NU Africa
Double Bullseye for SentinelOne in Recent Prestigious Global Accolades
Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited Africa SentinelOne’s endpoint security solutions came out on top among endpoint vendors in the latest ATT&CK Evaluation performed by MITRE Engenuity. Having recently released its results from the 2020 evaluation, SentinelOne was proud to report that it was the only vendor to achieve complete visibility, with zero missed detections, across both Windows and Linux environments. In addition, SentinelOne was also proud to announce that it has recently been positioned by Gartner as a Leader in the 2021 Magic Quadrant for Endpoint Protection Platforms. SentinelOne believes the placement is a testament to the company’s innovative Singularity XDR platform and scaled go-to-market execution in record time. Over and ...
Digitally Protecting Your Intellectual Property Helps Safeguard Future Business Success
In today’s increasingly knowledge-based economies, intellectual property holds value because of its ability to generate future profits and wealth, as it fuels innovation and growth. Therefore, it is logical that companies need to take precautions to safeguard their intellectual property. One definition of intellectual property is as follows: “Law: property that results from original creative thought, as patents, copyright material, and trademarks, OR an individual product of original creative thought.” Protecting an intangible asset As can be seen from the above, whether it is a legal or non-legal definition, original creative thinking is an integral part of intellectual property, meaning that it is an intangible asset which can take many forms. Some of the most well-known forms of i...
Your Data has Left the Building: Don’t Let it Take You on a Bumpy Ride
“Ladies and gentlemen: Michael Jackson has left the stadium.” These are the dramatic words spoken just after Michael Jackson, one of the most famous performers and entertainers in history, flew off the stage at the end of his 1992 – 1993 ‘Dangerous’ tour. It was one of the smoothest and most awe-inspiring endings to a stadium performance the world had ever seen – and Jackson did it for concert after concert during that spectacular global tour. However, as was later revealed, the truth is that Michael Jackson didn’t actually fly out of any stadiums via a jetpack – it was a professional stuntman in his place. So, it wasn’t really correct to think that the King of Pop had left the building. But it surely is correct, nearly 30 years later, to know that your data has certainly left the bu...
Rubrik for Microsoft 365 Delivers Faster, Simpler Recoveries at Scale
Risna Steenkamp, General Manager: ESM Division at Networks Unlimited Africa It’s well known that Microsoft 365 – formerly known as Microsoft Office 365 – is one of the most widely used solutions for email, collaboration and document storage in large enterprises. At the same time, Microsoft doesn’t provide its own backup and restore offering, but instead encourages third-party vendors to provide their own solutions. Cloud data management company Rubrik places a focus on speed and simplicity of management in its backup and restore solution for Microsoft 365. Rubrik offers a policy-based SLA enforcement, and uses Microsoft Azure as the storage location for backups. Risna Steenkamp, General Manager: ESM Division at Networks Unlimited Africa, which distributes Rubrik throughout Afri...
Fixing Your Cybersecurity Issues 1 Next-Gen Firewall at a Time
Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited Africa When did you last check your firewalls as a barrier to entry against cybercriminals? And, perhaps more importantly: does your organisation still rely on a legacy firewall, or has it upgraded to a next-generation firewall (NGFW)? And have you considered the ‘Broken window’ principle when looking at your internal cybersecurity posture, in order to have a positive effect on your business processes? These questions are posed by Stefan van de Giessen: General Manager: Cybersecurity at Networks Unlimited Africa, who says, “The broken window theory rests on the idea that a neighbourhood or community that appears to be orderly and well-kept will be less susceptible to crime. Conversely, one that has many broken wind...
Combined Rubrik and IDC Report Addresses Data Sprawl in the Modern Enterprise
Image sourced from Gerd Altmann, Pixabay Data sprawl – referring to the fact that valuable data is now commonly spread across multiple physical locations and different repository types – is one of the most critical IT issues that a modern organisation will have to manage. Not only does this expanse of data create issues for an organisation around its effective use, it can also negatively affect its security measures. This is according to a recent report from IDC, the global market intelligence firm, and cloud data management company Rubrik, which commissioned the IDC White Paper study and which involved just over 800 respondents in North America, Western Europe and the Asia/Pacific region. The white paper reveals that: Companies are not leveraging data to its fullest extent, causing ...
In the Eye of the Storm: New Record is Set by Ten Million DDoS Attacks in One Year
Not all record-breaking numbers are feats or achievements towards which we all aspire. For example, in 2006, American teenager Matt Suter was destined to become the holder of the record for the ‘farthest distance thrown by a tornado and survived’, when he was flung, in an unconscious state, for a distance of almost 400 metres (398.37 metres) by an F2 tornado (meaning wind speeds of 181 to 253 kilometres per hour), yet later regained consciousness almost without a scratch. “We’ve recently had a very thought-provoking record-breaking number released for 2020 in the cybersecurity arena, and it’s not pretty,” says Risna Steenkamp, General Manager: ESM Division at value-added distributor Networks Unlimited. “Distributed denial of service (DDoS) attacks have crossed the 10 million mark dur...
