phishing
How a Small Email Phish Can Become a Million Rand Ransom
Image sourced from Kaspersky. Cybercrime is smart, innovative, and agile. Cybercriminals are well-rewarded for their innovative attack vectors and have no incentive to stop finding inventive ways of penetrating systems and moving past the most vulnerable defences. According to Paul Grapendaal, Head of Managed Security Services at Nclose, there’s no standard playbook when it comes to penetrating a system successfully, but there are solid security steps that can mitigate risk and help the business manage the fallout. Steps that will help bolster your defences and ensure that one phish won’t cost your business millions. Paul Grapendaal, Head of Managed Security Services at Nclose. “There are obvious routes of attack, such as spear phishing, that are designed to focus on a target with the sole...
Beware: Microsoft is One of the Most Impersonated Brands in Phishing Attacks
Image sourced from NS Energy. Check Point Research for the second quarter of 2021 found that Microsoft was the most popular brand used to lure unsuspecting individuals and employees. This isn’t hard to believe because Microsoft’s Active Directory, continues to dominate the market share globally in 2021 and as a result is still the most popular target for phishing. The weight of this risk is emphasised by the fact that in 2021, phishing attacks increased by 47% in just the first quarter alone. The threats are smart, capable, and worrying – increasing in volume every year. Companies are facing an onslaught of risk that’s designed to fool employees into making mistakes that can cost the company money and reputation. “The risk is when employee credentials are stolen, this can lead to detriment...
Protect Yourself: Top 10 Most Common Phishing Email Subject Lines
KnowBe4, the provider of one of the world’s largest security awareness training and simulated phishing platform, has announced the results of its Q3 top-clicked phishing report. “Social engineering attacks continue to be one of the top ways malicious hackers breach organizations and/or cause damage,” said Stu Sjouwerman, CEO, KnowBe4. “We are seeing a continued increase in phishing, including more use of common HR types of communications and less reliance on obvious social media phishing campaigns. By equipping security professionals with more data on likely tactics and templates used by cybercriminals executing phishing attacks, infosec professionals can strengthen their human firewall. Now more than ever, end-users need to remain vigilant and remember to stop and think before they click....
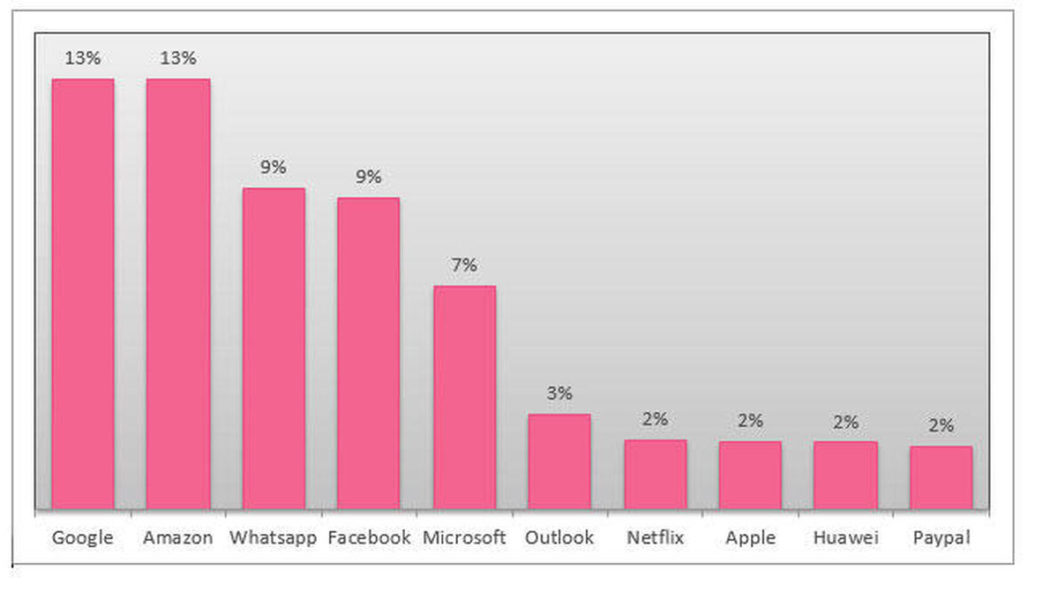
Beware: These Are The Top 10 Brands Imitated in Phishing Attacks
Image sourced from Kaspersky. Check Point Research (CPR), the Threat Intelligence arm of Check Point Software Technologies, a leading provider of cyber security solutions globally, has published its new Brand Phishing Report for Q3 2021. The report highlights the brands which were most frequently imitated by criminals in their attempts to steal individuals’ personal information or payment credentials during July, August and September. In Q3, Microsoft continued its reign as the brand most frequently targeted by cybercriminals, albeit at a slightly lower rate. Twenty-nine per cent of all brand phishing attempts were related to the technology giant, down from 45% in Q2 2021, as threat actors continue to target vulnerable, distributed workforces during the COVID-19 pandemic. Amazon has replac...
When It Comes to Cybercrime Beware of Social Engineers
You would be forgiven for thinking that terms like phishing, vishing, whaling, and pharming all had something to do with either a water sport or a pharmaceutical company, but every one of these is a cybercrime attack. These attacks leverage social engineering techniques to hack personal accounts, infect devices with ransomware, gain access to organisations or steal information to be sold on to the highest underground bidders. As Anna Collard, SVP of content and evangelist at KnowBe4 Africa points out, it has become absolutely essential for people to be mindful of what they post on social media. Anna Collard, SVP of content and evangelist at KnowBe4 Africa. “The risk of identity theft has never been greater and according to a report by SAFPS, has increased by 337% in 2020,” she says. “When ...
