Security
DPR: Market forces should determine gas prices
File Photo The Department of Petroleum Resources (DPR) has advocated that market forces should be allowed to determine gas prices to guarantee the security of supply and demand of the commodity. Mr Sarki Auwalu, the Chief Executive Officer, DPR, disclosed this while presenting keynote address at the pre-summit conference on “Decade of gas’, in Abuja, on Monday. Auwalu said that the right and market-based pricing of gas was critical, as it would assure producers of returns on their investments. He also outlined five critical levers for gas development, especially as Nigeria moves to leverage its abundant gas resources for national growth, diversification of the economy and to use gas as the fuel for economic transformation. According to him, the levers include availability, accessibility, a...
Yiaga Africa demands effective monitoring, evaluation of coronavirus vaccination
A Civil Society Organisation, CSO, Yiaga Africa, on Monday, demanded effective monitoring and evaluation of COVID-19 vaccination and also strengthening the nation’s health sector. This was stated by the Director of Programmes, Yiaga Africa, Cynthia Mbamalu, while speaking on the need for the vaccination to be guided by certain principles that would bring about the inclusion of all citizens in the process. Mbamalu said: “The conversation is important to ensure that the whole process of vaccination is guided by certain principles and every aspect of society is catered for. In the implementation of vaccines in Nigeria, we need to deploy effective monitoring and evaluation systems that will help document how well we have done, document the learning, and how we can improve on the system. “Beyon...
Why Cybersecurity is Crucial in the Age of Tap-to-Pay
Tap-to-Pay is by no means a new technological development, but thanks to the COVID-19 pandemic, it has become increasingly popular as a method of payment since it is ostensibly contactless. It is also a payment method that can be used even without a card, since many wearable devices such as smartwatches feature tap and go payment options. With rumours that Apple Pay will be launching in South Africa this year, it is likely to become increasingly available. However, this begs the question, what about security? When no physical card is required and often not even the authentication of a Personal Identification Number (PIN) for smaller transactions, who is responsible? The reality is that banks, merchants and users all need to play their part to minimise fraud and safeguard their money. Are c...
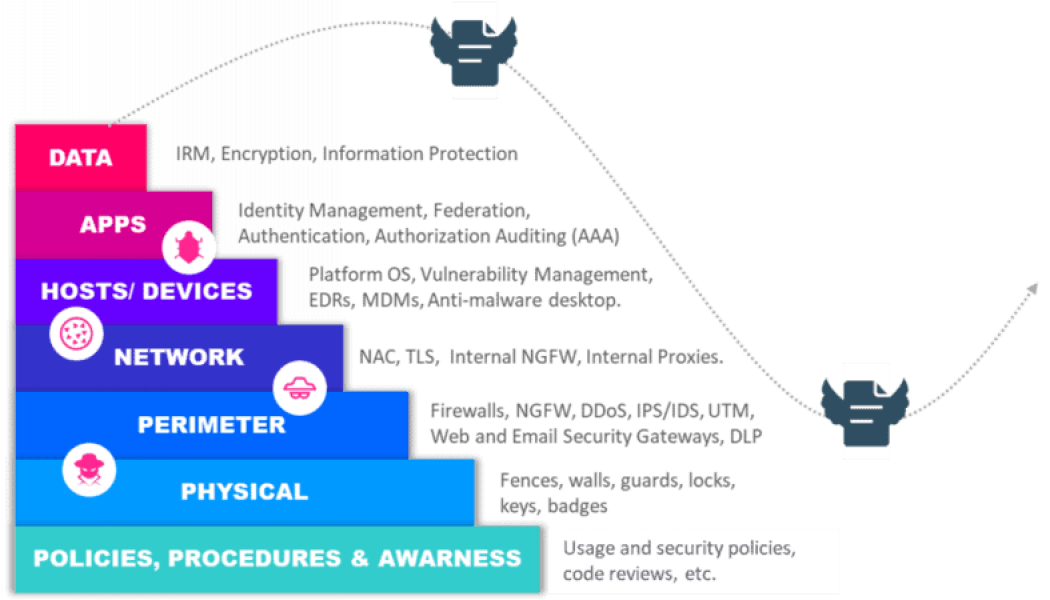
Protecting the IT Landscape in a Borderless World
The evolution of technology has pushed the perimeter of organisations further and further towards the edge, and we no longer have the monolithic structures we did in the past. The cloud, the Internet of Things (IoT), even the COVID-19 pandemic accelerating the adoption of a work from home model, have contributed to what has, in effect, become a borderless world. This means that the traditional approach to security of locking down the perimeter is simply no longer enough. The perimeter cannot be easily defined, and the way in which we access services has fundamentally changed. Cybersecurity mesh has emerged as a framework to address this challenge, with a distributed security architecture that more effectively meets the challenges of today’s landscape. Trust no one With IT infrastructure so...
Fixing Your Cybersecurity Issues 1 Next-Gen Firewall at a Time
Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited Africa When did you last check your firewalls as a barrier to entry against cybercriminals? And, perhaps more importantly: does your organisation still rely on a legacy firewall, or has it upgraded to a next-generation firewall (NGFW)? And have you considered the ‘Broken window’ principle when looking at your internal cybersecurity posture, in order to have a positive effect on your business processes? These questions are posed by Stefan van de Giessen: General Manager: Cybersecurity at Networks Unlimited Africa, who says, “The broken window theory rests on the idea that a neighbourhood or community that appears to be orderly and well-kept will be less susceptible to crime. Conversely, one that has many broken wind...
Group urges service chiefs to fish out criminal elements
Following the activities of armed bandits in the country, group has charged the new service chiefs to address the current Insecurity situation in the North East, particularly Maiduguri, which they noted,was the epicenter of insecurity in the country. By way of appeal the group urge the new security heads adopt a new strategy, hit the ground running by relocating to the theatre of the war against terrorists for at least six months in the first instance and not national tour. In a statement, Wednesday, the experts operating under the aegis of Coalition of Concerned Nigeria Security Experts noted that two months after the current security chiefs assumed office, insecurity was assuming a new dimension. In the statement by its National Coordinator, Prof. Otedola Adekunle and National Secretary,...