Enterprise IT
First Digital Helps Clients Deliver Projects Seamlessly during COVID-19
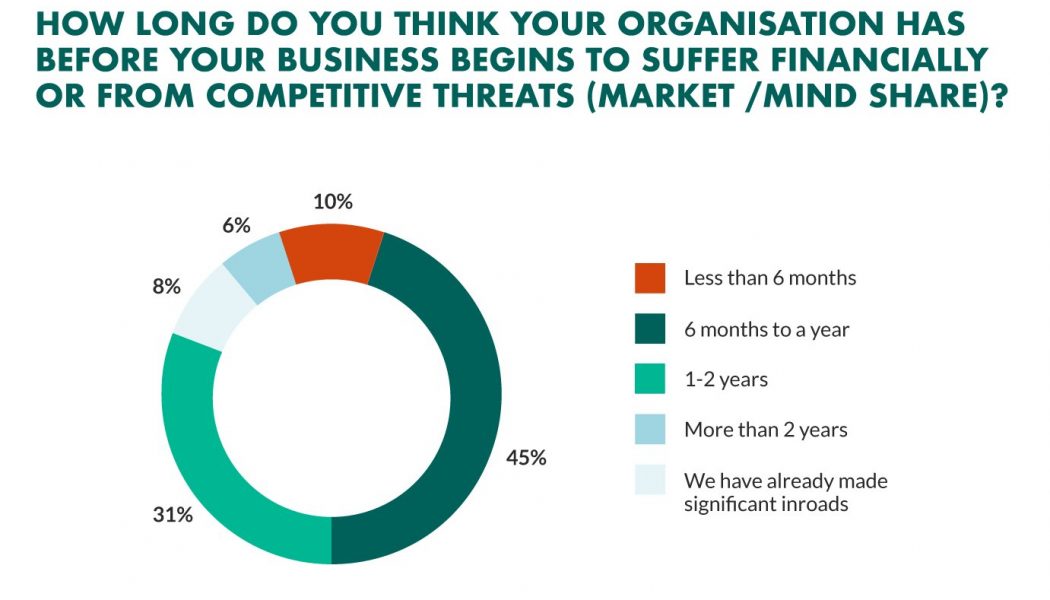
South Africa’s working culture ‘cage’ was well and truly rattled earlier this year when, due to the COVID-19 hard lockdown, companies were faced with little choice but to adapt to remote working… or suffer the consequences. “Suddenly, working from home became the only option to maintain a revenue stream,” explains Niel Steyn, division business owner – innovation at First Technology Digital, South Africa’s preferred partner for digital transformation, software consultancy and management consulting solutions and a First Technology Group company. “One of my favourite figures of speech is ‘Every cloud has a silver lining’, and during the pandemic, finding the silver linings within the chaos and fear was arguably even more critical than during regular day-to-day life.” “Looking at the situation...
Cyber Hygiene for System Health and Online Security
Organisations in the COVID-19 pandemic era have been forced to look at their security hygiene best practices in order to minimise risk, data leakage and non-compliance, while still allowing for operational flexibility and efficiency. Employees have increasingly been both allowed and encouraged to use their own devices to remotely connect to the corporate network. As a result, connectivity and digital resources at the office as well as the home have become more intertwined, meaning that minimising risk has become more critical than ever. Cyber hygiene refers to the practices and steps that companies need to take to maintain system health and improve online security. In my opinion, cyber hygiene has not changed significantly over the past year or two, but has just become more relevant to ap...
Altron People Solutions Partners with LivePerson to Deliver AI-powered Messaging for Better Customer Experiences
Altron People Solutions, a subsidiary of JSE-listed technology company Altron, was recently named as a Preferred Partner of LivePerson, a global leader in Conversational AI. The partnership will deliver AI-driven conversational experience solutions to the South African market and help companies pivot their businesses away from traditional voice-based channels to digital messaging channels. “The Altron People Solutions-LivePerson partnership is setting the bar when it comes to conversational experiences. South African brands can now leverage AI-powered bots to answer consumer messages alongside human customer service employees; we refer to this the Human-AI Tango,” says Darryl Marcus, head of business development and CX enabling technologies. “The devastating impact of the COVID-19 p...
Insult added to Injury as DDoS Extortion Attacker Impersonates well-known Threat Actors
Extortion and robbery while wearing a disguise are not new crimes in human history, but a threat actor has recently taken this into the online arena on the global stage, using distributed denial of service (DDoS) as the weapon, while pretending to be someone else. This is as reported in a recent threat advisory released by NETSCOUT’s ASERT division (ATLAS Security Engineering & Response Team), which is tasked with providing threat intelligence trends and research. Risna Steenkamp, General Manager: ESM at value-added distributor Networks Unlimited Africa, says, “We have seen DDoS ransom attacks before – for example in October last year, South African banks were hit by a wave of ransom-driven DDoS attacks, as were other targets in other countries around the same time. However, with...
Networks Unlimited Wins 2 Channel Awards at Fortinet Africa Virtual Security Day
Networks Unlimited Africa, a leading value-added distributor operating within sub-Saharan Africa, received two awards, namely the Technical Support Distributor of the Year: Southern Africa award and the DLB Growth Distributor of the Year: East Africa award at the recent Fortinet Africa Virtual Security Day. This was the first time that the event took place via a virtual platform, due to the current restrictions around the global COVID-19 pandemic. The online nature of the awards ceremony also ensured that this broadened its reach to other parts of Africa, and not only within South Africa. Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited Africa, comments, “We have proudly maintained our business partnership with Fortinet, a global leader in broad, integrated and a...
