cybersecurity
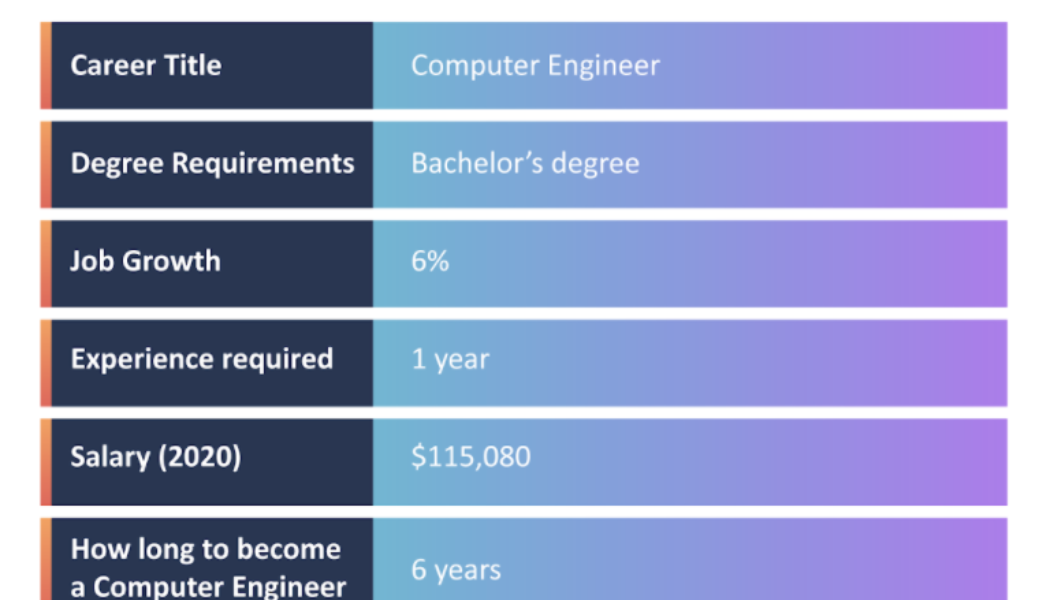
What Can You Do With A Degree In Computer Engineering?
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
HMI – How People, Processes and Technology Work Together
When embarking on an industrial digitisation project, it’s important to consider how people, processes, and technology will work together. These three considerations are integrated in a somewhat symbiotic manner, which is why each should function optimally and compliment the other. A good example is IIoT; the technology promises secure access to a lot of data but is this data providing the right insight to people as opposed to burying them under a heap of information? Also, how do you ensure insights are delivered to workers whenever and wherever they need them, such as on the plant floor where they are working around production equipment. HMIs and Industrial Automation Enter Human-Machine Interfaces (HMIs); a technology developed to replace hard-wired pushbuttons and indicator lights with...
Why Organisations Need to Invest in Digital, Customer-Facing Technology
Image sourced from www.emediait.com Over the past two years, Chief Information Officers (CIOs) and senior IT executives have largely focused their efforts on digital transformation. This is mostly because COVID-19 forced organisations to expedite planned and unplanned re-engineering of their IT environments to fulfil the digital marketplace’s ever-increasing demand. While the top issues for IT departments have traditionally been (and continue to be) digital transformation, cybersecurity, data compliance, and cloud migration, customer experience has also become a top priority. This highlights the necessity to maintain a customer-centric mindset during digital transformation efforts, to increase customer retention, encourage repeat business, and grow revenue. Customer-centric digital transfo...
Bad Actors Innovate, Extort & Launch 9.7M DDoS Attacks
In March 2022 we released our 2H 2021 Threat Intelligence Report. The report covers worldwide distributed denial-of-service (DDoS) attack activity during 2021—particularly during the second half of the year. As always, it’s chock-full of DDoS attack statistics, trends, and insights from our elite NETSCOUT ATLAS Security Engineering and Research Team (ASERT). Key findings include: DDoS attacks continued to exceed pre-pandemic levels. During the second half of 2021, cybercriminals launched approximately 4.4 million DDoS attacks, bringing the total number of DDoS attacks in 2021 to 9.75 million. These attacks represent a 3 percent decrease from the record number set during the height of the pandemic but continue at a pace that’s 14 percent above pre-pandemic levels. DDoS extortion and ransomw...
How to Secure Your Remote Work Environment from Cybersecurity Threats
Sourced from International IDEA Cybersecurity threats are at an all-time high. With organizations increasingly employing hybrid work models, it has become more vital than ever to educate employees on the various cybersecurity risks that come with a distributed work environment. In a hybrid work environment, employees working from home pose a greater security risk compared to those working at the office. Home networks are less secured than corporate networks, unprotected by in-office firewalls and advanced fraud detection systems. In the comfort of one’s home, a small mistake by an employee could potentially risk the company’s confidential data being leaked. However, risks like data leaks and device compromise can be managed by following certain best practices. Here are some of the practice...
