phishing attacks
Cross chains, beware! deBridge flags attempted phishing attack, suspects Lazarus Group
Cross-chain protocols and Web3 firms continue to be targeted by hacking groups as deBridge Finance unpacks a failed attack that bears the hallmarks of North Korea’s Lazarus Group hackers. deBridge Finance employees received what looked like another ordinary email from co-founder Alex Smirnov on a Friday afternoon. An attachment labeled ‘New Salary Adjustments’ was bound to pique interest, with various cryptocurrency firms instituting staff layoffs and pay cuts during the ongoing cryptocurrency winter. A handful of employees flagged the email and its attachment as suspicious, but one staff member took the bait and downloaded the PDF file. This would prove fortuitous, as the deBridge team worked on unpacking the attack vector sent from a spoof email address designed to mirror Smirnov’s. The ...
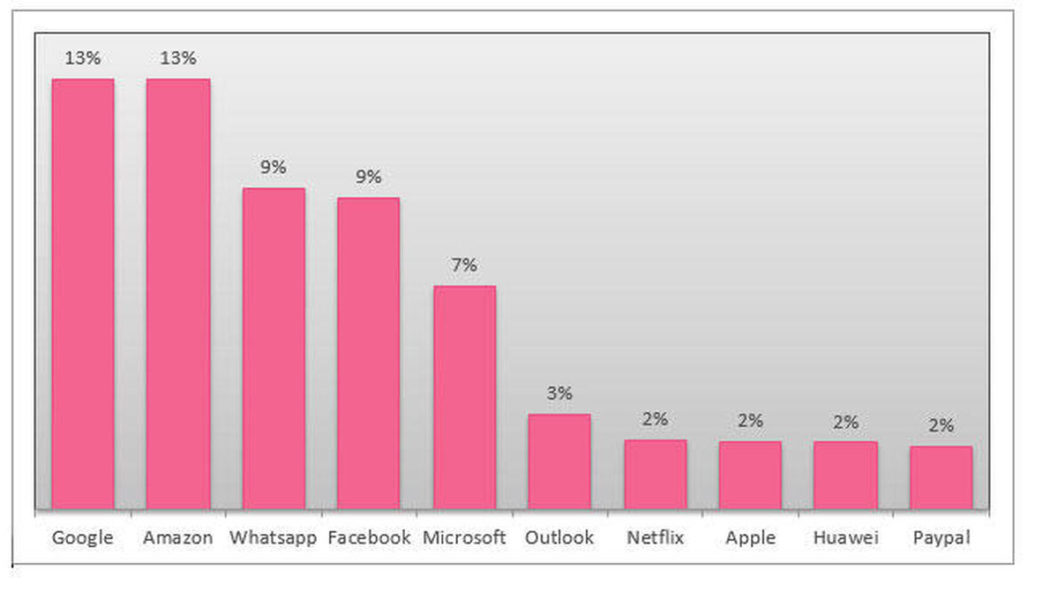
Digital Payments: Survey Reveals 35% South Africans Faced Phishing Scams
Image sourced from isnews.stir.ac.uk According to the Kaspersky Digital Payment survey, 35% of respondents from South Africa faced phishing scams when using online banking or mobile wallet services. 43% have personally encountered fake websites, and 59% experienced scams (via texts or calls) using social engineering. When asked about awareness of threats against digital payment methods, the majority of respondents from South Africa report that they are aware of both financial phishing attacks (94%) and online scams (95%). 78% also stated that they are informed about banking malware on PCs and on mobile. This type of malicious software steals money from users’ bank accounts. However, 98% think that banks and payment companies should educate users more about the threats online. When it comes...
Small Businesses in Kenya Face 47% Increase in Cyber Attacks
When a small business owner is faced with the responsibilities of production economics, financial reports, and marketing all at the same time, cybersecurity can often appear complicated and, at times, unnecessary. However, this disregard for IT security is being exploited by cybercriminals. Kaspersky researchers assessed the dynamics of attacks on small and medium-sized businesses between January and April 2022 and the same period in 2021, to identify which threats pose an increasing danger to entrepreneurs. In 2022, the number of Trojan-PSW (Password Stealing Ware) detections in Kenya increased by 16% when compared to the same period in 2021 – 12 639 detections in 2022 compared to 10 934 in 2021. Trojan-PSW is a malware that steals passwords, along with other account inform...
