online security
The Shift to Remote Working Has Led to Bad Online Security Habits
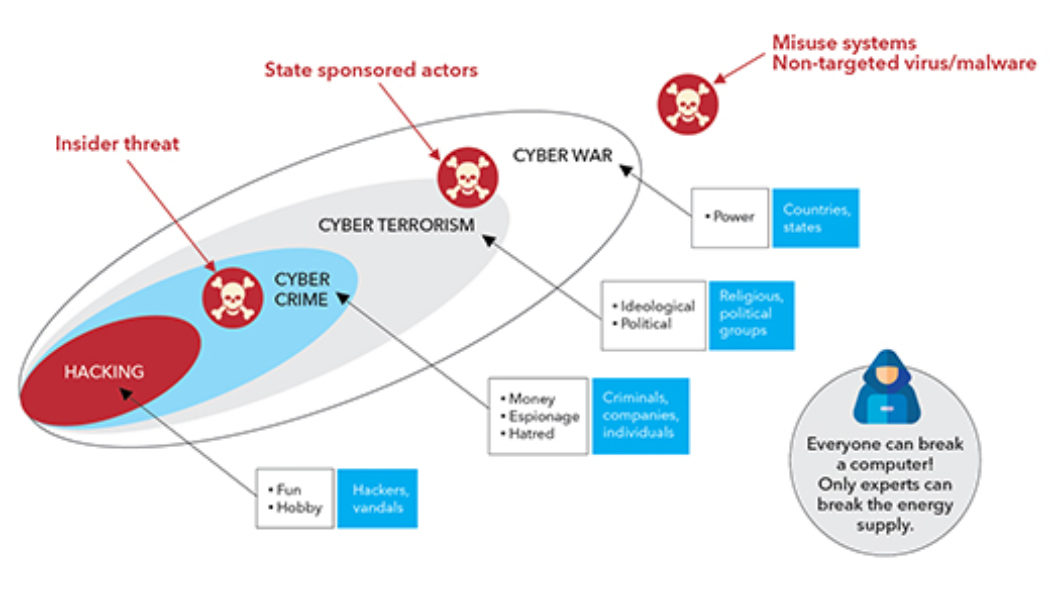
More than 50% of IT teams believe that employees have bad security habits. Habits they’ve developed since moving their offices into the home and that put their information, systems and employers at risk. The statistic comes from the Tessian Back to Work Security Behaviors Report that also found an age discrepancy when it came to who practised the best security from home. Around 51% of 16–24-year-olds and 46% of 25–34-year-olds reported that they used security workarounds, while two in five people said that the security behaviours they adopted at home were very different from those they used in the office. Training A Top Priority For Anna Collard, SVP Content Strategy & Evangelist at KnowBe4 AFRICA, this draws a thick red marker around the need to ensure that people and security trainin...
Is Cybersecurity as Necessary as Electricity?
Sourced from Travellers Cybersecurity has become as much a business necessity as having electricity says South African financial services and insurance company, Sanlam. Threat actors are constantly evolving and relentlessly hunting for vulnerabilities, cybercrime has become so profitable that exploitation is their business priority, and regulation is increasingly complex to navigate and manage. For Sanlam, cybersecurity has always been more than plugging holes and filling gaps, it’s a priority that has to be embedded within business foundations while managing cost, growth, customer experience, data analytics and regulatory controls. “Developing a comprehensive and holistic cybersecurity solution is a mandate for us, one that we must meet to ensure customer, stakeholder and industry trust. ...
Cyber Hygiene for System Health and Online Security
Organisations in the COVID-19 pandemic era have been forced to look at their security hygiene best practices in order to minimise risk, data leakage and non-compliance, while still allowing for operational flexibility and efficiency. Employees have increasingly been both allowed and encouraged to use their own devices to remotely connect to the corporate network. As a result, connectivity and digital resources at the office as well as the home have become more intertwined, meaning that minimising risk has become more critical than ever. Cyber hygiene refers to the practices and steps that companies need to take to maintain system health and improve online security. In my opinion, cyber hygiene has not changed significantly over the past year or two, but has just become more relevant to ap...
- 1
- 2