Digital Transformation
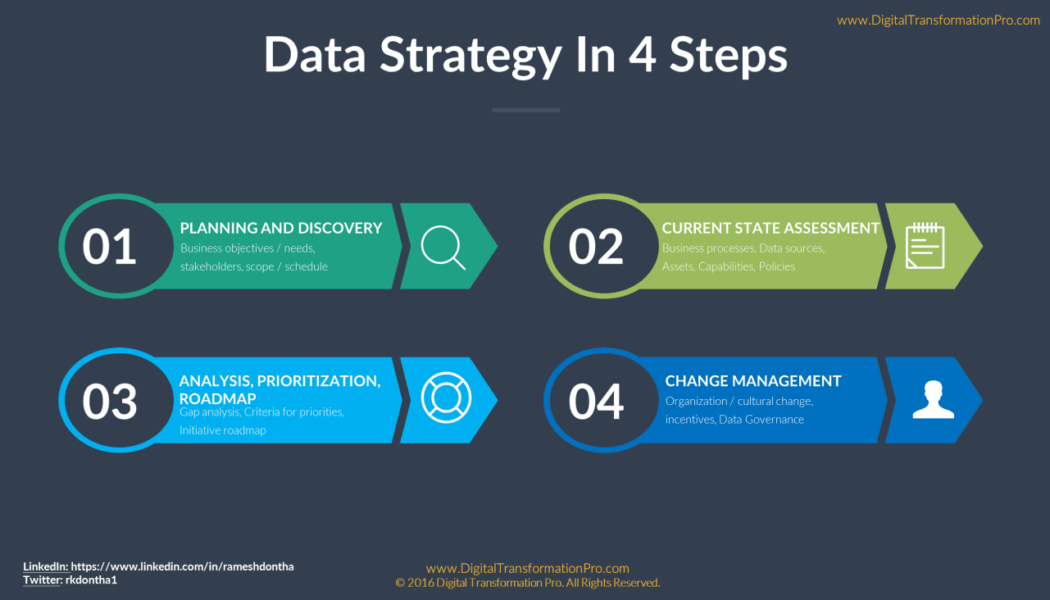
Every Digital Business Needs a Data Strategy
Sourced from TTEC.com Even though data has become one of the most critically important assets in an organisation, most companies have yet to align this with their business strategies. Not doing so results in an inability to identify and prioritise the interventions needed for growth and effectively measure their success. But doing so is not without its complexities. For the most part, a data strategy comes down to identifying and understanding the data that is being worked with. Having this in place can improve the way a company acquires, stores, manages, shares, and uses data. The underlying processes and the governance involved in how all this is managed are all key components of such a data strategy. Even if this is in place, the biggest obstacle is still on how to best integrate it wit...
Confidential Computing – Why Privacy Should be the Heart of Digital Experiences
Image sourced from Intel. In this past year, the consumer experience came to the forefront. As we faced various stages of lockdowns, we turned to online banking, seeing our doctors remotely, running our businesses using technology and socialising through a screen. Digital interactions became a part of our lives – ever-present and normalised as we navigated changes swept in by this pandemic. As our digital interaction became seamless and permeated through every aspect of our lives, privacy continued to be top of mind. We carried out our lives predominantly online – making many of us more vulnerable to fraudsters. As we navigated living our lives digitally, data theft dominated 2020 as the most common attack in the Middle East and Africa. Across the region, data theft and leaks accounted for...
How COVID-19 Has Changed E-Learning Forever
Image sourced from Entrepreneur. E-learning has changed. Much of this change is due to COVID-19, and there’s no going back to the way we were before, however, many organisations may want to do so. “COVID arrived and new technology came to the fore – like Zoom, Meets, Teams and so on. How did you upskill your people on it? Were they ready for it? Are you teaching people to get the best out of things like LinkedIn?” says Michael Gullan, CEO of corporate e-learning consultancy G&G Advocacy. “Executives may not be as equipped to deal with online networking now that physical networking events aren’t as common anymore. Can your C-Suite execs use these tools? Can your sales team?” Companies can no longer afford to see their e-learning as a grudge purchase or an afterthought, says Gullan. “Tha...
