Enterprise IT
Combined Rubrik and IDC Report Addresses Data Sprawl in the Modern Enterprise
Image sourced from Gerd Altmann, Pixabay Data sprawl – referring to the fact that valuable data is now commonly spread across multiple physical locations and different repository types – is one of the most critical IT issues that a modern organisation will have to manage. Not only does this expanse of data create issues for an organisation around its effective use, it can also negatively affect its security measures. This is according to a recent report from IDC, the global market intelligence firm, and cloud data management company Rubrik, which commissioned the IDC White Paper study and which involved just over 800 respondents in North America, Western Europe and the Asia/Pacific region. The white paper reveals that: Companies are not leveraging data to its fullest extent, causing ...
INTERVIEW: Strengthening the ICT Sector in Ethiopia
The ICT sector is fast-growing. To unpack this, Co-founder and CEO of iceaddis – Ethiopia’s first innovation hub and tech incubator – Markos Lemma talks to his experience of the East African country’s innovation ecosystem: How do you picture the development of ICT in Ethiopia? When we started iceaddis in 2011, Internet penetration was less than 1% among the population; and the role of ICT was limited. 10 years have passed since then; the internet penetration rate is around 19% today. We have seen significant progress in infrastructure, service provision, human capital and research. There are key players in the ICT sector and there is political willingness to advance this sector. In this regard, the contribution of the private sector is unneglectable. The Ministry of Innovation & techno...
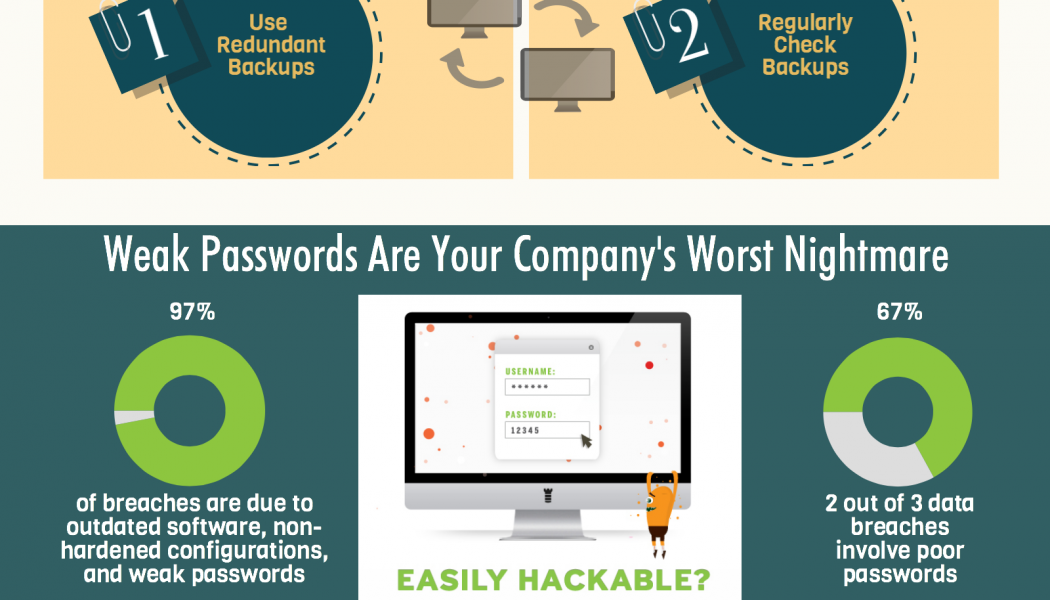
58% of Data Backups are Failing, According to Research
Data protection challenges are undermining organizations’ abilities to execute Digital Transformation (DX) initiatives globally, according to the Veeam Data Protection Report 2021, which has found that 58% of backups fail, leaving data unprotected. The report also found that against the backdrop of COVID-19 and ensuing economic uncertainty, which 40% of CXOs cite as the biggest threat to their organization’s DX in the next 12 months, inadequate data protection and the challenges to business continuity posed by the pandemic are hindering organizations’ initiatives to transform. “Over the past 12 months, CXOs across the globe have faced a unique set of challenges around how to ensure data remains protected in a highly diverse, operational landscape,” says Danny Allan, CTO at Veeam. “In respo...
How Cloud Migration can Boost Data Management
Sourced from InfoWorld. As cloud migrations accelerate, the need for effective backup and recovery becomes increasingly clear. This is also driven by compliance, with legislation such as the Protection of Personal Information Act (PoPIA) regulating the governance of data. With the PoPIA deadline, 1st of July 2021, becoming a reality, many businesses are trying to make sure they comply with all sections of the regulations. However, merely ticking a box for compliance can lead to challenges down the line. Data management impacts vary from company to company, and there is no such thing as a one-size-fits-all approach. With data regarded as a valuable asset, organisations need to understand what data they have, where it resides and of what importance it is. The process of migrating to the clou...
