Security Online
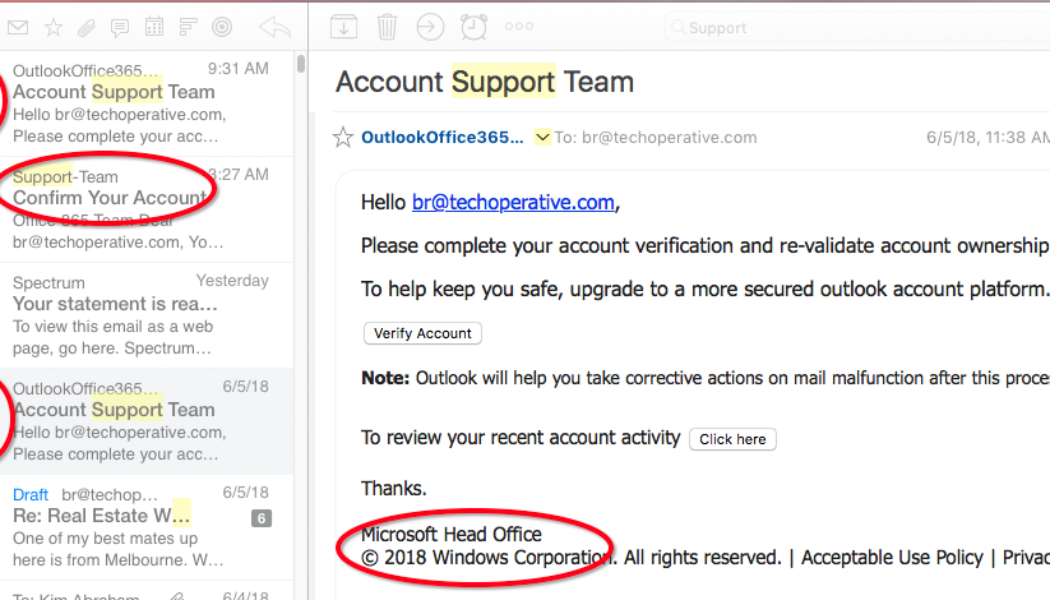
How to Be Safe From the “Reset Password” Email Scam
Image sourced form Broad Media Most online services have built-in security systems that alert employees when the systems detect “unusual” activity on their accounts. For example, legitimate email services or similar will send notifications about attempts to reset the phone number and e-mail address linked to the account, or the password. Of course, as soon as such messages became commonplace, enterprising cybercriminals tried to imitate this mechanism to attack corporate users. As cyberattacks rely on the human factor more often each year, and as cybersecurity technologies progress, such tricks are becoming more and more common and are being registered in multiple mailouts around the world. The scenario is usually as follows: if it’s a public online service attacker it will usually make ev...
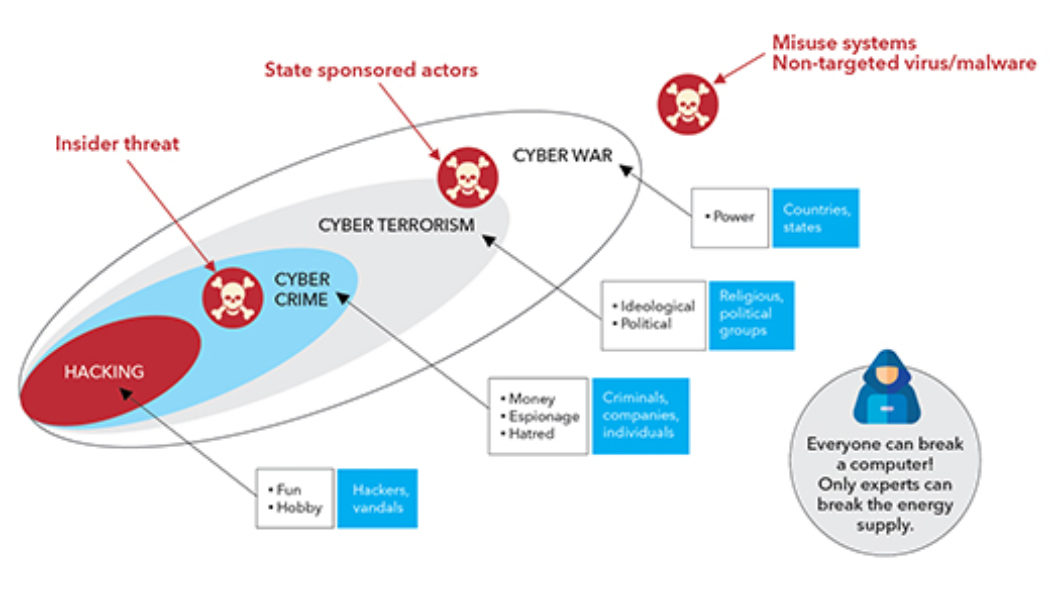
Is South Africa a Playground for Cybercriminals?
The Attacks From All Angles 2021 Mid-year Cybersecurity Report by Trend Micro highlighted a 47% year-on-year increase in email threats as well as malicious files and URLs in the first quarter of 2021 globally. South Africa’s technology landscape is almost identical to that of other countries, which has seen black hat hackers using it as a testing ground for cybersecurity attacks before these are launched on their intended end-users. Ransomware Remains the Prime Threat Globally, ransomware remained the standout threat in the first half of the year. The pandemic has highlighted how easy it is to buy ransomware as a service (Raas) on the dark web. Africa accounted for 1.7% of these attacks, with 1.05% being targeted at South Africa. Our findings show that locally, South Africa was in the top ...
Is Cybersecurity as Necessary as Electricity?
Sourced from Travellers Cybersecurity has become as much a business necessity as having electricity says South African financial services and insurance company, Sanlam. Threat actors are constantly evolving and relentlessly hunting for vulnerabilities, cybercrime has become so profitable that exploitation is their business priority, and regulation is increasingly complex to navigate and manage. For Sanlam, cybersecurity has always been more than plugging holes and filling gaps, it’s a priority that has to be embedded within business foundations while managing cost, growth, customer experience, data analytics and regulatory controls. “Developing a comprehensive and holistic cybersecurity solution is a mandate for us, one that we must meet to ensure customer, stakeholder and industry trust. ...