malware
Cybercrooks to ditch BTC as regulation and tracking improves: Kaspersky
Bitcoin (BTC) is forecasted to be a less enticing payment choice by cybercriminals as regulations and tracking technologies improve, thwarting their ability to safely move funds. Cybersecurity firm Kaspersky in a Nov. 22 report noted that ransomware negotiations and payments would rely less on Bitcoin as a transfer of value as an increase in digital asset regulations and tracking technologies will force cybercriminals to rotate away from Bitcoin and into other methods. As reported by Cointelegraph, ransomware payments using crypto topped $600 million in 2021 and some of the biggest heists such as the Colonial Pipeline attack demanded BTC as a ransom. Kaspersky also noted that crypto scams have increased along with the greater adoption of digital assets. However, it said that people have be...
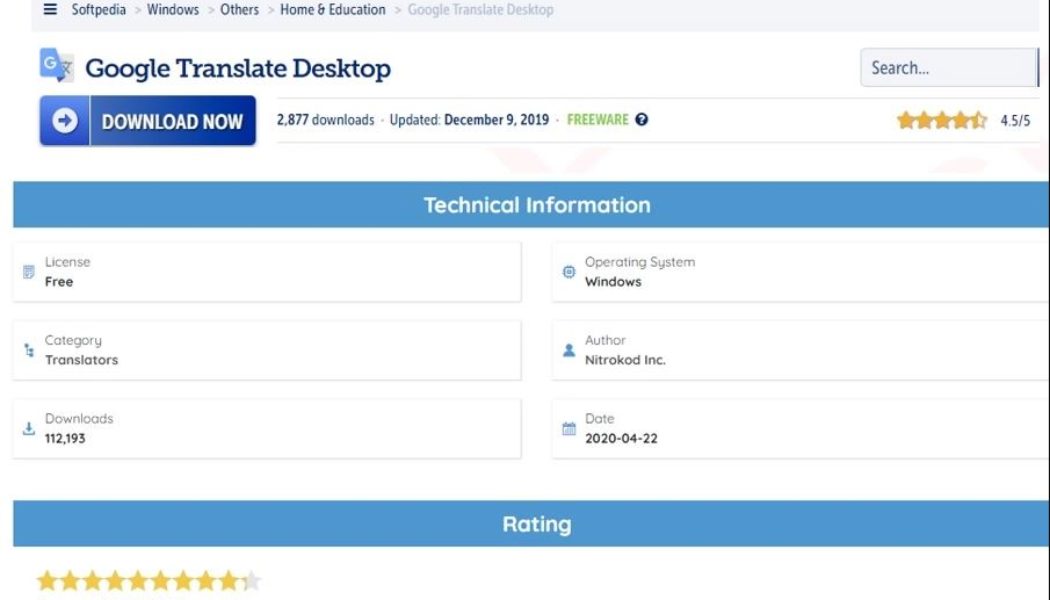
Sneaky fake Google Translate app installs crypto miner on 112,000 PCs
Crypto mining malware has been sneakily invading hundreds of thousands of computers around the world since 2019, often masquerading as legitimate programs such as Google Translate, new research has found. In an Aug. 29 report by Check Point Research (CPR), a research team for American-Israeli cybersecurity provider, Check Point Software Technologies revealed the malware has been flying under the radar for years, thanks partly to its insidious design which delays installing the crypto mining malware for weeks after the initial software download. .@_CPResearch_ detected a #crypto miner #malware campaign, which potentially infected thousands of machines worldwide. Dubbed ‘Nitrokod,” the attack was initially found by Check Point XDR. Get the details, here: https://t.co/MeaLP3nh97 #crypto...
Ransomware: The Threat that Lies in Wait
There can be no doubt that ransomware attacks are on the rise across the globe. A simple online search will reveal thousands of statistics in this regard, and South Africa is no exception. What is also clear from numerous examples of successful breaches, is the potentially devastating effect of a ransomware attack, which can cripple a business and shut down essential services for extended periods, not to mention cost a fortune to recover from. They are, in fact, legitimate business disasters, and need to be considered as such when it comes to disaster recovery and business continuity planning. Under Siege There is no shortage of high-profile examples of ransomware attacks in South Africa over the past two years, from Johannesburg City Power to the Life Healthcare hospital group, Transnet P...
How to Secure Your Remote Work Environment from Cybersecurity Threats
Sourced from International IDEA Cybersecurity threats are at an all-time high. With organizations increasingly employing hybrid work models, it has become more vital than ever to educate employees on the various cybersecurity risks that come with a distributed work environment. In a hybrid work environment, employees working from home pose a greater security risk compared to those working at the office. Home networks are less secured than corporate networks, unprotected by in-office firewalls and advanced fraud detection systems. In the comfort of one’s home, a small mistake by an employee could potentially risk the company’s confidential data being leaked. However, risks like data leaks and device compromise can be managed by following certain best practices. Here are some of the practice...
