data protection
How a Data Breach Can Impact a Business Even Years After
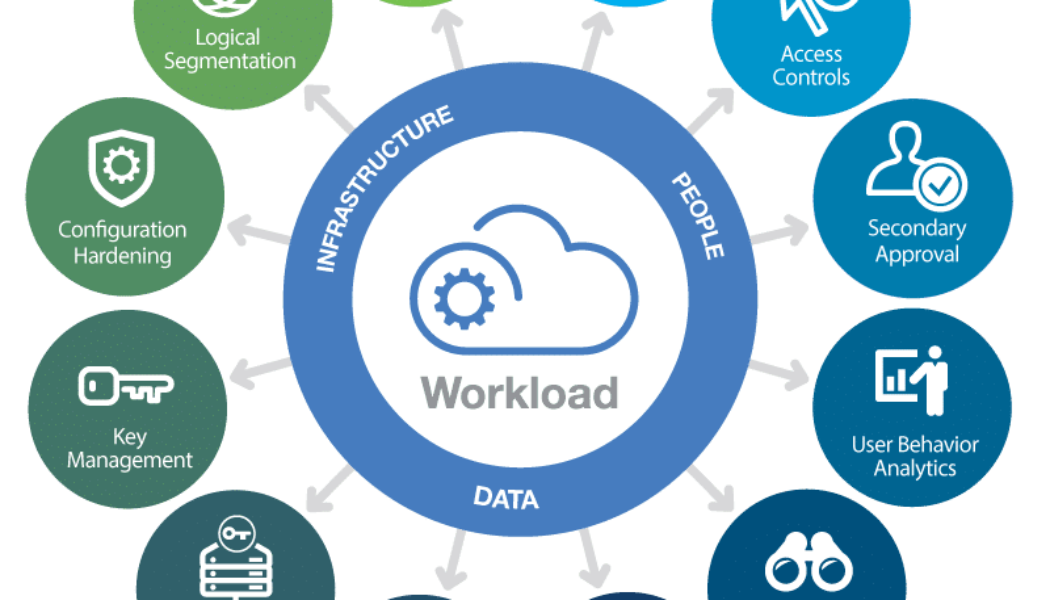
Image sourced from Forbes. Modern enterprises face an onslaught of cyberattacks from many quarters and must not only be prepared to contend with the direct costs of potential breaches but also with spiralling indirect costs, such as compliance fines and reputational damage. As the threat landscape continues to evolve, so do the frequency and sophistication of attacks, with companies facing anything from denial of service attacks and phishing attempts to payment card skimming, identity theft, and account takeover threats. At the same time, ransomware attacks have gained prominence over the last few years, forcing companies to continually test their data protection plans to understand the risks associated with having sensitive data released to the public. In its State of Ransomware 2021 repo...
Ransomware: The Threat that Lies in Wait
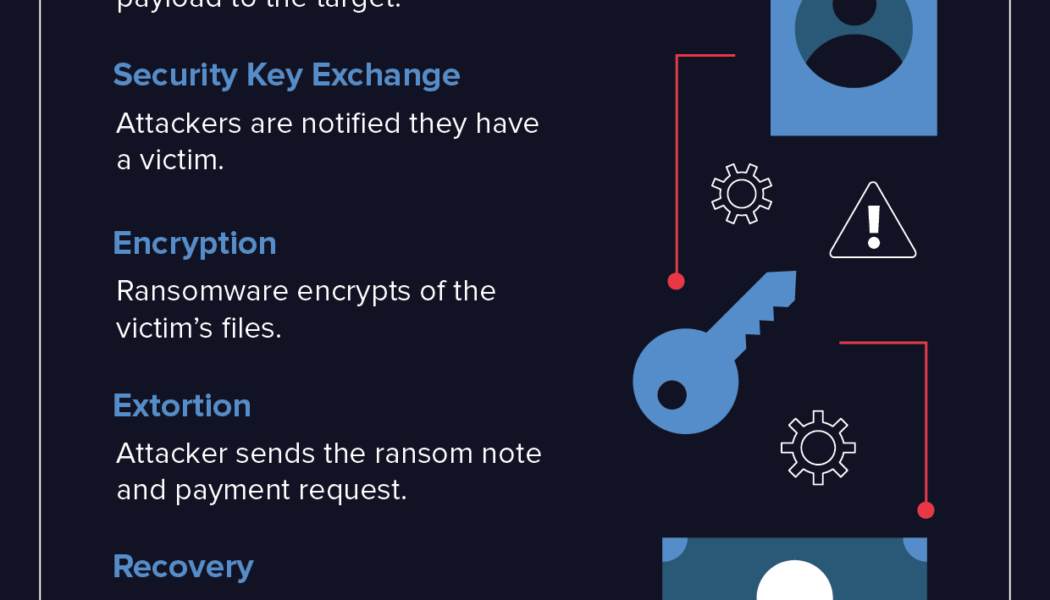
There can be no doubt that ransomware attacks are on the rise across the globe. A simple online search will reveal thousands of statistics in this regard, and South Africa is no exception. What is also clear from numerous examples of successful breaches, is the potentially devastating effect of a ransomware attack, which can cripple a business and shut down essential services for extended periods, not to mention cost a fortune to recover from. They are, in fact, legitimate business disasters, and need to be considered as such when it comes to disaster recovery and business continuity planning. Under Siege There is no shortage of high-profile examples of ransomware attacks in South Africa over the past two years, from Johannesburg City Power to the Life Healthcare hospital group, Transnet P...
