Networks Unlimited
NETSCOUT Visibility is Enhanced by AWS Expanded Support for Virtual Private Cloud Traffic Mirroring
Risna Steenkamp, General Manager: ESM Division at Networks Unlimited Africa Amazon Web Services (AWS), the world’s largest provider of on-demand cloud computing platforms, has now expanded its Virtual Private Cloud (Amazon VPC) Traffic Mirroring to support additional select non-Nitro Elastic Compute Cloud (EC2) instance types. As a result of this expansion, NETSCOUT is enabled to provide end-to-end visibility for security and service assurance of even more applications and services that are used in AWS. NETSCOUT, a leading global provider of service assurance, security and business analytics, is distributed throughout Africa by Networks Unlimited. Risna Steenkamp, General Manager: ESM Division at value-added distributor Networks Unlimited, explains, “Nitro is the underlying pla...
Security and Service Assurance Must Rule Financial Services as Threat Actors Remain Relentless
Risna Steenkamp, General Manager: ESM Division at Networks Unlimited Africa The rise of the pandemic last year meant that corporates around the globe had to embrace a highly dispersed, virtualised environment to keep the wheels of business turning. This is now changing the way that banks need to move forward, with both their security as well as their service assurance. So says Darren Anstee, Chief Technology Officer for security at NETSCOUT, a leading global provider of service assurance, security and business analytics. He explains that, at the start of 2020, digital transformation in the financial services sector was already well underway, and the intervening year has only accelerated this transformation. Writing in a recent blog, he notes that, “The COVID-19 lockdown shut branches, forc...
Rubrik for Microsoft 365 Delivers Faster, Simpler Recoveries at Scale
Risna Steenkamp, General Manager: ESM Division at Networks Unlimited Africa It’s well known that Microsoft 365 – formerly known as Microsoft Office 365 – is one of the most widely used solutions for email, collaboration and document storage in large enterprises. At the same time, Microsoft doesn’t provide its own backup and restore offering, but instead encourages third-party vendors to provide their own solutions. Cloud data management company Rubrik places a focus on speed and simplicity of management in its backup and restore solution for Microsoft 365. Rubrik offers a policy-based SLA enforcement, and uses Microsoft Azure as the storage location for backups. Risna Steenkamp, General Manager: ESM Division at Networks Unlimited Africa, which distributes Rubrik throughout Afri...
Fixing Your Cybersecurity Issues 1 Next-Gen Firewall at a Time
Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited Africa When did you last check your firewalls as a barrier to entry against cybercriminals? And, perhaps more importantly: does your organisation still rely on a legacy firewall, or has it upgraded to a next-generation firewall (NGFW)? And have you considered the ‘Broken window’ principle when looking at your internal cybersecurity posture, in order to have a positive effect on your business processes? These questions are posed by Stefan van de Giessen: General Manager: Cybersecurity at Networks Unlimited Africa, who says, “The broken window theory rests on the idea that a neighbourhood or community that appears to be orderly and well-kept will be less susceptible to crime. Conversely, one that has many broken wind...
Combined Rubrik and IDC Report Addresses Data Sprawl in the Modern Enterprise
Image sourced from Gerd Altmann, Pixabay Data sprawl – referring to the fact that valuable data is now commonly spread across multiple physical locations and different repository types – is one of the most critical IT issues that a modern organisation will have to manage. Not only does this expanse of data create issues for an organisation around its effective use, it can also negatively affect its security measures. This is according to a recent report from IDC, the global market intelligence firm, and cloud data management company Rubrik, which commissioned the IDC White Paper study and which involved just over 800 respondents in North America, Western Europe and the Asia/Pacific region. The white paper reveals that: Companies are not leveraging data to its fullest extent, causing ...
Tintri Drives Intelligent Infrastructure so You Can Get Ready to ‘Let Go of the Wheel’
The concept of self-driving cars is controversial and tends to polarise opinion. At the heart of it is the idea that a car will be capable of the same split-second decision-making as a human – or even better – with the ultimate goal of creating accident-free roads. For a vehicle to be autonomous, it needs to be continuously aware of its surroundings: firstly, by identifying and classifying information, and then by acting on the information through the computer control of the vehicle. And for this to happen, artificial intelligence (AI) is required, it is a critical technology in the goal of realising autonomous driving. “One of the main premises of self-driving cars is the idea that autonomy equals safety,” says Michael Donaldson, Tintri Product Manager at value-added distributor Net...
In the Eye of the Storm: New Record is Set by Ten Million DDoS Attacks in One Year
Not all record-breaking numbers are feats or achievements towards which we all aspire. For example, in 2006, American teenager Matt Suter was destined to become the holder of the record for the ‘farthest distance thrown by a tornado and survived’, when he was flung, in an unconscious state, for a distance of almost 400 metres (398.37 metres) by an F2 tornado (meaning wind speeds of 181 to 253 kilometres per hour), yet later regained consciousness almost without a scratch. “We’ve recently had a very thought-provoking record-breaking number released for 2020 in the cybersecurity arena, and it’s not pretty,” says Risna Steenkamp, General Manager: ESM Division at value-added distributor Networks Unlimited. “Distributed denial of service (DDoS) attacks have crossed the 10 million mark dur...