Liquid Telecom Unveils New Identity and Pan-African Strategy
Image sourced from MyBroadband Liquid Telecom has unveiled its new identity as Liquid Intelligent Technologies. The pan-African technology group also revealed its plan to go from being a telecommunications and digital services provider to a full one-stop-shop technology group through a group-wide rebrand. Over the last two decades, Liquid has firmly established itself as the leading pan-African digital infrastructure provider with an extensive network spanning over 73,000 KM. This rebrand to Liquid Intelligent Technologies highlights the organisation’s expansion of its Cloud business, Cyber Security services, and other technologies added to its existing telecoms and connectivity capability. This furthers the Group’s aim of accelerating growth by providing tailor-made digital solutions to b...
How to Create a Culture of Cybersecurity
Sourced from IDG Connect Security. This is a word that can make a grown CFO tremble and an entire SOC crumble. It is the word that captures a complex landscape littered with complexity, cybercriminals and technology. It defines how well an organisation adheres to a growing body of legislation – GDPR, POPIA and other data protection regulations – and how its reputation fares when a breach is revealed and information exposed. Security should be on every boardroom agenda, in ongoing employee training, and an investment into the right tools and solutions. But, perhaps most importantly, security should be an inherent part of the company’s culture because it is this factor that ultimately determines its security risk and posture. “There is a clear link between security culture and secure behavio...
Tintri Drives Intelligent Infrastructure so You Can Get Ready to ‘Let Go of the Wheel’
The concept of self-driving cars is controversial and tends to polarise opinion. At the heart of it is the idea that a car will be capable of the same split-second decision-making as a human – or even better – with the ultimate goal of creating accident-free roads. For a vehicle to be autonomous, it needs to be continuously aware of its surroundings: firstly, by identifying and classifying information, and then by acting on the information through the computer control of the vehicle. And for this to happen, artificial intelligence (AI) is required, it is a critical technology in the goal of realising autonomous driving. “One of the main premises of self-driving cars is the idea that autonomy equals safety,” says Michael Donaldson, Tintri Product Manager at value-added distributor Net...
INTERVIEW: Unpacking ESET South Africa’s Approach to Innovation in 2021
After a year in which the COVID-19 pandemic upended the way we live, work and socialize, Carey van Vlaanderen, CEO of ESET South Africa, has revealed to IT News Africa the innovations and challenges expected to impact businesses in 2021. Here’s what transpired: The COVID-19 pandemic has forced organisations to adapt to a new, remote way of working; How has ESET risen to this challenge? With the interrupted electricity supply affecting our business throughout the years, we had made the decision some time back to ensure that all employees were mobile and as off the grid as possible. This meant equipping all employees with laptops and backup power and connectivity, both at work and at home. This meant that when COVID-19 hit, we were able to adapt quite quickly. We also took learnin...
Telco Vs TechCo – a Battlefield for the Future of ICT
Across the world, disruption has become a reality that is driving changes the business sectors. Included in this disruptive environment is the telecommunications industry, which is having to take account of changing technologies and the challenges these changes bring to the way the sector has traditionally done business. Under examination must be the industry’s twin roles as a primary provider of telephone services and platforms to OTT suppliers to launch their offerings to users. Internationally, experience shows that there has been an average decline in revenues per user as IT suppliers, offering focused services, have made products built around mobile and data less critical to end-users. Although some different market factors apply to the African and South African markets, we are not ex...
COVID-19 Fuels Global Appetite for App Modernization, AI and Edge Computing
COVID-19 has catalysed the speed and depth of the world’s digital transformation efforts, according to F5’s latest State of Application Strategy (SOAS) report. This year’s report strongly underlines how the need to improve connectivity, reduce latency, ensure security, and harness data-driven insights is intensifying. It also points to an elevated interest in cloud, as-a-service solutions, edge computing, and application security and delivery technologies. “The COVID-19 pandemic has vastly accelerated a global digital transformation that was already underway. Progress that might normally have taken a decade has leapt forward in a single year,” says Lori MacVittie, Principal Technical Evangelist, Office of the CTO at F5. “In a short time, more organization...
In the Eye of the Storm: New Record is Set by Ten Million DDoS Attacks in One Year
Not all record-breaking numbers are feats or achievements towards which we all aspire. For example, in 2006, American teenager Matt Suter was destined to become the holder of the record for the ‘farthest distance thrown by a tornado and survived’, when he was flung, in an unconscious state, for a distance of almost 400 metres (398.37 metres) by an F2 tornado (meaning wind speeds of 181 to 253 kilometres per hour), yet later regained consciousness almost without a scratch. “We’ve recently had a very thought-provoking record-breaking number released for 2020 in the cybersecurity arena, and it’s not pretty,” says Risna Steenkamp, General Manager: ESM Division at value-added distributor Networks Unlimited. “Distributed denial of service (DDoS) attacks have crossed the 10 million mark dur...