Security
Understanding the Need to Secure SD-WAN Platforms
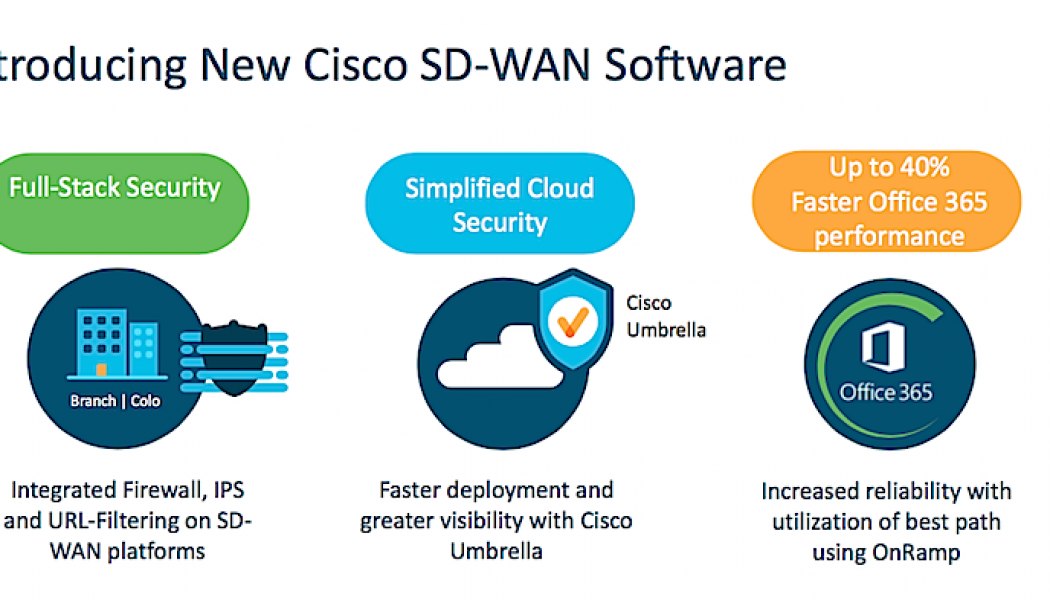
An increasing number of businesses are switching to a Software-Defined Wide Area Network (SD-WAN), which is a unique approach to wide-area networking because it combines traditional WAN technologies with the Internet and provides more visibility within an organisation. The move to SD-WAN is largely driven by distributed enterprises with multiple remote offices, which are increasingly using business-critical, cloud-based applications and tools that are migrating away from performance-inhibited wide-area networks (WAN). According to Louis Kirstein, DSM Expert for Connectivity Services at T-Systems South Africa, the visibility provided by an SD-WAN enables network administrators to oversee the network and monitor traffic for inconsistencies. From a security perspective, this functionality all...
How Using Cloud Can Increase Security for Remote Working During the Pandemic
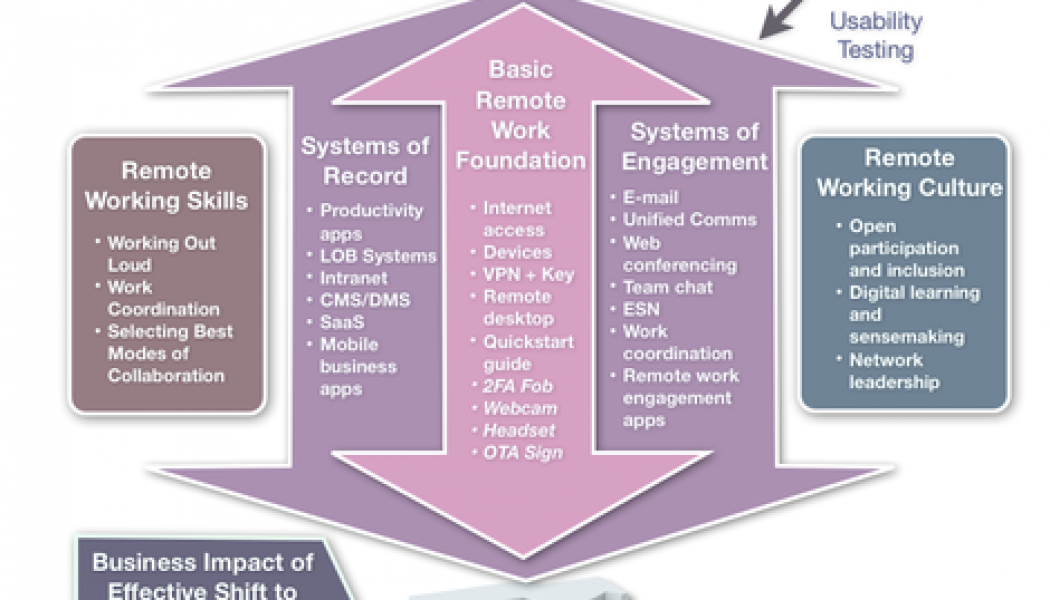
Sourced from Tapscape The cloud can enable organisations to quickly scale out enhanced security to a suddenly remote workforce, as part of efforts to ensure business continuity and disaster recovery – this is according to Patrick Grillo, Senior Director and Solutions Marketing at Fortinet. The pandemic had created unique challenges for employers and employees across all sectors around the world, with Varun Kukreja, Senior Program Manager – IT Security MEA, IDC Middle East, Africa, & Turkey, saying securing the teleworker had become a top priority, with some 90% of organisations looking to provide staff with secure access to IT services and applications. The pandemic had also accelerated digital transformation, he says, with an IDC Meta survey interim results revealing that some 56% of ...
Google Launches Website to Help People Avoid Online Scams
Sourced from Google. Ever opened your emails and received a poorly-worded message about a payment that you weren’t expecting? What about one proclaiming that you’ve won a competition you never entered. “Congratulations!” it reads, beneath, a sinister attachment that you probably should not open. This is becoming more and more common, and now Google has unveiled a website to teach people how to spot and avoid online scams. Digital hoaxes, malware and cyberattacks have been surging during the ongoing coronavirus pandemic. The website – Scamspotter.org – tries to show users how to identify things such as false stimulus checks, fake vaccine offers, or other fake medical information. The site also attempts to make clear certain patterns that are typical of hoaxes, like a romance scammer asking ...
Check Point Software Partners Strathmore University to Promote Digital Skills in Kenya
Sourced from Business News Daily Cybersecurity solutions company, Check Point Software has announced that its education initiative has partnered with Strathmore University in Kenya to provide a comprehensive cybersecurity curriculum to students, bridging the digital skills gap and also creating a safer local cyber landscape. According to research, the number of unfilled cybersecurity roles now stands at 4.07 million professionals globally. What causes alarm for those within the security market across Africa is that the ICT courses across a range of disciplines are still underdeveloped, as well as the skills required to operate, support and understand the complexities of next-generation technologies and threats. Introducing the Check Point SecureAcademy To keep up with the current thr...