Lists
From Owen to Wilshere, the Premier League’s Unfulfilled XI features the best players to never make it
The launch of the Premier League in 1992 sparked a wave of hype that has continued apace since then. While the self-styled ‘best division in the world’ clearly has plenty of attributes, it is debatable whether the excitement it generates is truly justified. One area where the propaganda machine has run riot is regarding players, with the last few decades littered with examples of someone being hailed as ‘the next big thing’. With many of those players failing to live up to expectations, we have assembled a Premier League Unfulfilled Potential XI. David James (GK) – Although James ended his career with two major trophies on his CV, it is impossible to look back on his playing days and think that he delivered what was expected of him. For starters, you don’t end up with the nickname ‘Calamit...
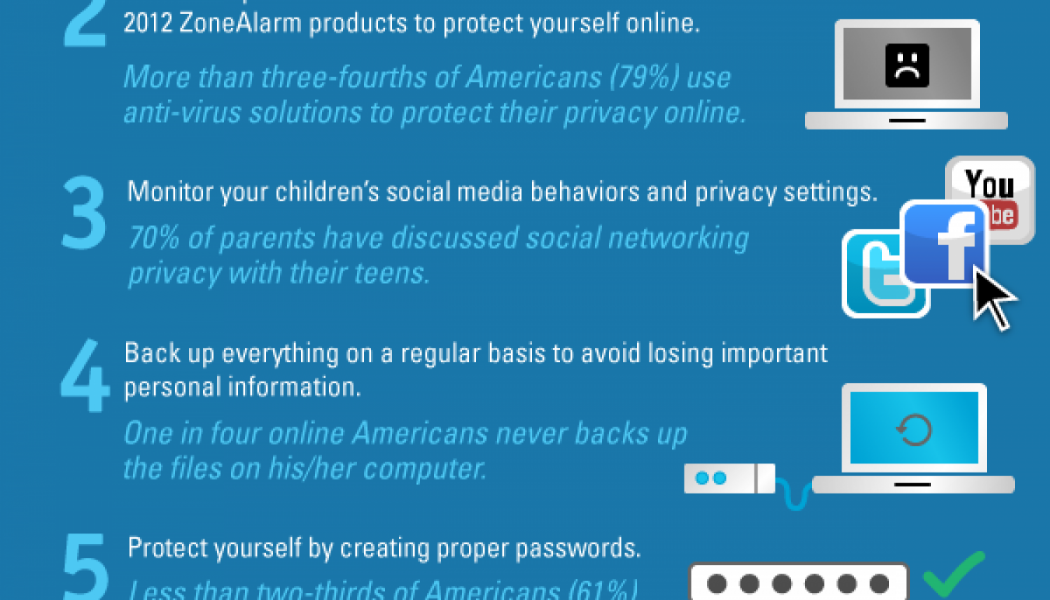
4 Tips to Protect Your Family Online
A recent survey revealed that 51.5% of South African children have been cyberbullied. “The reason for this is the increase in connected societies, more and more people are online, especially the youth,” says Simon Campbell-Young, co-founder and VP of global sales at Digimune. “There is clearly a lack of good cyber education and defensive tools. With this in mind, here are four tips to protect you and your family: 1. Remember that education is key This is the first awareness step. The vast majority of children have access to a wide variety of online devices — either shared or their own device — from a young age. By the age of 10, 30.5% of children have their own smartphone and 41.5% have access to a shared smartphone. It is thus imperative to take time to go about the internet – the good an...
10 Album Covers Worse Than Justin Bieber’s Justice
Justin Bieber’s new album, Justice, immediately caught people’s attention when it was first announced — not necessarily for the music it promised but for having a really terrible album cover. Along with Bieber’s painful attempt to edgily pose in a dim, green tunnel, as if he was the new Skins cast member, eagle-eyed music lovers also spotted the album font’s similarity to the band Justice’s logo. <img data-attachment-id="1114012" data-permalink="https://consequenceofsound.net/2021/03/justice-cease-and-desist-justin-bieber/justin-bieber-justice-logo-cease-and-desist/" data-orig-file="https://consequenceofsound.net/wp-content/uploads/2021/03/justin-bieber-justice-logo-cease-and-desist.jpg?quality=80" data-orig-size="1200,675" data-comments-opened=&q...
