Security
Exclusive Networks Africa Continues its Expansion Plans Throughout the Continent
Exclusive Networks Africa, which represents the continental arm of this global, trusted cybersecurity specialist for digital infrastructure, is continuing its expansion into Africa, building presence within the sub-Saharan region in recent months, including the opening of a formal office in Lagos, Nigeria. This adds to the existing offices in South Africa, Kenya and Mauritius. Because Africa is seen as a growth market by the Group, it is widely recognised as an important investment destination, allowing for a strong focus on the company’s vendor partners, both current as well as potential. This is according to Anton Jacobsz, Managing Director of Exclusive Networks Africa, who clarifies: “Having previously operated in a number of countries across Africa with the support of representatives t...
What is Good Cloud Migration Security?
Sourced from InfoWorld. Cloud adoption continues to be important for many organizations as they transform how they do business in today’s digital world. While there are many benefits associated with cloud adoption, the security implications of moving to the cloud cannot be ignored if organizations are to fully embrace it. This blog outlines the benefits of cloud migration and the security challenges associated with the process. Also, there is a list of best practices for creating a powerful cloud migration security strategy. What is Cloud Migration? Cloud migration is the process of transferring an organization’s data and apps from on-premises servers to a cloud infrastructure. Cloud infrastructure enables organizations to access data storage requirements and computing capabilities when th...
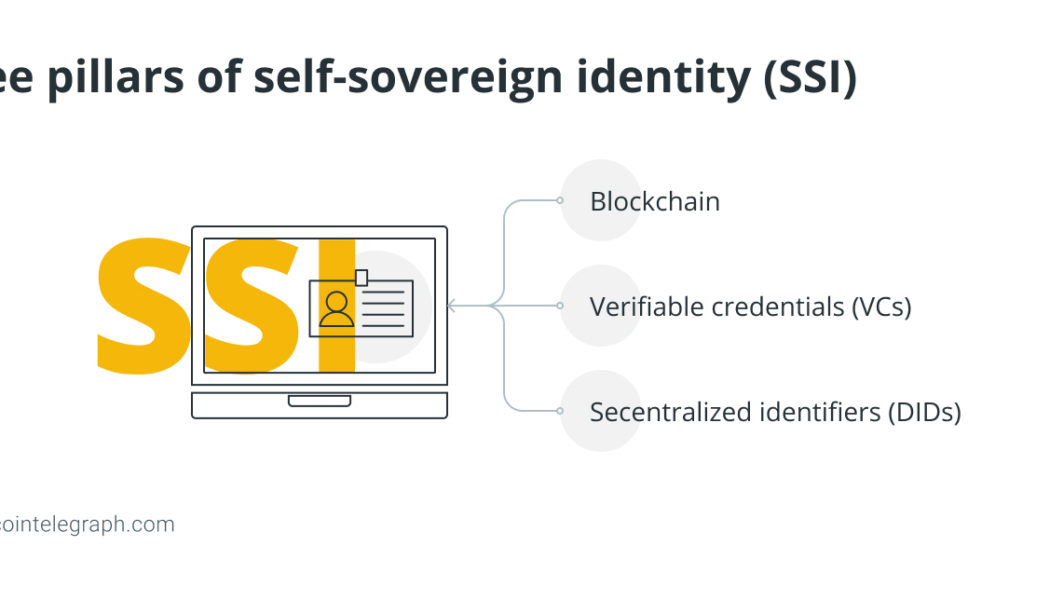
What is decentralized identity in blockchain?
Self-sovereign identity is a concept that refers to the use of distributed databases to manage PII. The notion of self-sovereign identity (SSI) is core to the idea of decentralized identity. Instead of having a set of identities across multiple platforms or a single identity managed by a third party, SII users have digital wallets in which various credentials are stored and accessible through reliable applications. Experts distinguish three main components known as the three pillars of SSI: blockchain, verifiable credentials (VCs) and decentralized identifiers (DIDs). Blockchain is a decentralized digital database, a ledger of transactions duplicated and distributed among network computers that record information in a way that makes it difficult or impossible to change, hack or cheat. Seco...