lazarus group
North Korea’s Lazarus behind years of crypto hacks in Japan: Police
Japan’s national police have pinned North Korean hacking group, Lazarus, as the organization behind several years of crypto-related cyber attacks. In the public advisory statement sent out on Oct. 14, Japan’s National Police Agency (NPA) and Financial Services Agency (FSA) sent a warning to the country’s crypto-asset businesses, asking them to stay vigilant of “phishing” attacks by the hacking groupaimed at stealing crypto assets. The advisory statement is known as “public attribution,” and according to local reports, is the fifth time in history that the government has issued such a warning. The statement warns that the hacking group uses social engineering to orchestrate phishing attacks — impersonating executives of a target company to try and bait employees into click...
Ronin hackers transferred stolen funds from ETH to BTC and used sanctioned mixers
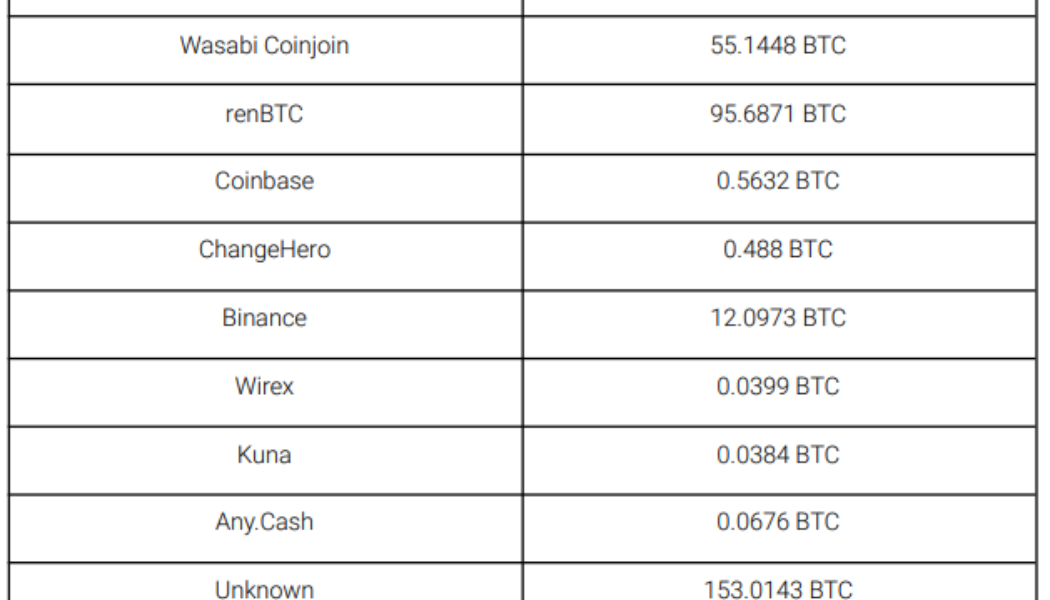
The hackers behind the $625 million Ronin bridge attack in March have since transferred most of their funds from Ether (ETH) into Bitcoin (BTC) using renBTC and Bitcoin privacy tools Blender and ChipMixer. The hacker’s activity has been tracked by on-chain investigator ₿liteZero, who works for SlowMist and contributed to the company’s 2022 Mid-Year Blockchain Security report. They outlined the transaction pathway of the stolen funds since the March 23 attack. The majority of the stolen funds were originally converted into ETH and sent to now sanctioned Ethereum crypto mixer Tornado Cash before being bridged over to the Bitcoin network and converted into BTC via the Ren protocol. I’ve been tracking the stolen funds on Ronin Bridge.I’ve noticed that Ronin hackers have trans...
Cross chains, beware! deBridge flags attempted phishing attack, suspects Lazarus Group
Cross-chain protocols and Web3 firms continue to be targeted by hacking groups as deBridge Finance unpacks a failed attack that bears the hallmarks of North Korea’s Lazarus Group hackers. deBridge Finance employees received what looked like another ordinary email from co-founder Alex Smirnov on a Friday afternoon. An attachment labeled ‘New Salary Adjustments’ was bound to pique interest, with various cryptocurrency firms instituting staff layoffs and pay cuts during the ongoing cryptocurrency winter. A handful of employees flagged the email and its attachment as suspicious, but one staff member took the bait and downloaded the PDF file. This would prove fortuitous, as the deBridge team worked on unpacking the attack vector sent from a spoof email address designed to mirror Smirnov’s. The ...