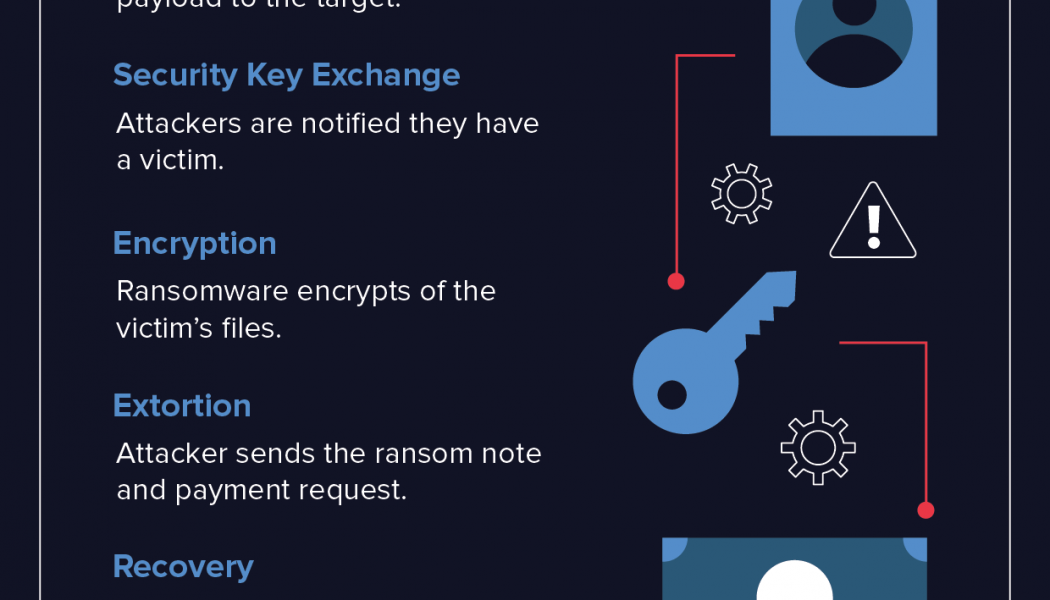
6 Ways to Create a Ransomware Mitigation Strategy
Ransomware attack trends continue to evolve, and the current iterations seen during the COVID-19 pandemic are no exception. During this time, malicious actors have attacked healthcare organisations, medical trials, schools, and shipping agencies. Considering the impact these modern attacks can have on organisations everywhere, no matter the industry, security professionals must always be ready to secure their systems, networks, and software in new ways. And according to a recent FortiGuard Labs global threat landscape report, ransomware remains a prolific threat that increased in 2020 and became even more disruptive. Mature cyber hygiene is key Attackers know that end-users are high-target, high-value assets. Ransomware leverages social engineering attacks, preying on fears as a way to exe...
10 Riot Grrrl Albums Every Music Fan Should Own
Editor’s Note: Crate Digging is a recurring feature in which we take a deep dive into a genre and turn up several albums all music fans should know about. This time, we celebrate Women’s History Month with a deep dig into the riot grrrl genre. Emerging from the deep forests of The Pacific Northwest, riot grrrl was a rasping rallying cry at a time when gender norms weighed heavily on the mosh pits and politics imposed itself dangerously on ovaries and queerness. With punk legends like Patti Smith and The Slits preceding them, the emerging DIY feminist punk movement of the ’90s brought with it grievances of the third wavers. Faced with no space in the existing punk-rock scene, attention was turned to tackling sexism and carving out a new underground alternative. A movement of rioting gi...
5 Cybersecurity Tips for Startups
Sourced from International IDEA From 2020 being dubbed ‘the year of the side hustle’ to small businesses grappling to maintain continuity and profitability, despite these unprecedented times there has been a significant uprising in entrepreneurial activity the world over. Startups tend to be created by people who burn with an idea and want to put it into action as soon as possible. Money is usually tight, and expenses run high, what with product development, promotion, and all the rest of it. When managing priorities, emerging businesspeople often neglect matters related to information security. Many startups try to save on security, confident that a small company with limited resources holds no interest for cybercriminals. The truth is anyone can fall victim to cybercrime. Firstly, becaus...
4 Trends Expected to Reshape Mobile Gaming in 2021
Mobile gaming has come into its own over the past few years. Analysts say the gaming industry generated $85 billion in value in 2020, while an estimated 2.5 billion people play games on mobile devices. Advances in technology also mean mobile games are increasingly able to compete with the visual fidelity of their console and PC cousins. Market researchers believe there are at least 11 million gamers in South Africa and forecast strong growth due to the increasing youth population. There is a clear trend towards social and mobile gaming, with the free-to-play revenue model dominating the market. However, we are also seeing more console-like experiences emerge on mobile devices as games like Fortnite and PUBG take off among smartphone and tablet gamers. Here are four reasons to expect mobile...
5 House Objects Cybercriminals could Use to Spy on You
It is estimated that there are more 22 billion devices linked to a home internet connection around the world, and research suggests this figure could reach 38.6 billion by 2025. While hyper-connectivity offers countless benefits, it also increases the number of available attack points to hackers and invisible intruders. Check Point research warns that there are five household objects that are being targeted by cybercriminals to spy on individuals in their own home. “Mobile phones, Smart TVs, computers and toys are just some of the devices being targeted. The number of products that feature a camera or microphone is growing every day, which can become an issue if they are connected to the internet and do not have the necessary security measures in place,” says Eusebio Nieva, Technical Direc...