How Emails Can Cause Cybersecurity Vulnerabilities in Your Organisation
Sourced from International IDEA Since the start of the pandemic, many businesses have shifted to remote work. Cybercriminals saw the opportunity to target businesses’ remote users leaving unprepared businesses vulnerable to cyberattacks. Phishing attacks have become one of the most prominent data security problems for a number of businesses in South Africa. “Remote working increased organisation’s reliance on email, creating the perfect conditions for email fraud and phishing,” says Riaan de Villiers, Business Analyst at LAWtrust Information Security. In the Mimecast State of Email Security 2020 study, businesses in South Africa reported a 53% increase in phishing attempts and a 46% increase in incidences of impersonation fraud compared to previous years. Email is a common channel used for...
Understanding the Risks to Cryptocurrency Trading
Sourced from Hacker Noon. Alongside self-fertilizing crops and low-carbon shipping, cryptocurrencies have made the World Economic Forum (WEF) list of top tech trends in 2022 bolstered by research by the Thomson Reuters Foundation that describes it as moving from the ‘fringes of finance to the mainstream’. Perceptions around cryptocurrencies have shifted, with several countries adopting it as legal tender, banks looking to create their own forms of digital currency, and consumers putting their savings into crypto wallets instead of traditional financial institutions. Anna Collard, SVP Content Strategy & Evangelist at KnowBe4 Africa. Countries are either considering or are already partially using Central Bank Digital Currency (CBDC), which essentially allows for companies and individuals...
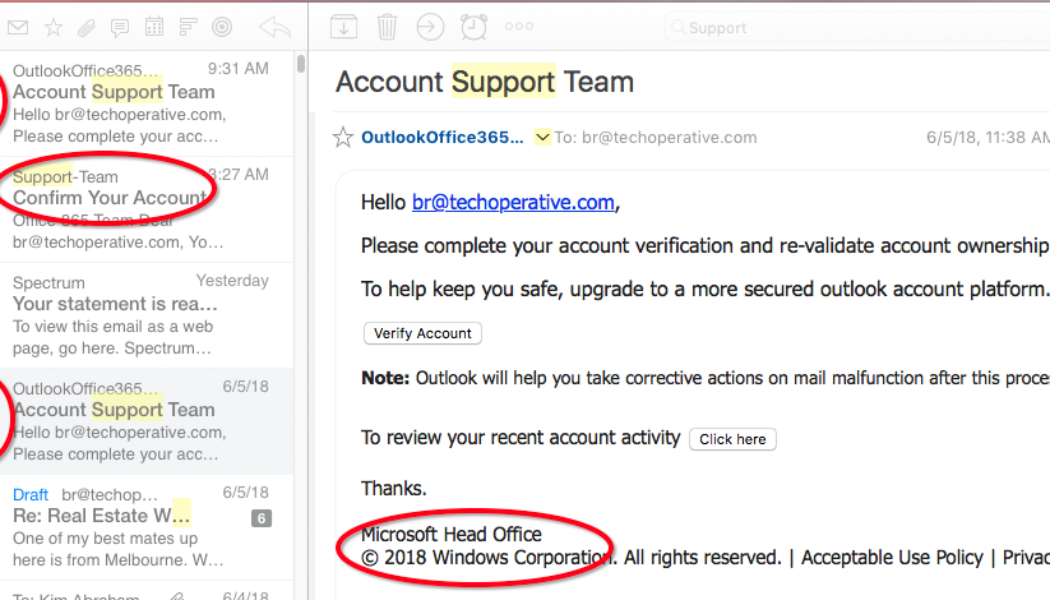
How to Be Safe From the “Reset Password” Email Scam
Image sourced form Broad Media Most online services have built-in security systems that alert employees when the systems detect “unusual” activity on their accounts. For example, legitimate email services or similar will send notifications about attempts to reset the phone number and e-mail address linked to the account, or the password. Of course, as soon as such messages became commonplace, enterprising cybercriminals tried to imitate this mechanism to attack corporate users. As cyberattacks rely on the human factor more often each year, and as cybersecurity technologies progress, such tricks are becoming more and more common and are being registered in multiple mailouts around the world. The scenario is usually as follows: if it’s a public online service attacker it will usually make ev...
DeFiance Capital founder loses $1.6M in hot wallet hack
Founder of major crypto investment firm DeFiance Capital, “Arthur_0x”, has suffered a hack on one of his hot wallets resulting in the loss of more than $1.6 million in nonfungible tokens (NFTs) and crypto. In a tremendous show of support, the crypto community has come to his aid to help retrieve the stolen items as he asked people to blacklist the hacker’s wallet. Several individuals on Twitter have attempted to determine exactly how the hack occurred and where the hacker gained access to his wallets. NFT community member “Cirrus” went as far as buying two of the stolen Azuki NFTs and deciding to return them to Arthur at cost. Cirrus told Cointelegraph today that he: “found out they were hacked, and instead of selling them for profit like the other folks who got some of his, decided I’d se...