Security
DeFi-type projects received the highest number of attacks in 2022: Report
It’s no secret that in 2022 the world of Web3 and decentralized finance (DeFi) experienced a slew of major exploits and attacks. From the Ronin bridge attack to the Nomad hack, the top 10 exploits alone saw over $2 billion lost. In the Beosin Global Web3 Security Report 2022, it revealed that of 167 major security incidents over the last year those rooted in DeFi were the most vulnerable. DeFi projects were attacked 113 times, which accounted for approx. 67.6% of recorded attacks. This is followed by attacks on exchanges, nonfungible token (NFT) projects, cross-chain bridges and wallets in that order. According to the report, DeFi projects came in second in terms of monetary losses with a total of $950 million in losses. This follows the $1.89 billion lost in cross-chain bridge exploits in...
Crypto companies aim to build trust within future products and services
The cryptocurrency ecosystem underwent a turbulent year in 2022. Criticism inside and outside of the crypto industry was fueled following the collapse of FTX, Celsius, Three Arrows Capital and the Terra ecosystem. A number of losses have been recorded from these events. Blockchain analytics firm Chainalysis released a report in December of last year, which noted that the depegging of Terra’s stablecoin, Terra USD Classic (USTC), saw weekly-realized losses peak at $20.5 billion. Findings further show that the subsequent collapse of Three Arrows Capital and Celsius in June 2022 saw weekly-realized losses reach $33 billion. While these events may have resulted in a loss of trust within the crypto ecosystem, it’s important to point out that blockchain technology and cryptocurrency have n...
Indonesia to launch national crypto exchange in 2023: Report
As a part of its reform of crypto regulation, Indonesia will create a crypto exchange in 2023, according to reports. The platform is planned to be launched prior to a shift of regulatory power from commodities to securities authority. On Jan. 4, the head of the Commodity Futures Trading Regulatory Agency of Indonesia (Bappebti), Didid Noordiatmoko, stated that a crypto exchange should be set up this year. The move comes as a part of broader financial reform launched in December 2022. In accordance with the reform, in the next two years, the crypto oversight will be taken from Bappebti, a commodities-focused agency, by the Financial Services Authority (FSA). The Financial Sector Development and Reinforcement bill (P2SK) was ratified by the House of Representatives of Indonesia on Dec....
BitKeep exploiter used phishing sites to lure in users: Report
The Bitkeep exploit that occurred on Dec. 26 used phishing sites to fool users into downloading fake wallets, according to a report by blockchain analytics provider OKLink. The report stated that the attacker set up several fake Bitkeep websites which contained an APK file that looked like version 7.2.9 of the Bitkeep wallet. When users “updated” their wallets by downloading the malicious file, their private keys or seed words were stolen and sent to the attacker. 【12-26 #BitKeep Hack Event Summary】1/n According to OKLink data, the bitkeep theft involved 4 chains BSC, ETH, TRX, Polygon, OKLink included 50 hacker addresses and total Txns volume reached $31M. — OKLink (@OKLink) December 26, 2022 The report did not say how the malicious file stole the users’ keys in an unencrypted form. Howev...
LastPass attacker stole password vault data, showing Web2’s limitations
Password management service LastPass was hacked in August 2022, and the attacker stole users’ encrypted passwords, according to a Dec. 23 statement from the company. This means that the attacker may be able to crack some website passwords of LastPass users through brute force guessing. Notice of Recent Security Incident – The LastPass Blog#lastpasshack #hack #lastpass #infosec https://t.co/sQALfnpOTy — Thomas Zickell (@thomaszickell) December 23, 2022 LastPass first disclosed the breach in August 2022 but at that time, it appeared that the attacker had only obtained source code and technical information, not any customer data. However, the company has investigated and discovered that the attacker used this technical information to attack another employee’s device, which was then used...