Effective Data Backup Becomes Essential as Kenya is Rocked by Ransomware
In the wake of the COVID-19 pandemic, cybercrime, in particular, ransomware, has seen a massive increase across the globe. As a burgeoning economy in Africa, Kenya has become a growing target, with a new report from internet security group Kaspersky recording 32.8 million attacks in the first half of 2021. According to INTERPOL, increasing digital demand in the country, coupled with “a lack of cybersecurity policies and standards, exposes online services to major risks”. As digital transformation continues to gain traction in Kenya, data becomes increasingly important for business, and it needs to be effectively protected. Effective data backup and recovery are key to overcoming the potential threat of a ransomware attack. Connected, but vulnerable In Kenya, as in much of the world, the pa...
Why Balancing Customer Experience with PoPIA Compliance is Critical
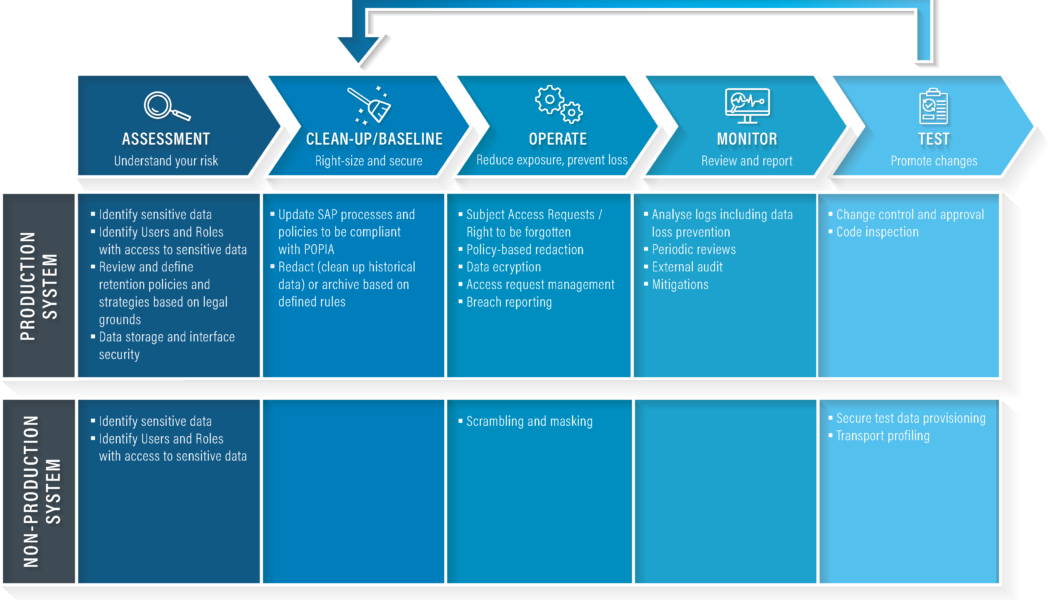
Image sourced from Innoverse 365. Meeting growing customer demand for relevant, personalised experiences while managing the regulatory demands of protecting data is emerging as one of the most significant challenges facing South African businesses today. Aspects such as managing customer consent and conforming to data privacy legislation create complexities for cloud-based data and analytics solution providers, the brands that use them, and the customers themselves. Given how the management of personal information (PI) is driven by the likes of the General Data Protection Regulation (GDPR) in Europe and the Protection of Personal Information Act (PoPIA) in South Africa, companies and providers need to navigate a minefield of compliance requirements to avoid significant financial fines and ...
How Will PoPIA Impact Cloud Providers?
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent. You Deserve to Make Money Even When you are looking for Dates Online. So we reimagined what a dating should be. It begins with giving you back power. Get to meet Beautiful people, chat and make money in the process. Earn rewards by chatting, sharing photos, blogging and help give users back their fair share of Internet revenue.
How Will PoPIA Impact Cloud Providers?
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent. You Deserve to Make Money Even When you are looking for Dates Online. So we reimagined what a dating should be. It begins with giving you back power. Get to meet Beautiful people, chat and make money in the process. Earn rewards by chatting, sharing photos, blogging and help give users back their fair share of Internet revenue.
- 1
- 2