-machine-during-golden-hour-162568/ Sudan was once the largest country in Africa before it was split into two countries in 2011, geographically redefining the state as Sudan (or North Sudan) and South Sudan. The geographical region where both countries lie has rich oil reserves. However, it is also a region hurting from the inside due to years of wars and internal conflicts. With both countries being dependent on oil production to support their economic stability and growth, the future development of countries lies in its oil industry performance. With conflicts, economic struggles, and the COVID-19 pandemic affecting the Sudan region, are there signs of the Sudan oil industry recovering? Read on as we explore some promising signs. ...
Altron People Solutions to Empower Organisations to do Business through the Virtual Business Academy
When South Africa and the rest of the world went into lockdown, it was clear for organisations that they had to reinforce the way they work and do business. Crucial to the current situation was realising that having remote employees and policies in addition to technology was going to be the solution to keep the doors open. However, working remote may be isolated now and then with nobody nearby that you can immediately ask help. Also, some employees will not openly admit to needing help to finish a task nor reach out if they have issues with technology compared to a conventional office setting. On the opposite hand, employers face the dilemma of how to successfully support remote working and ensure business continuity through increased productivity and effectivity. It is against...
Tips for Managing Large Intergration Projects
There are multiple departments within a company, each of which has a way of doing things. Project integration management brings all aspects of a project together in one cohesive place. As a project manager, it’s important to ensure all aspects of a project stay on track and have the tools and support system necessary to perform. Each piece of the project needs to seamlessly integrate with the other to result in a complete project. Here are some tips for managing large integration projects. Project Charter There is a certain skill and finesse needed to piece all the working parts of a project together. Successful project managers use their professional experiences as well as the advice of industry experts when working on a new project. Drafting a brief project charter do...
Managed Detection and Response Services – An Effective Defence to Knockout Sophisticated Cyberattacks
The accelerated adoption of cloud, digital transformation and remote working, in the wake of the ongoing pandemic, has expanded the attack surface for cybercriminals. Adversaries are also changing their tactics, techniques and procedures to increasingly launch cyberattacks that combine automation with active human interaction or “hands-on keyboard” hacking. In these types of attacks, adversaries attempt to manually circumvent preventive solutions, such as firewalls and endpoint security, and leverage administrator tools, pen test tool kits, and poorly designed or easily exploitable applications to escalate privileges and move laterally. Due to the increased use of these attack methods, IT leaders need to ensure their current cybersecurity defences can stand up against active cyberatt...