latest tech news
The First-Ever Images of the Black Hole at the Centre of Our Galaxy
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
Julie Snell of the Scotland 5G Centre Joins This Expert Line-up of Speakers at the #DTF2022
Julie Snell, Chair of the Scotland 5G Centre, is set to speak at the upcoming Digital Transformation Forum 2022 held in Sandton, Johannesburg, South Africa on 31 May 2022 at the Maslow Hotel. Julie Snell, Chair of the Scotland 5G Centre, is set to speak at the upcoming Digital Transformation Forum 2022 held in Sandton, Johannesburg, South Africa on 31 May 2022 at the Maslow Hotel. This hybrid event will see industry experts come together to tackle ideas on how to navigate the future-of-work, future-of-integration, connected digital experience, data management, and digital innovation strategies all in efforts to prepare your business for its successful digital transformation journey. Snell has 35+ years of experience as a business leader having successfully established new technology market...
Why Every Business Needs Data to Drive Recruitment & Talent-Retention
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
SA’s Zapper Launches Tap-On-Phone Payments
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
How Hackers Get Your Passwords & How to Defend Yourself
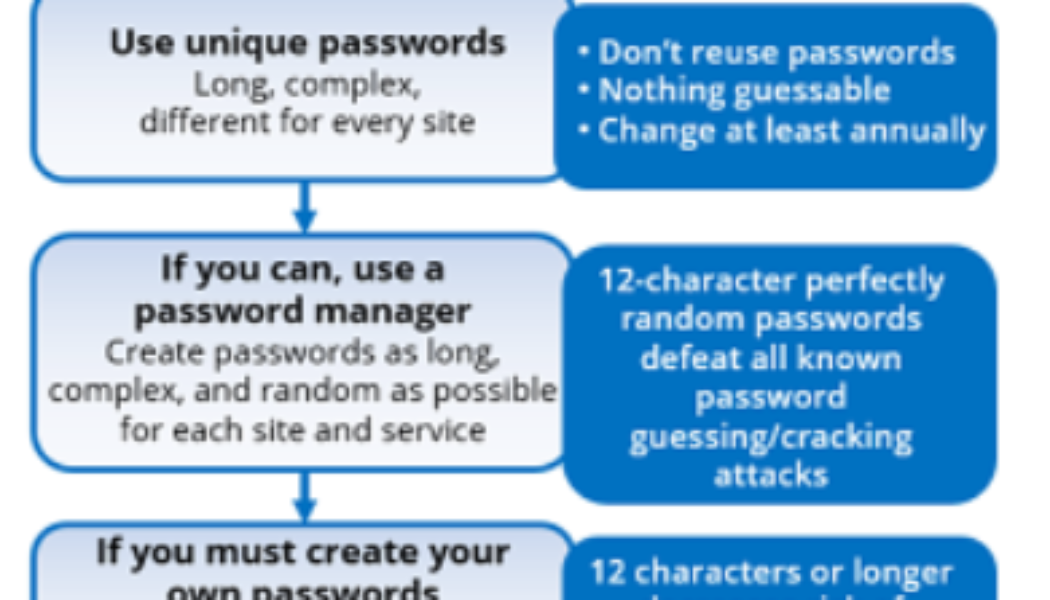
Sourced from Travellers Despite the world’s best efforts to get everyone off passwords and onto something else (e.g., MFA, passwordless authentication, biometrics, zero trust, etc.) for decades, passwords have pervasively persisted. Today, nearly everyone has multiple forms of MFA for different applications and websites AND many, many passwords. The average person has somewhere between three to seven unique passwords that they share among over 170 websites and services. And, unfortunately, those passwords often get stolen or guessed. This is why I recommend the following password policy guide: Most computer security experts agree with these policy recommendations, but more than a few readers might be shaking their heads, especially at the recommendations to use 20+ character passwords/pass...
Which African Country Will Adopt Bitcoin as Legal Tender Next?
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
Omnis Security from NETSCOUT: Protect Your Network from the Threats You Can’t See
On 09 December 2021, the world was alerted to the Log4j vulnerability [CVE-2021-44228 aka Log4Shell]. It is likely that threat actors already knew about the vulnerability before this date, says Tom Bienkowski, NETSCOUT Product Marketing Director, because it’s been reported that the vulnerability had been exposed much earlier in Minecraft chat forums. How does Log4j work – and what lessons does it bring? Log4j, which is open-source software provided by the Apache Software Foundation, records errors and routine system operations and sends diagnostic messages about them to system administrators and users. A common example of Log4j is when a user types in or clicks on a bad weblink and they receive a 404 error message. The web server running the domain of the attempted weblink sends a message ...