How to Stop the Costliest Internet Scams
Image sourced from isnews.stir.ac.uk According to Steve Flynn, Sales and Marketing Director at ESET Southern Africa, it’s long past time organisations get a handle on business email compromise scams which generated more losses for victims in 2021 than any other type of cybercrime. While ransomware, hacking, API hacks, and all the other cybersecurity threats make headlines, it’s worth remembering that the costliest internet scam is still business email compromises, according to the latest FBI Internet Crime Report. Among the complaints received by the FBI in 2021, ransomware, business e-mail compromise (BEC) schemes, and the criminal use of cryptocurrency are among the top incidents reported. Technology-based systems are under attack, and they cost organisations around the world billions in...
How Emails Can Cause Cybersecurity Vulnerabilities in Your Organisation
Sourced from International IDEA Since the start of the pandemic, many businesses have shifted to remote work. Cybercriminals saw the opportunity to target businesses’ remote users leaving unprepared businesses vulnerable to cyberattacks. Phishing attacks have become one of the most prominent data security problems for a number of businesses in South Africa. “Remote working increased organisation’s reliance on email, creating the perfect conditions for email fraud and phishing,” says Riaan de Villiers, Business Analyst at LAWtrust Information Security. In the Mimecast State of Email Security 2020 study, businesses in South Africa reported a 53% increase in phishing attempts and a 46% increase in incidences of impersonation fraud compared to previous years. Email is a common channel used for...
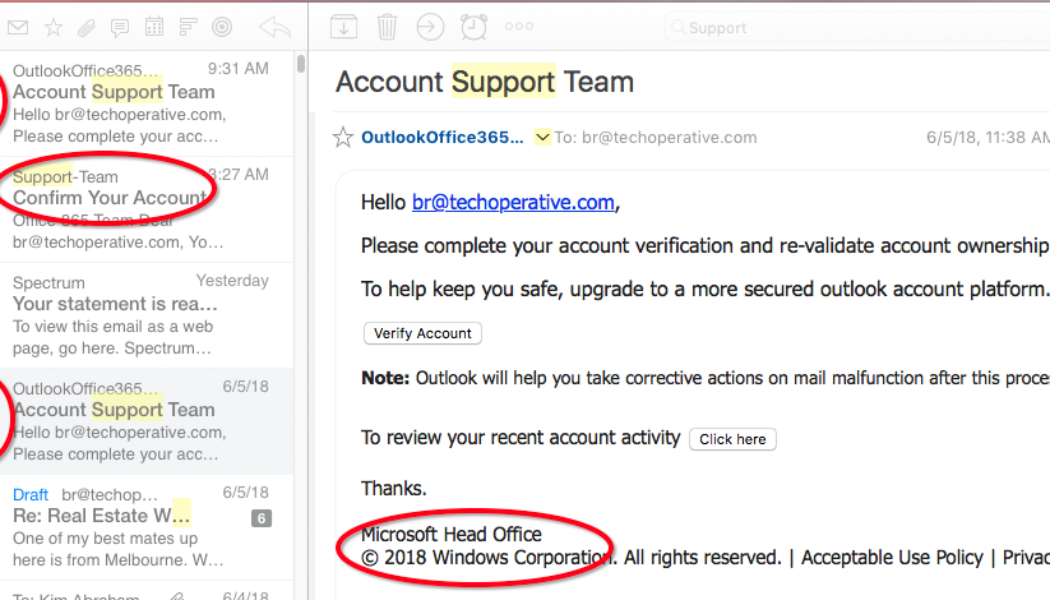
How to Be Safe From the “Reset Password” Email Scam
Image sourced form Broad Media Most online services have built-in security systems that alert employees when the systems detect “unusual” activity on their accounts. For example, legitimate email services or similar will send notifications about attempts to reset the phone number and e-mail address linked to the account, or the password. Of course, as soon as such messages became commonplace, enterprising cybercriminals tried to imitate this mechanism to attack corporate users. As cyberattacks rely on the human factor more often each year, and as cybersecurity technologies progress, such tricks are becoming more and more common and are being registered in multiple mailouts around the world. The scenario is usually as follows: if it’s a public online service attacker it will usually make ev...
- 1
- 2