ESET Launches ESET Cloud Office Security to Provide Advanced Protection for Microsoft 365
ESET, a global leader in cybersecurity, has today launched ESET Cloud Office Security, a new standalone software as a service solution that provides advanced preventative protection for users of Microsoft 365 applications. The software is designed to reflect the modern role of emails and collaboration tools used within organizations. Microsoft Office 365 is used by organizations all over the globe, with the cloud becoming an integral part of many businesses’ data storage and systems, regardless of their size. With more than 84% of organizations (according to Gartner survey*) using or intending to use Microsoft 365, it is crucial that businesses and their cloud tools are adequately protected. Businesses that leverage ESET Cloud Office Security are protected against incidents caused by email...
How SMEs Should Protect Themselves from Cybersecurity Attacks
Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited Africa Small and medium enterprises (SMEs) are widely acknowledged as playing a critical role in South Africa’s economy, and yet they are also potentially more at risk in terms of their ongoing survival than larger enterprises. According to a recent McKinsey report, SMEs in South Africa employ between 50 and 60% of the country’s workforce across all sectors. At the same time, SMEs arguably face a number of challenges, which can potentially weigh on them more heavily than on larger enterprises. These particular areas of concern include attracting customers; maintaining profitability; increasing revenue; facing greater uncertainty during economic down-turns, and securing financing for expansion. Now add in the issues a...
Networks Unlimited Africa keeps Value Offering Promises despite Lockdown Challenges
Anton Jacobsz, Networks Unlimited CEO Despite challenges of constraint, Networks Unlimited Africa has managed to maintain its standards during the lockdown in order to keep its unique partner offering intact. So says Anton Jacobsz, CEO at this leading value-added distributor in the sub-Saharan Africa market. He comments, “Networks Unlimited delivers products and solutions that are affordable, better than the competition, and with faster service delivery to our partners and end-users within the converged technology, data centre, networking, and security landscapes. “We are proud to have maintained our standards during the lockdown despite the difficult environment, especially during the initial phase of the early ‘hard’ lockdown. I commend the three general managers of our divisions and the...
How a Multi-channel Approach could Improve the Experience of Remote Workforces
As the COVID-19 pandemic irrevocably redefined the way we communicate and work, remote working and mobile workforces have become central to doing business in the new normal. This means that organisations are having to develop new communication strategies and channels to create a collaborative remote working environment for employees to ensure Business Continuity (BC). However, it goes beyond merely assisting them to set up shop in their living rooms and bedrooms so they can continue to carry out their daily activities, the biggest concern has been enabling as much productivity of the mobile workforce as when they were in the office. This means that remote workers should have access to the same software applications, data and tools as when working physically in the office. Yet not everythin...
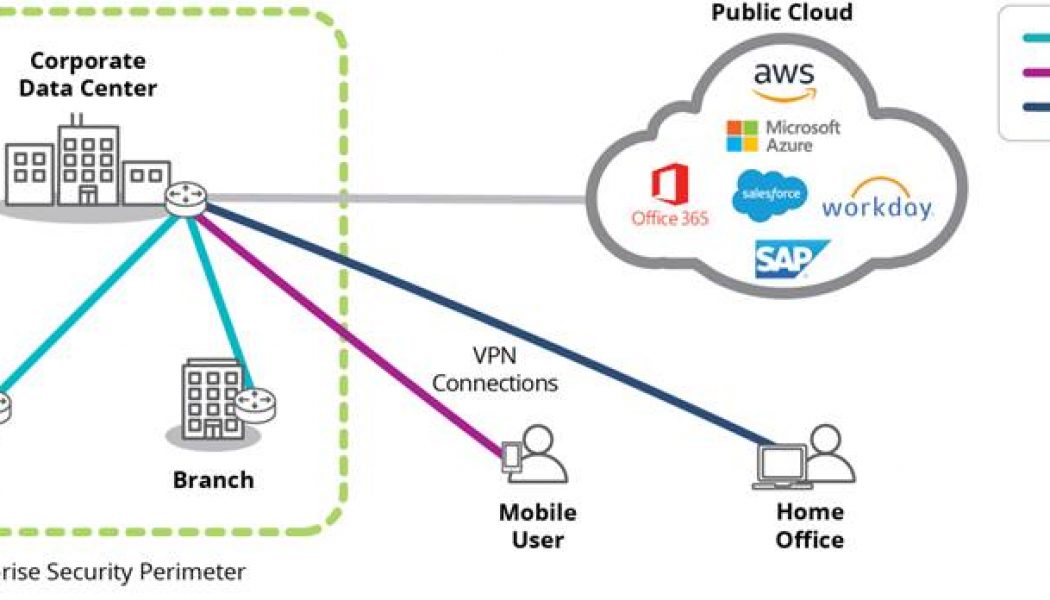
Silver Peak SD-WAN Capabilities Facilitate your SASE Journey
There are many acronyms in the world of IT, and SASE – the Secure Access Service Edge – is one of the latest that is gaining traction. It comes from a Gartner report published a year ago, and has been gathering strength ever since. The report is entitled ‘The Future of Network Security is in the Cloud’, and in it, the global research and advisory firm introduces the term to describe the need for the combination of wide-area network (WAN) transformation together with security transformation at the edge, to enable enterprises to realise all the benefits of moving applications and workloads to the cloud. This is according to a recent Silver Peak blog written by Derek Granath, Silver Peak VP of product marketing, who explains that SASE (pronounced ‘sassy’) involves a certain amount of ne...