Crypto on-chain crime drama sees the good guys finally win
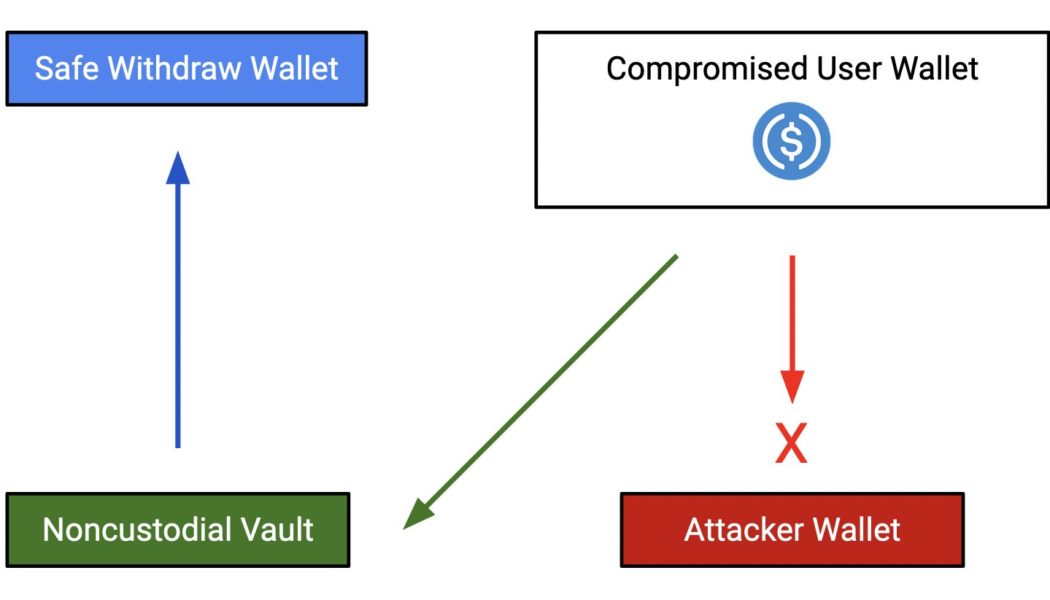
The stories about people getting their private keys hacked or stolen are nothing new, with a number losing their life savings because of these thefts. However, in quite an anti-climax scene, a crypto user managed to save their crypto holdings despite losing their private keys. Harpie, an on-chain security firm, revealed an instance of on-chain crime drama where the good guys eventually won. One of the users in their Discord group reportedly raised concerns about the suspected theft of their private keys. When the firm looked into said customer’s wallet, someone was indeed trying to transfer funds from the victim’s accounts. How did we do this? About a month ago, this user protected their tokens with Harpie. By approving and protecting their tokens with Harpie, this user gave us permis...
Gensler’s approach toward crypto appears skewed as criticisms mount
Since taking over at the United States Securities and Exchange Commission (SEC), chairman Gary Gensler has repeatedly been referred to as the “bad cop” of the digital asset industry. To this point, over the past 18 months, Gensler has taken an extremely hard-nosed approach toward the crypto market, handing out numerous fines and enforcing stringent policies to make industry players comply with regulations. However, despite his aggressive crypto regulatory stance, Gensler, for the most part, has remained mum about several key issues that digital asset proponents have been talking about for a long time. For example, the SEC has still failed to clarify which cryptocurrencies can be considered securities, stating time and again that most cryptocurrencies in the market today could be classified...
‘Father of the iPod’ helps Ledger create new cold crypto wallet
Hardware wallet provider Ledger, known for its cold-storage devices, announced its seventh crypto wallet in collaboration with the creator of the original iPod. Tony Fadell, the inventor of the iconic iPod Classic model, has partnered with Ledger to help the company design its latest wallet device known as Ledger Stax. The company broke the news on Dec. 6 at Ledger’s bi-annual Web3 developer event, Ledger Op3n, in Paris. Ledger’s upcoming new hardware wallet is a credit card-size device that features a large E Ink display, capacitive touch, Bluetooth support, wireless charging and more. For the first time in Ledger’s product line, Stax contains a curved E Ink display which can be used to show the holder’s name or other wallet information, just like a book spine. The device is a...
Cut through the clutter for proactive security with a threat-centric SOC
Simeon Tassev, MD and QSA at Galix IT and information security are critical, but when you have multiple systems throwing out hundreds of alerts every day, it is easy to become ‘alert fatigued’. Alerts relating to real, business threats can easily be lost in the sheer volume, giving malicious attacks a gap and making your business vulnerable. Adding intelligence around this process through a threat-centric Security Operations Centre (SOC) can help businesses prioritise incidents and more easily detect higher-risk threats affecting multiple locations and systems, for improved incident response and better security. The evolution of the SOC A SOC has become essential for business today, whether this is an in-house department or delivered via a managed services partner, responsible for monitori...