Internet of Things
Cyber-attacks and OT – safeguard this new feeding ground
Johan Potgieter, cluster industrial software leader at Schneider Electric Before the advent of Industrial Internet of Things (IIoT), Operation Technology (OT) was safeguarded against most cyberattacks. OT systems’ propriety nature, standards and hard-wired connectivity protected it against malicious attacks. Cyber threats and incidents are a major operating and business risk for every digital enterprise. In age the of digitisation, creating and executing a strategy that allows you to see, reduce, and respond to cyber threats and risks is critical for achieving your financial objectives. Now, we’re entering unchartered waters – the widespread integration of embedded devices and OT networks with corporate or IT infrastructure has created a new feeding ground for hackers. Every en...
Internet of Vehicles (IoV) – The Cutting Edge of Vehicle Automation?
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
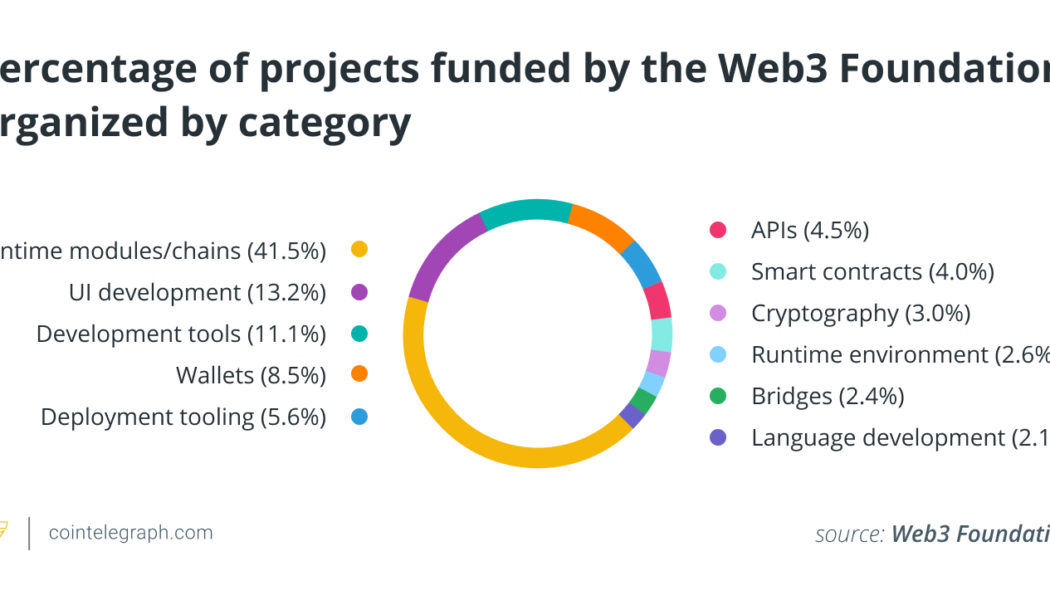
How adoption of a decentralized internet can improve digital ownership
Known as Web2, the current iteration of the internet emphasizes creating and distributing user-generated content. Websites like YouTube, social media apps like Instagram and Twitter, news sites, personal blogs and more make up a large part of the internet. Web2 is a step up from Web1, which was mainly a read-only web version filled with simple static websites. Web3 aims to bring decentralization and token-based economies to the internet. Web2 versus Web3 The development of several different web protocols at the beginning of the twenty-first century made it possible for programs and content to be linked via read-and-write interactions. Web2, in its present form, enables users to consume material created by other users and create their own content. Readers are probably best acquainted Web2. ...
How Smart Will Tomorrow’s Homes Be?
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
Little by little, blockchain technology is beginning to appear around the house
Blockchain technology is familiar to cryptocurrency users and national banks, and awareness of it is spreading fast to gamers. Applications in industry, particularly supply chain management, have been appearing as well. Through them, blockchain technology may improve domestic life in unseen ways, such as ensuring high-quality food, responsibly sourced seafood, or preventing the counterfeiting of pharmaceuticals. Nonetheless, the home may be blockchain’s final frontier. Blockchain penetration at the household level is so far quite low, but day-to-day utility was no afterthought for blockchain developers. Christoph Jentzsch, Simon Jentzsch and Stephan Tual, who in 2016 created The DAO — the short-lived first decentralized autonomous organization (DAO) — introduced Slock.it, “the first ...
AB4IR’s Kelebogile Molopyane to Speak on Bridging the Digital Divide Through Incubation at IoTFA 2022
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
Zoho Officially Announced as Platinum Sponsor for IoT Forum Africa 2022
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.