Most SAns Would Stop Trusting Brands Involved in Phishing Attacks – Survey
Image sourced from Kaspersky. According to the global Brand Trust survey by cybersecurity company Mimecast, almost three-quarters (74%) of South African consumers would stop buying from a brand if they fell victim to a phishing attack involving that brand, with 93% of South African consumers expecting their favourite brands to ensure their services, such as websites, emails and other communication, are safe to use. Heino Gevers, cybersecurity expert at Mimecast, says brands need to do more to protect their customers from cybercriminals. “South Africans are incredibly trusting with 69% of consumers not hesitating to open an email from brands they use regularly, and 56% readily clicking on links from their favourite brands. However, with cyber threats- including impersonation attacks and phi...
3 Trends to Understand the Evolving Cybersecurity Landscape
Image sourced from Feed Navigator. Given the global disruption that took place last year, it is hardly surprising that malware increased by 358% and ransomware by 435% as compared to 2019. The rapid push to digitalise and embrace work from home solutions meant companies not only had to accelerate data migration projects to the cloud but also remain cognizant of how best to secure employee endpoint devices while keeping the impact on productivity to a minimum. What makes the likes of malware and ransomware so difficult to combat is that successful attacks on corporate networks and endpoint devices can potentially remain hidden for months giving the hacker access to a veritable treasure trove of information. Attackers can encrypt this compromised data at any time, resulting in significant da...
Beware: The Top 5 Cybercrime Schemes Running Amid the Tokyo Olympics
Image sourced from T3. After an unprecedented year-long delay, the 2020 Tokyo Summer Olympics began in earnest last week. This time, all the events will take place with no spectators, which reduces physical risks – in terms of health and from a cybersecurity point of view (such as data theft using the vulnerabilities of public Wi-Fi at the stadium). However, sports enthusiasts should not forget that cybercriminals will aim to take advantage of fans’ eagerness to watch the Olympic Games by instigating various online fraud schemes. To get a better overview of how scammers are trying to monetise viewers’ interest, Kaspersky experts analysed Olympic-related phishing websites designed to steal users’ credentials. As a result, Kaspersky researchers found fake pages offering to stream various Oly...
WhatsApp Overwhelmingly Popular for Phishing Scammers, According to Kaspersky
Anonymised data, voluntarily provided by Kaspersky Internet Security for Android users, has shown which messenger apps are the most popular among phishing scammers. The biggest share of detected malicious links between December 2020 and May 2021 were overwhelmingly sent via WhatsApp (84.9%), followed by Telegram (5.7%). “Percentage of Phishing Detections by Messanger App.” Courtesy of Kaspersky. Viber is in third place with a share of 4.9% and Hangouts has less than 1%. Countries experiencing the highest number of phishing attacks were Russia (46%), Brazil (15%) and India (7%). Globally, 480 detections were recorded per day. Messenger Apps Surge in Popularity According to research, messenger apps outstripped social networks by 20% in 2020, in terms of popularity among users, and ...
Inside the Mind of Cybercriminals – How Threat Actors Think
Cybercriminals come in many different flavours, but the majority of them are in it for one thing: financial pay-off. They want the money that comes with offering their tools or services, selling stolen data, extortion like ransomware or plain fraud. And they all have one thing in common – your organisation is on their radar. This is why, says Anna Collard, SVP Content Strategy and Evangelist at KnowBe4 Africa, it is critical to understand how cyber criminals operate, the tools they use and the approaches they take to embed robust security within the organisation. “With ransomware going rampant and victim organisations paying up to millions of U.S. dollars to the extortionists, this problem is just going to get worse. The U.S. government recently announced that ransomware is a national cybe...
5 Crucial Things You Need to Do When You Receive A Phishing Email
Image sourced from Kaspersky. You may not even notice when you receive one, most suspicious emails are automatically sorted to spam by your email service – though, a few may slip through the cracks, and one or two may even be authentic enough for you to click through their contents. The most important thing to remember about phishing emails is that unless you open any attachments or click on any links, you will not be affected by malware. Phishing emails are based on social engineering and work off bait, hence the name, and unless the bait is taken you can’t be affected by the cybercriminals holding the rod, fingers twitching at the reel. If you’re not familiar with these kinds of emails or begin to feel nervous or panicked when you receive one – this list is for you. Here are 6 crucial th...
Beware of Scammers – 4 Tips to Spot Digital Banking Fraud
Sourced from Pure Cloud Solutions To prevent becoming the victim of fraudsters, it’s vital to be on guard, especially when using transactional, card-based accounts linked to cheque and savings accounts. Vijay Naidoo, CIO at Old Mutual Finance, pointed out that “…transactional accounts are among the most commonly used accounts, which means they are prime targets for scammers.” “Scammers are continually finding new ways to gain access to personal banking information and use it to defraud unsuspecting customers. So, banks need to continually upgrade their security systems, while consumers need to be informed and alert.” Phishing involves sending what appears to be an official email notification from an institution. If you open the message, malware is installed on your computer and account inf...