10 Artists Worth Bringing Back VH1 Storytellers For
Kendrick Lamar photo by Amy Price; St. Vincent photo by David Brendan Hall; Janelle Monáe photo by Philip Cosores VH1 Storytellers was such a cool show. It borrowed the idea of MTV Unplugged — a hugely popular act performing a stripped-down set in front of an intimate audience — and took it one step further. Audiences could see and hear artists in a more relaxed setting, dishing on their careers and telling stories about creating the songs we know and love. Storytellers first aired 25 years ago in late February 1996; Kinks mastermind Ray Davies was the first performer. It ran for 97 more episodes, the last starring Ed Sheeran in 2015. In between, there was a veritable Who’s Who of talent, from classic rock gods like David Bowie and Crosby, Stills, Nash & Young to ‘90s stars like Pearl ...
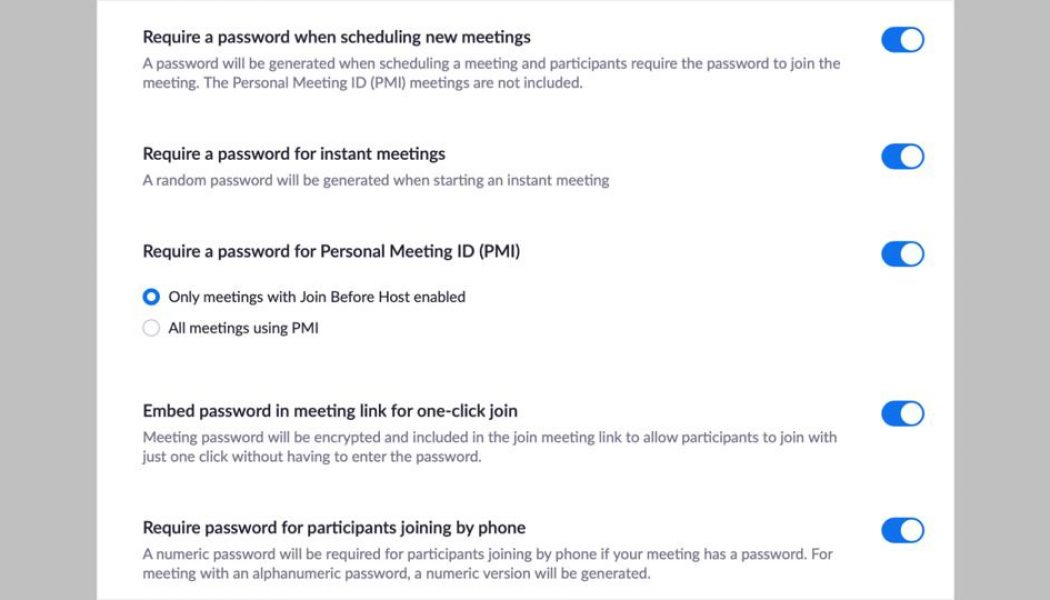
5 Surprisingly Simple Ways to Keep Hackers Out of Your Zoom Call
The COVID-19 remote work exodus has seen billions of people working from home, which means video conferencing apps have exploded in popularity. At the forefront is the service Zoom. However, with Zoom’s explosive popularity came a series of highly publicized security issues. To unpack this, ITNA’s Jenna Delport chatted with Gabe Goldhirsh, VP MEA at digital risk protection company, ZeroFOX. According to Goldhirsh, Zoom administrators are responsible for establishing security parameters that affect internal employees as well as any external parties that may join the organization’s Zoom meetings. Here are five ways to keep users safe and hackers out: Enable password requirements for ALL remote meetings whenever possible within the tool. Password enforcement at the administrati...
3 Reasons Data Management can Unlock the Value of Healthcare Data
Data in the healthcare sector is heavily regulated, with numerous laws and regulations governing how data needs to be processed, protected and retained. This has become more important than ever in light of the COVID-19 crisis, which has made healthcare data an increasingly attractive target for cybercrime. However, the pandemic has also highlighted the need to be able to analyse and share data effectively, as the world strives for improved treatment protocols and ideally an effective and safe vaccination. Data management has become a critical tool to unlocking the value of healthcare data, during the pandemic and beyond. Here are three ways effective data management can provide value: /* custom css */ .tdi_3_0c4.td-a-rec-img{ text-align: left; }.tdi_3_0c4.td-a-rec-img img{ margin: 0 auto 0...
4 Ways to Use Your Smartphone Better
Sourced from Getty Images. Smartphones are glued to the palm of our hands for most of the day, perhaps to keep up with the latest social media updates or to keep in contact with family, friends and even clients. Whatever the reason may be, smartphones are here and, let’s be honest, we probably wouldn’t survive a day without them. With this in mind, here are four ways to make the most of your screen time: 1. Record important information When it comes to remembering things, it often goes in one ear and out the other – despite our best efforts. To make sure that you remember important dates, meetings, or other events, use your phone’s calendar. Most of them will allow you to sync with your email calendar, which means that there’s no excuse for forgetting. /* custom css */ .tdi_3_7c6.td-a...