Understanding the Risks to Cryptocurrency Trading
Sourced from Hacker Noon. Alongside self-fertilizing crops and low-carbon shipping, cryptocurrencies have made the World Economic Forum (WEF) list of top tech trends in 2022 bolstered by research by the Thomson Reuters Foundation that describes it as moving from the ‘fringes of finance to the mainstream’. Perceptions around cryptocurrencies have shifted, with several countries adopting it as legal tender, banks looking to create their own forms of digital currency, and consumers putting their savings into crypto wallets instead of traditional financial institutions. Anna Collard, SVP Content Strategy & Evangelist at KnowBe4 Africa. Countries are either considering or are already partially using Central Bank Digital Currency (CBDC), which essentially allows for companies and individuals...
‘Less sophisticated’ malware is stealing millions: Chainalysis
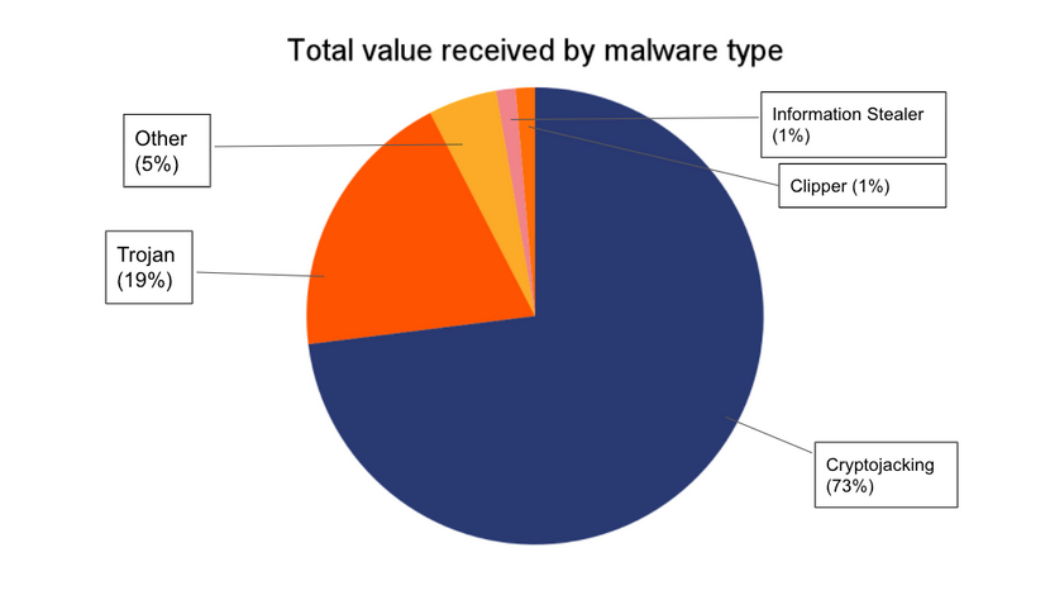
Cryptojacking accounted for 73% of the total value received by malware related addresses between 2017 and 2021, according to a new malware report from blockchain analysis firm Chainalysis. Malware is used to conduct nefarious activity on a victim’s device such as a smartphone or PC after being downloaded without the victim’s knowledge. Malware-powered crime can be anything from information-stealing to denial-of-service (DDoS) attacks or ad fraud on a grand scale. The report excluded ransomware, which involves an initial use of hacks and malware to leverage ransom payments from vicitms in order to halt the attacks. Chainalysis stated: “While most tend to focus on high-profile ransomware attacks against big corporations and government agencies, cybercriminals are using less sophisticated typ...
‘Less sophisticated’ malware is stealing millions: Chainalysis
Cryptojacking accounted for 73% of the total value received by malware related addresses between 2017 and 2021, according to a new malware report from blockchain analysis firm Chainalysis. Malware is used to conduct nefarious activity on a victim’s device such as a smartphone or PC after being downloaded without the victim’s knowledge. Malware-powered crime can be anything from information-stealing to denial-of-service (DDoS) attacks or ad fraud on a grand scale. The report excluded ransomware, which involves an initial use of hacks and malware to leverage ransom payments from vicitms in order to halt the attacks. Chainalysis stated: “While most tend to focus on high-profile ransomware attacks against big corporations and government agencies, cybercriminals are using less sophisticated typ...