Unpacking Intelligent Infrastructure in the Modern Data Centre
As the world’s largest IT companies realise the importance of ‘intelligent infrastructure’ in the modern data centre, the race is on between storage competitors to provide products and solutions that are actually truly intelligent, and not merely standard infrastructure. So says Marcel Fouché, Networking and Storage General Manager at value-added distributor Networks Unlimited Africa, which partners in South Africa with Tintri, a provider of intelligent infrastructure for virtualised and non-virtualised enterprise IT environments. He clarifies, “In order to get to grips with this challenging issue, Tintri recently held a free webcast to unpack the differences between intelligent and standard infrastructure, looking at the topic from the perspectives of the customer, the vendor and th...
NETSCOUT Proves it’s Ready to Take on Threat Actors
Risna Steenkamp, General Manager: ESM Division at Networks Unlimited Africa Midway through June, American citizens thought the country was experiencing the world’s biggest-ever distributed denial of service (DDoS) attack, which seemed to be taking down internet service providers, social media platforms, and online services from gaming to banking. It very quickly turned out that no such attack was underway at all, as reported by Forbes, but the most interesting point was that so many citizens in the world’s most technology-enabled Western country believed the story so quickly. “A DDoS attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of internet traffic,” explains Ris...
Networks Unlimited Africa Embraces the Power of Three with its Value Offering to Partners
Anton Jacobsz, Networks Unlimited CEO There is a mysterious alchemy about the number three. As the saying goes, ‘Good things come in threes’ – which is why Networks Unlimited Africa is embracing this ‘magic number’. “A triangle, with its three sides, is one of the most stable shapes that you will find, which is why it’s used in building bridges and other structures where supporting a lot of weight is required,” says Anton Jacobsz, CEO at this leading value-added distributor in the sub-Saharan Africa market. “In the world of colour, we find three primary colours that make up all the rest – red, yellow and blue. In sport, we invariably award medals to the top three competitors, while in photography and design, artists often work in the rule of thirds for perspective. And so here ...
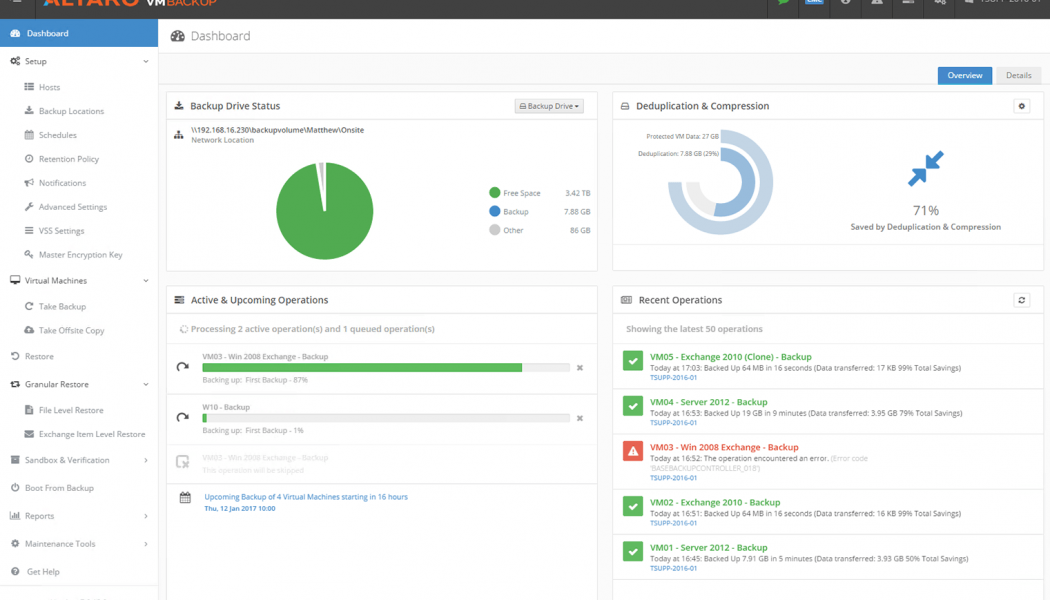
Altaro VM Backup: the Competitive Advantage
Anton Jacobsz, Networks Unlimited CEO Finding a reliable backup and replication solution for Hyper-V and VMware can be a difficult exercise. The partnership agreement between African value-added distributor, Networks Unlimited Africa, and Altaro, a leader in backup solutions for managed service providers (MSPs), IT resellers and IT departments, provides easy and affordable protection of Hyper-V and VMware virtualised environments. A virtual machine (VM) is a software computer that, like a physical computer, runs an operating system and applications. The virtual machine is comprised of a set of specification and configuration files and is backed by the physical resources of a host. VMware backup is the copying of data on a virtual machine in a V...