cybersecurity
Why Ransomware is the Greatest Threat to Your Organisation
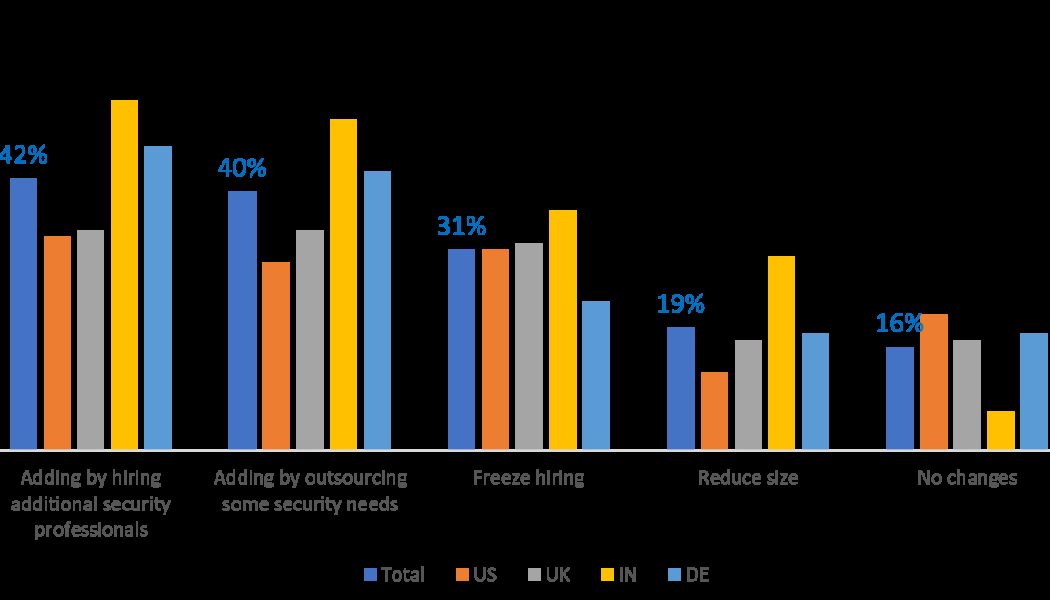
Ransomware is getting nastier and more expensive all the time and it has affected almost every industry and geography. No one is immune from the threat. In a global ransomware survey conducted by Fortinet, 67% of organizations report suffering a ransomware attack. Even worse, almost half said they had been targeted more than once, and nearly one in six said they had been attacked three or more times. Renee Tarun, Deputy CISO/ Vice President Information Security, Fortinet Inc. The US Treasury’s Financial Crimes Enforcement Network (FinCEN) reported that organizations paid out almost $600 million in ransomware in the first half of 2021, which puts the US on track to surpass the combined payouts of the previous decade in a single year. Last year’s attacks on the suppl...
Why Women Are Underrepresented in Cybersecurity
Sourced from Women in Tech Africa. One of the industries struggling with significant bias and gender stereotypes is cybersecurity. This field plays an increasingly crucial role in our digital world and, as a result, offers many fulfilling career paths and opportunities. However, there are still significant barriers and misperceptions driving the belief that a career in cybersecurity is not for women. While women have been disproportionately impacted by pandemic-driven unemployment (for example, one in four women reported job loss due to a lack of childcare—twice the rate of men), the technology sector was less affected. This was mainly due to their being better prepared to pivot to remote work and flexible work models. As a result, according to a report by Deloitte Global, l...
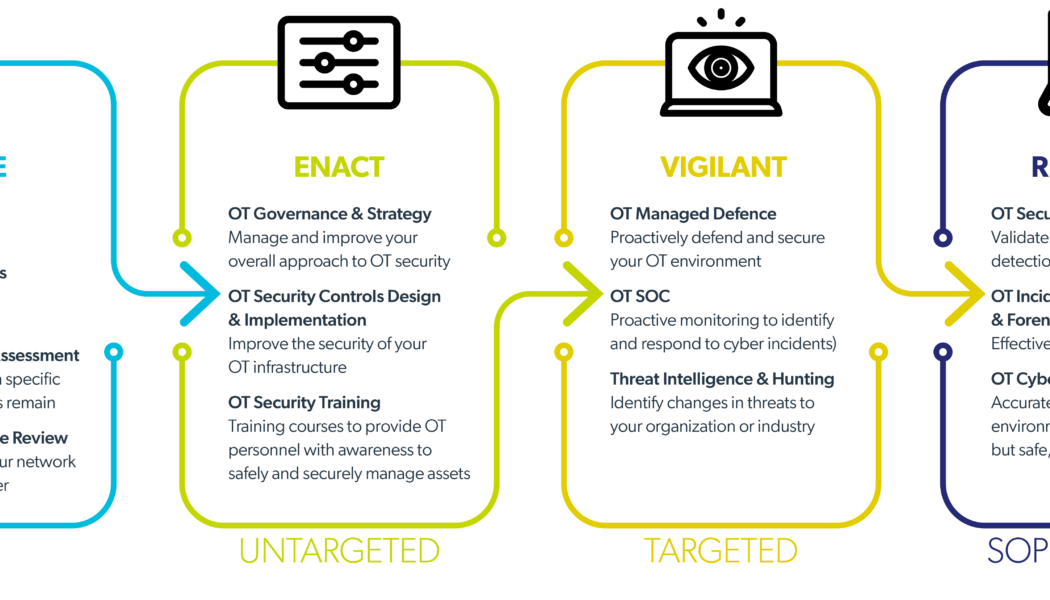
OT Security – Everything You Need To Know
Image sourced from Twitter: @SmartIndustryUS Most enterprises know that cyberattacks in the information security realm are continuously growing in sophistication, severity and number. However, up until now, many organisations that run plants, factories, pipelines and other infrastructure have paid less attention to the threats they face in the realm of operational technology (OT). Recent global, OT-focused cyberattacks highlight why South African utilities, manufacturers, oil & gas companies and other organisations that run industrial infrastructure would be wise to take note of the growing range of cyber threats faced by their OT systems and infrastructures. In one example, an intruder breached a water treatment plant in Florida in the US. The attacker briefly increased the quantity o...
What every leader must know about cybersecurity
Digitization means every single company now is vulnerable to cyberattacks. Cybersecurity has now become a topical issue affecting enterprises and the bedrock of tomorrow’s intelligent business. For enterprises to succeed they have to invest in digital capabilities that are robust and supported by a cybersecurity strategy that is sophisticated enough to ward off any attacks. Join Shelt & IT News Africa for this informative panel discussion around the constant threats enterprises face and what leaders in the industry need to know about building winning cybersecurity strategies for your business that go far beyond avoiding this worst case scenario. This will be followed by a simulation of a hypothetical crisis where the panel gets to discuss and come up with possible solutions. Date: ...
The impact of the pandemic on cybersecurity
Ralph Berndt, Director of Sales at Syrex Even prior to the pandemic, organisations had begun putting in place elements to manage distributed employees whether that be through corporate remote desktop or virtual private networking (VPN) capabilities. However, this was not done at the scale and at a rate required to manage the disruption caused by COVID-19. Suddenly, companies had to deal with the influx of connectivity challenges that they needed to overcome for their employees to remain productive. Furthermore, support teams now had to manage providing access to critical systems, which were mainly hosted on-premises within the relative safety of their own corporate network. In many cases this resulted in companies having to implement more VPN licences to manage these additional external co...