Why Digital Workplaces are the Future of Remote Work
According to Gartner, a global research and advisory company, the digital workplace is a business strategy for promoting employee effectiveness and engagement through a more consumer-like computing environment. Offices are now becoming location and device agnostic and moving to the cloud or following the sun to reduce project duration and increase responsiveness. ITC Infotech, a leading global technology services and solutions provider, led by Business and Technology Consulting, has invested in building a secure digital workplace solution over the years, for a differentiated offering with a proven value proposition. The adoption of the digital workplace by companies across the world is at a nascent stage, but very few understand the relevance of the digital workplace strategy. A digital wo...
How Emotion AI Can Make the World a Better Place
Most of us take it for granted that we can read another person’s emotions through subtleties such as body language, yet this is a real struggle for many others. Enter emotion AI. Researchers at Stanford University modified Google’s augmented reality glasses to read emotions in others and notify the wearer. The glasses detect someone’s mood through their eye contact, facial expressions and body language, and then tell the wearer what emotions it’s picking up. “Emotion AI taps into the individual,” explains Zabeth Venter, CEO and co-founder of Averly. “If you think about facial recognition, which is a kind of emotion AI, I can pick up if you like what I’m saying by whether your smile is a smirk or a real genuine smile.” Such nuances go deeper. Another example is polling: what is your favouri...
5 Ways to Ensure Your Organisation is POPIA Compliant
Sourced from Europa EU. On 1 July, the grace period for compliance with the Protection of Personal Information Act (POPIA) will come to an end. That means organisations found to be in breach of the act will be liable for fines and even criminal persecution. Given the long lead up to POPIA’s implementation, most organisations should be compliant by now. However, the flurry of activity when the European Union’s General Data Protection Regulation (GDPR) grace period came to an end in 2018 shows that this won’t necessarily be the case. And while POPIA will affect most organisations, it’s pivotal that they pay extra care when ensuring that they’re POPIA compliant. Here are five ways to do just that: Understand the data you deal with You cannot hope to adequately protect customer data in li...
South Africans Think Software Update Time can be Used to Increase Productivity
Installing updates is considered a routine boring task, according to a study commissioned by Kaspersky. The research revealed that four-in-ten (47%) of South Africans admit that the time spent waiting for updates to take place can be used productively and they are making this a reality in their day-to-day lives. Updates to devices are not only necessary to gain access to new features or interfaces, but they also help to maintain a high level of security. Vendors regularly test their offerings to find new potential vulnerabilities that could be exploited by attackers. The timely installation of updates can serve as an effective defence against cybercriminals. This downtime can also increase people’s productivity and help with well-being. South Africans agree that the time spent waiting for ...
Contactless Payment Methods Beat Traditional Options for the First Time
Sourced from Htxt.Africa South African bank, FNB has revealed that contactless payments have surpassed Chip and PIN contact payments for the first time ever among its Credit, Debit, Fusion, and Virtual Card users. The Bank attributes the behavioural shift (from chip contact to contactless) to consumer’s preference and awareness of safer, convenient, and quicker means to pay at a Point-of-Sale. “This is a remarkable milestone for the financial services industry, and it augurs well for efforts to improve safety and convenience in the payments network,” says Raj Makanjee, Payments Executive at FNB. “With over 10 million contactless cards in the hands of our customers and 200 000 Virtual Cards activated, we are delighted to see our customers pioneering what we believe to be the future of payme...
Should West African Businesses Embrace Mobile Authentication for Security?
Sourced from International IDEA Digital technology has not only profoundly altered the way we live our lives, but also changed the pace of communication and commerce, allowing us to do everything, immediately. While this has effectively impacted every aspect of our lives, it also inevitably changed the way we are targeted by fraudsters. Along with the world transforming to digital, so has crime. According to an Accenture report published in 2019, the total value at risk of cybercrime over the next five years is an estimated $5.2 trillion. The average cyberattack costs $13 million, according to the same report, with phishing, social engineering and stolen device crime making up $2.4 million of the cost of an average attack. In West Africa, cybercrime is on the increase, with a recent analys...