Ransomware attack
Fight Back Against the Rise of Ransomware in SA with EDR Solutions
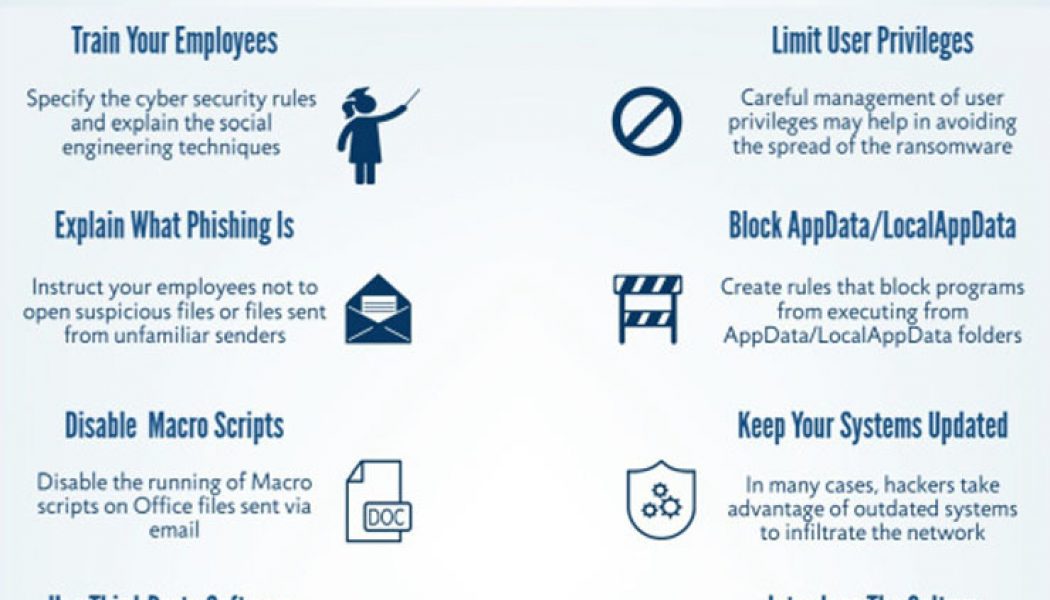
When cyberattacks are on the rise, as they certainly have been in South Africa this year, an organisation cannot afford to have its cybersecurity operating in a reactive manner. And yet, far too many businesses operate in this manner, making them prime targets for a breach. This is according to Milad Aslaner, Senior Director, Cyber Defense Strategy at SentinelOne, which helps organisations to prevent, detect, respond to and remediate end-point threats using artificial intelligence (AI) and machine learning. Its endpoint security products are distributed throughout Africa by Networks Unlimited. Aslaner explains: “Endpoints including laptop computers, tablets, and phones provide entry points to a wider network penetration that could harm the organisation, and which is one of the goals of ran...
How to Successfully Recover from a Ransomware Attack
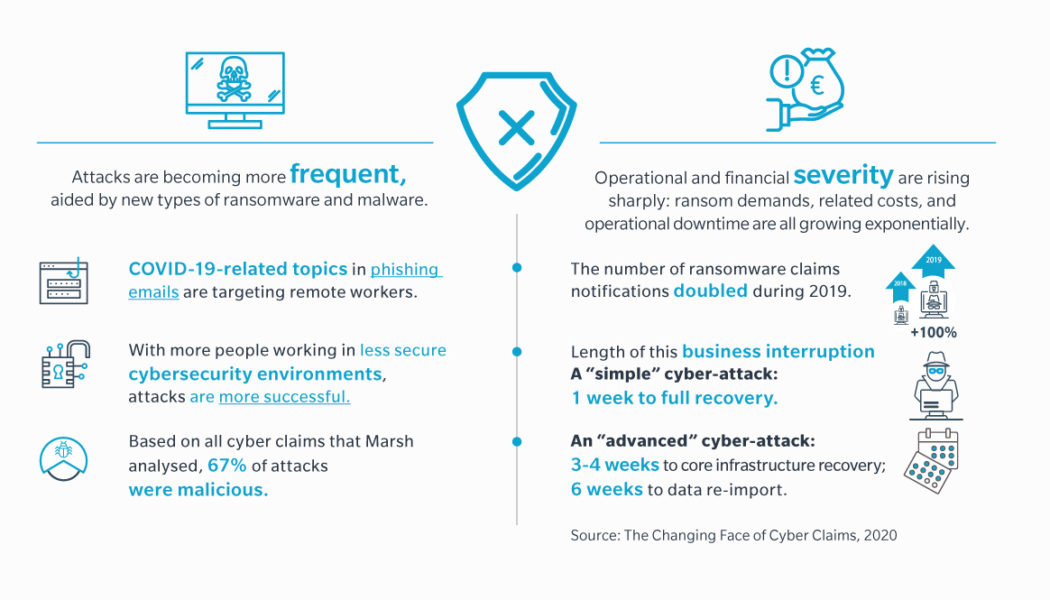
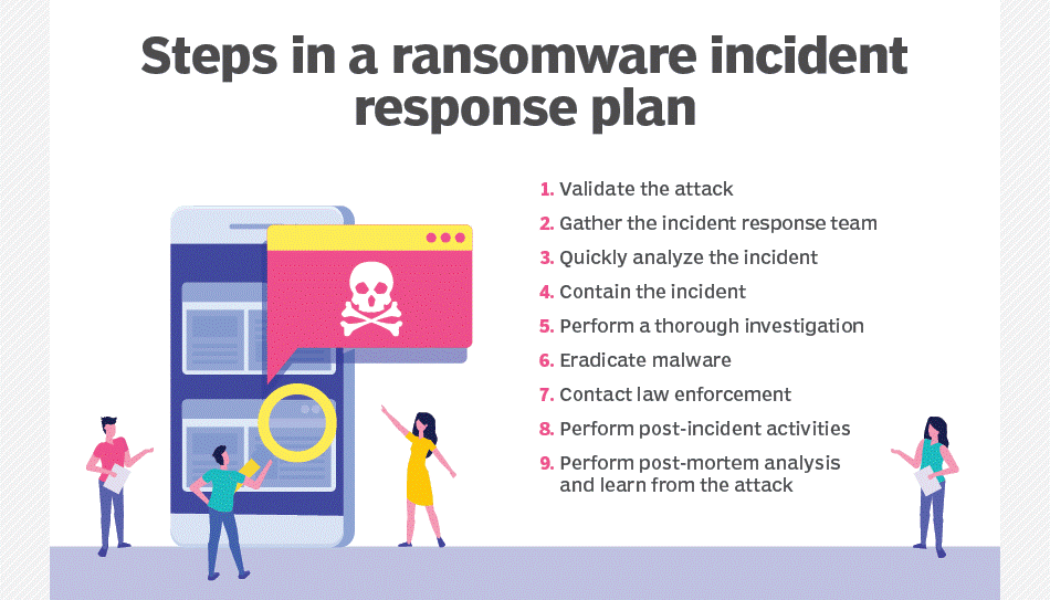
Sourced from Kaspersky South Africa is an attractive target for cybercriminals for a number of reasons, and the last few years have seen a sharp rise in high-profile ransomware attacks. One of the key motivations driving this volume of attacks is the fact that data is a de facto currency and an extremely valuable commodity on the black market. While backup is a critical component of data protection, when this backup is also encrypted by malicious software, companies are often left with few options other than to pay the ransom. Therefore, an effective Cyber Recovery strategy, which enables businesses to get back up and running without having to give in to criminal demands, is the key. Ransomware on the Rise The rapid adoption of digital transformation, Artificial Intelligence (AI) and the I...
