cybersecurity
Hybrid Cloud Environments Provide Cheap Security for Financial Service Organisations
Sourced from ZDNet. Worldwide, financial services organisations are turning to the cloud as the means to transform outdated legacy systems and commit to disruptive technologies. The size of the public cloud market is expected to top $354 billion by the end of 2022, a significant jump from the less than $197 billion of 2018. But instead of going the all-or-nothing route, the hybrid cloud is positioned to provide companies with a more secure way of leveraging their data. Yunus Scheepers, CTO at SilverBridge, discusses these security benefits at a time when Microsoft Azure data centres in the country are attracting attention from financial services organisations as a safer alternative to what their current on-premise offerings can provide. A hybrid cloud environment also provides risk-averse ...
Inadequate Investment in Cybersecurity is Behind Increase in Cyber Attacks
Following on this week’s Life Healthcare cyberattack, the issue of cybersecurity has once again been brought to the fore as businesses and individuals are forced to evaluate whether measures in place are strong enough to withstand major breaches in their security. Life Healthcare is the third major South African company that has been targeted by hackers this year. In February, Nedbank warned that the information of about 1.7 million clients was potentially affected by a data breach, and the following month chemicals and fertiliser maker Omnia Holdings said it’s IT infrastructure was subject to a cyberattack. Amongst the other big businesses that have been targeted in South Africa are Johannesburg City Council, Capitec Bank and Telkom. The trend is also true for the rest of the continent. I...
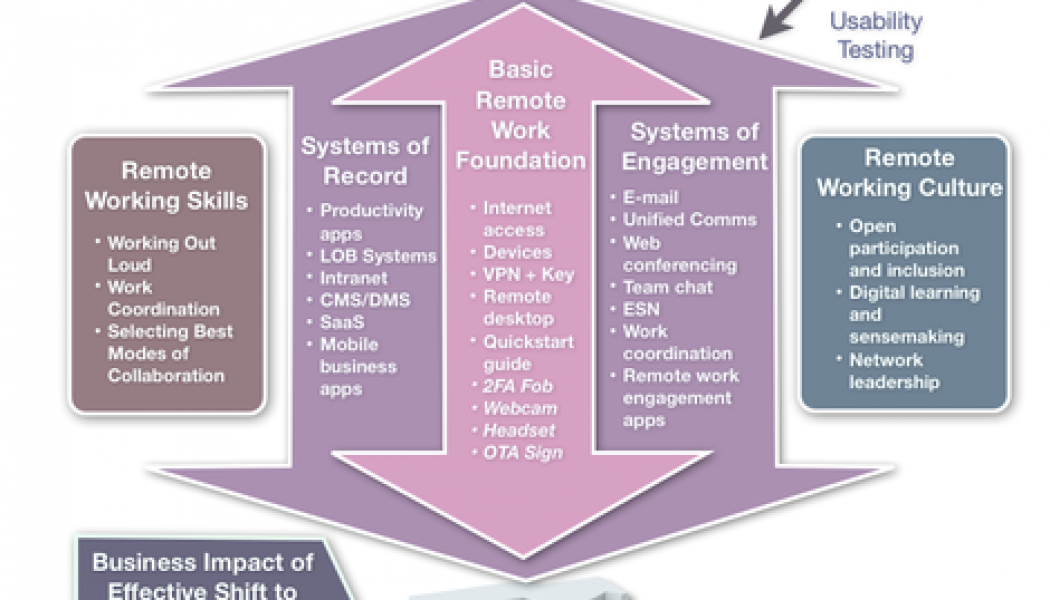
How Using Cloud Can Increase Security for Remote Working During the Pandemic
Sourced from Tapscape The cloud can enable organisations to quickly scale out enhanced security to a suddenly remote workforce, as part of efforts to ensure business continuity and disaster recovery – this is according to Patrick Grillo, Senior Director and Solutions Marketing at Fortinet. The pandemic had created unique challenges for employers and employees across all sectors around the world, with Varun Kukreja, Senior Program Manager – IT Security MEA, IDC Middle East, Africa, & Turkey, saying securing the teleworker had become a top priority, with some 90% of organisations looking to provide staff with secure access to IT services and applications. The pandemic had also accelerated digital transformation, he says, with an IDC Meta survey interim results revealing that some 56% of ...
CIOs Should Embrace the Opportunities of a Post-lockdown Market
As South Africa enters the tenth week of the nationwide lockdown, the business focus has shifted from enabling employees to work remotely to now planning for what the new normal is likely to look like. This requires CIOs to balance existing organisational priorities with ways of becoming more adaptive to the changing environment. Critical to this is decisive decision-making that positions the business for growth. For small to medium-sized businesses that do not have all the skills in-house to transform their IT environments, decision-makers should consider going the outsourcing route. By partnering with a managed service provider (MSP) that can deliver everything from a cloud-readiness audit through to helping identify the technology gaps that exist between the business strategy and what i...
Cybercrime has Increased by 33%, Report Shows
The 100 Days of Coronavirus report – published by Mimecast – shows that the volume of malicious and opportunistic cybercrime has increased significantly by 33% in the period January to March 2020. The new report has found that in the period January to March 2020 monthly volumes of: Spam and opportunistic cybercrime detections increased by 26.3%, Impersonation fraud detections increased by 30.3%, Malware detections increased by 35.16%, and Blocking of URL clicks increased by 55.8%, meaning people are more likely now to click on unsafe links than before the outbreak. Over the months of February and March, as South Africa reported its first case and moved swiftly into lockdown, the Threat Intelligence Team saw dramatic increases in cyberattacks in Sub-Saharan Africa. Carl Wearn, Head of E-Cri...