How the ‘Broken Window’ Theory Affects Cybersecurity Matters
Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited Africa Here at Networks Unlimited Africa, we are applying the ‘broken window’ principle when looking at our internal cybersecurity posture and how it affects business processes. The term ‘Broken window’ comes from George Kelling, a criminologist, who wrote in 1982 that, “social psychologists and police officers tend to agree that if a window in a building is broken and is left unrepaired, all the rest of the windows will soon be broken… vandalism can occur anywhere once communal barriers…are lowered by actions that seem to signal that ‘no one cares’.” This theory had also been the subject of experiments previously (1969) by a professor at Stanford University, Philip Zimbardo. Zimbardo arranged to have a car w...
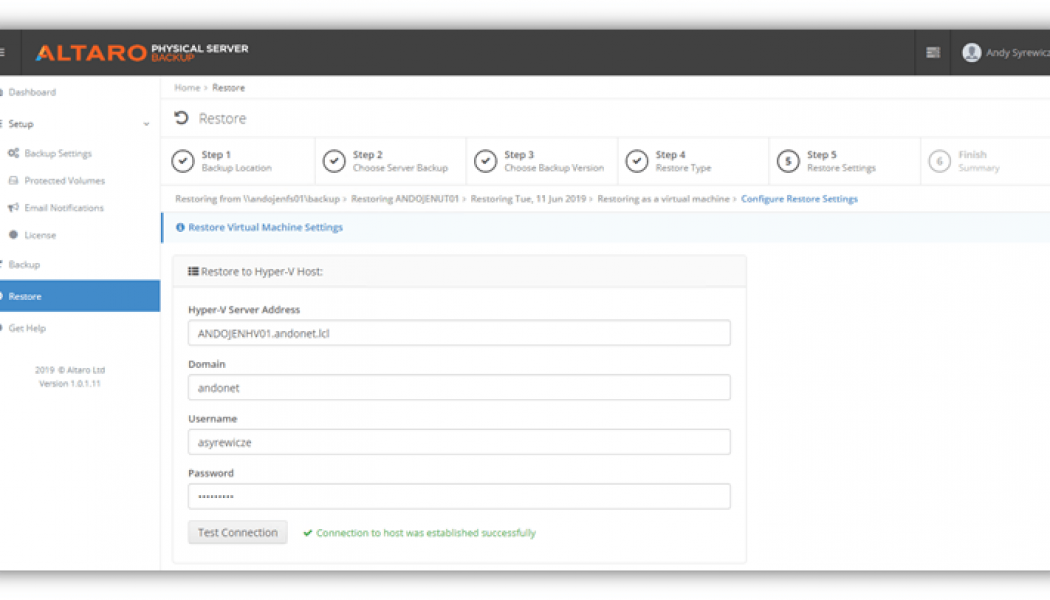
Backup the Physical Servers on your Network with Free Altaro Software
Risna Steenkamp, General Manager: ESM Division at Networks Unlimited Africa Companies and organisations with virtualised server environments often have physical machines too, and these also need data protection. Altaro has reacted to this need with the introduction of Altaro Physical Server Backup, a server backup software solution – with the added bonus that it’s free. Altaro is a leader in backup solutions for MSPs, IT resellers and IT departments, with its solutions distributed throughout Africa by value-added distributor Networks Unlimited Africa. Risna Steenkamp, General Manager: ESM Division at Networks Unlimited Africa, explains: “Businesses with virtual environments that have one or more physical machines or legacy servers that have not been virtualised can use Altaro P...
The Growing Role of SASE for Enterprises during 2021, and other top SD-WAN Predictions from Silver Peak
Marcel Fouché, Networking and Storage General Manager at Networks Unlimited Africa Silver Peak, the global SD-WAN leader that was recently acquired by Aruba, a Hewlett Packard Enterprise company, now has an even greater ability to help enterprises successfully transform their wide area network (WAN) and security architectures, and advance their digital transformation. This includes the ability for enterprises and their employees to connect to business applications from anywhere in a safe and secure manner. This is according to Silver Peak founder David Hughes, who writes in a blog entry that, “With so many exciting advancements in WAN edge technologies, including the acceleration of IoT adoption, advancements in automation and AI along with new transport technologies emerging, we’re contin...
DDoS ‘Tax’ Adds to an Organisation’s Attack Burden, says NETSCOUT
Risna Steenkamp, General Manager: ESM Division at Networks Unlimited Africa Did you ever think about the ‘tax’ you pay as an organisation in the event of a distributed denial of service (DDoS) attack? In a nutshell, DDoS attacks by threat actors don’t only have a negative effect on businesses and their customers – they also take up quantities of internet bandwidth without paying for it. This means that the cost of this traffic falls on the shoulders of every business that does pay for the internet service. This is according to the NETSCOUT ‘2020 1H Threat Intelligence Report’, in which NETSCOUT, a leading global provider of service assurance, security and business analytics, introduces its DDoS Attack Coefficient. The figure summarises the amount of DDoS traffic going through regional netw...
Networks Unlimited Africa brings Festive Season Cheer to Tembisa school
There is no doubt that it has been difficult for many local companies to survive in 2020. Imagine then how much more challenging it must have been for worthy causes like The Love Trust and its beneficiary, Nokuphila School in Tembisa, Midrand? This is the question asked by Anton Jacobsz, CEO at Networks Unlimited Africa, a leading value-added distributor within the Sub-Saharan African market. He explains, “The Love Trust is a South African non-profit educational organisation which has, to date, reached over 20,000 primary and secondary beneficiaries in disadvantaged communities. Because the lockdown period has made it even harder for non-profit organisations to stay afloat, our company has made a point of continuing to offer our support to this worthwhile organisation. A team from Ne...