Ireland’s health service IT systems shut down by ransomware attack
Ireland’s health service said it was under a ransomware attack on Friday that forced it to shut down its computer systems. A ransomware attack locks users out of their computer systems until they pay a fee to the intruder. There were few details, but the attack was described as significant by Ireland’s Health Service Executive. Motorists line up for fuel at one of the few remaining gas stations that still has fuel in Arlington, Virgina, on May 13, 2021. AFPBiden says oil pipeline back in operation after cyber attack It said it was shutting down all its IT systems to protect them from the attack while it consulted security partners. Covid-19 vaccinations would still go ahead as planned, the agency said. “We apologise for inconvenience caused to patients and to the public and will give furth...
Apple Reportedly Targeted in $50 Million Ransomware Attack
Apple Inc has reportedly suffered a ransomware attack at the hands of REvil operators. The hackers have revealed that the tech company has until 1 May to pay the ransom or risk losing confidential drawings and gigabytes of personal data. “Our team is negotiating the sale of large quantities of confidential drawings and gigabytes of personal data with several major brands,” says REvil operators. “We recommend that Apple buy back the available data by May 1.” According to The Record, the REvil gang asked for a $50 million ransom demand, similar to the sum they requested from laptop maker Acer last month. Denis Legezo, Senior Security Researcher for Kaspersky’s Global Research and Analysis Team, says “REvil ransomware has been known since 2019 and it can both encrypt data and steal it. I...
- 1
- 2