IT News Africa
How Hybrid Working Has Helped Female Office Employees
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
Why Women Are Underrepresented in Cybersecurity
Sourced from Women in Tech Africa. One of the industries struggling with significant bias and gender stereotypes is cybersecurity. This field plays an increasingly crucial role in our digital world and, as a result, offers many fulfilling career paths and opportunities. However, there are still significant barriers and misperceptions driving the belief that a career in cybersecurity is not for women. While women have been disproportionately impacted by pandemic-driven unemployment (for example, one in four women reported job loss due to a lack of childcare—twice the rate of men), the technology sector was less affected. This was mainly due to their being better prepared to pivot to remote work and flexible work models. As a result, according to a report by Deloitte Global, l...
OT Security – Everything You Need To Know
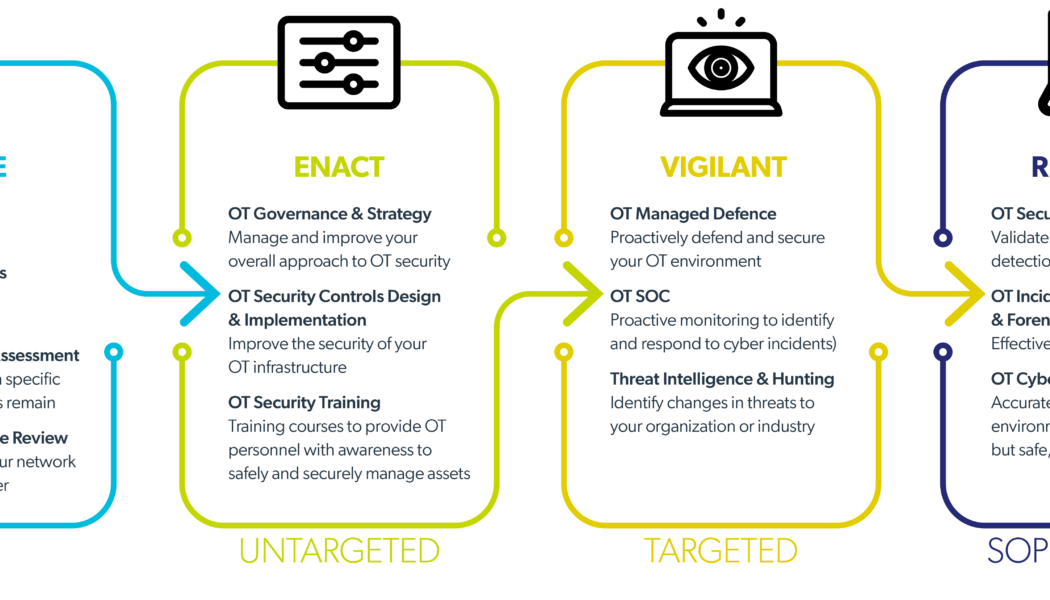
Image sourced from Twitter: @SmartIndustryUS Most enterprises know that cyberattacks in the information security realm are continuously growing in sophistication, severity and number. However, up until now, many organisations that run plants, factories, pipelines and other infrastructure have paid less attention to the threats they face in the realm of operational technology (OT). Recent global, OT-focused cyberattacks highlight why South African utilities, manufacturers, oil & gas companies and other organisations that run industrial infrastructure would be wise to take note of the growing range of cyber threats faced by their OT systems and infrastructures. In one example, an intruder breached a water treatment plant in Florida in the US. The attacker briefly increased the quantity o...
MiRO Announced as Virtual Exhibitor at #IoTFA2022
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.