Fortinet
iOCO Offers Africa-Focused SD-WAN Solution to IT Landscape
Brett van Rensburg, Sales Director for iOCO’s Compute Division After a year-long due diligence process, EOH, a JSE-listed technology services firm, through its IT services company, iOCO, has chosen to extend its partnership with Fortinet, a global leader in broad, integrated and automated cybersecurity solutions, in order to offer its software-defined wide-area networking (SD-WAN) solution to the southern African market. As explained by Fortinet, an SD-WAN solution connects users to any application wherever it resides, from the data centre to the cloud. SD-WAN intelligently determines which path best meets the ideal performance needs for a specific application. It then routes the traffic through to the best WAN path, whereas traditional WAN architectures only have the ability t...
Networks Unlimited Wins 2 Channel Awards at Fortinet Africa Virtual Security Day
Networks Unlimited Africa, a leading value-added distributor operating within sub-Saharan Africa, received two awards, namely the Technical Support Distributor of the Year: Southern Africa award and the DLB Growth Distributor of the Year: East Africa award at the recent Fortinet Africa Virtual Security Day. This was the first time that the event took place via a virtual platform, due to the current restrictions around the global COVID-19 pandemic. The online nature of the awards ceremony also ensured that this broadened its reach to other parts of Africa, and not only within South Africa. Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited Africa, comments, “We have proudly maintained our business partnership with Fortinet, a global leader in broad, integrated and a...
T-Systems and Fortinet to Launch Cyber Security Academy in South Africa
T-Systems and Fortinet have teamed up to launch a Cyber Security Academy that’s accessible to local South African youth. The new Academy is expected to include Fortinet’s Network Security Expert (NSE) certifications, helping participants build cybersecurity awareness skills and ultimately tackle the global cybersecurity workforce shortage. “Cybersecurity has become a top C-level priority across the globe with skills in high demand. With the addition of this focus to our ICT Academy, we are empowering participants with new skills that will make them even more employable,” explains Marcus Karuppan, ICT Academy Manager at T-Systems South Africa. “T-Systems has been a Fortinet partner for many years. Building on our relationship, we are now collaborating with them to focus on cybersecurity ski...
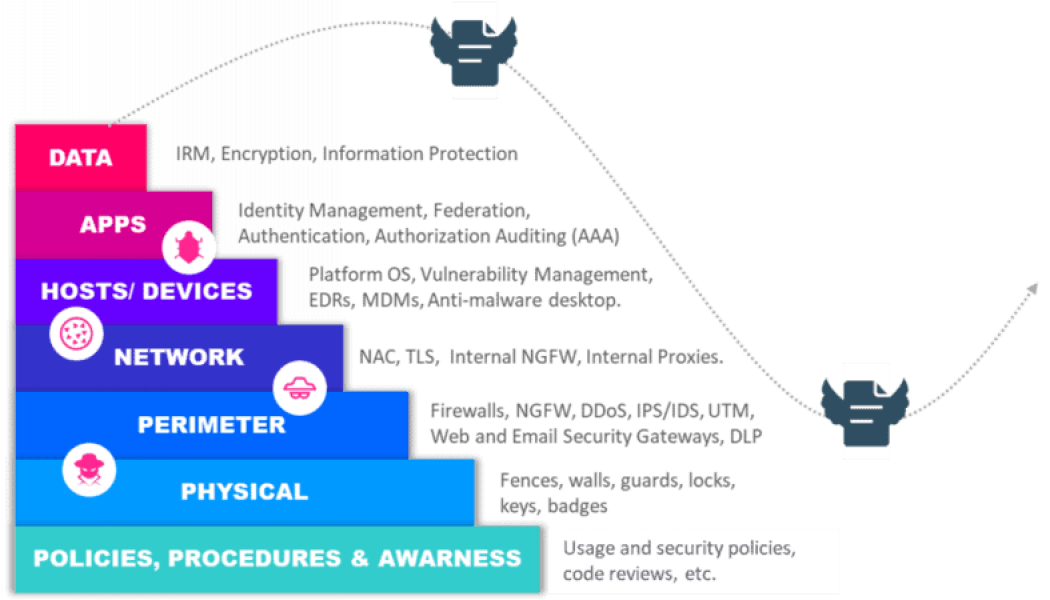
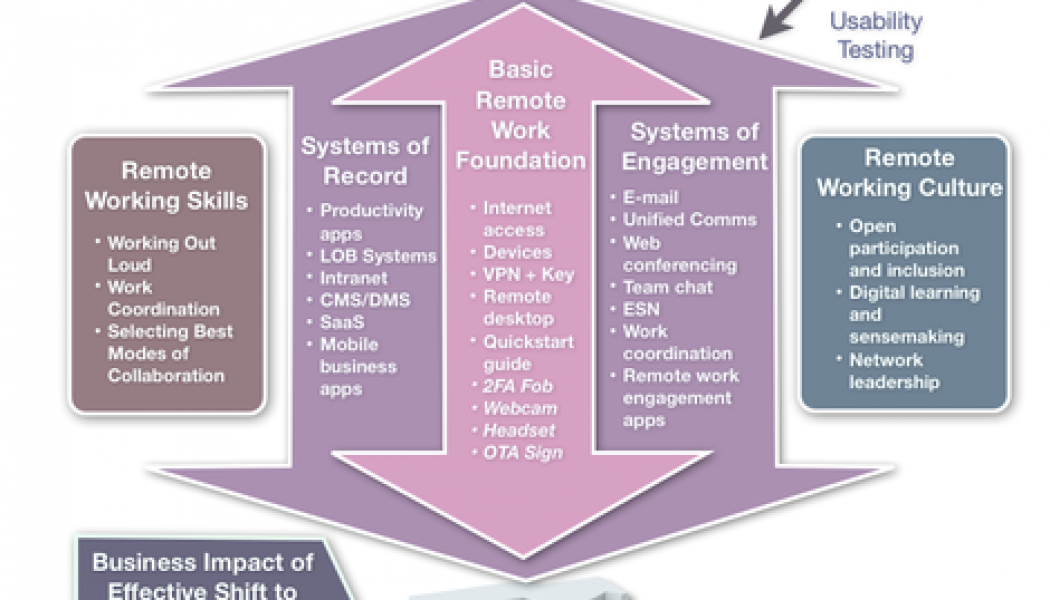
How Using Cloud Can Increase Security for Remote Working During the Pandemic
Sourced from Tapscape The cloud can enable organisations to quickly scale out enhanced security to a suddenly remote workforce, as part of efforts to ensure business continuity and disaster recovery – this is according to Patrick Grillo, Senior Director and Solutions Marketing at Fortinet. The pandemic had created unique challenges for employers and employees across all sectors around the world, with Varun Kukreja, Senior Program Manager – IT Security MEA, IDC Middle East, Africa, & Turkey, saying securing the teleworker had become a top priority, with some 90% of organisations looking to provide staff with secure access to IT services and applications. The pandemic had also accelerated digital transformation, he says, with an IDC Meta survey interim results revealing that some 56% of ...
- 1
- 2