cybersecurity
Here’s How Many Mobile Users in Kenya and Nigeria are Affected by Stalkerware
Stalkerware affects one out of every 100 mobile users in Kenya and Nigeria, according to Kaspersky Research. The same report reveals that similar malware impacts every four out of 100 South Africans. “Even though these numbers might seem low, especially when it comes to stalkerware, it bears mentioning that this form of attack is focused on specific individuals,” says Lehan van den Heever, Enterprise Cyber Security Advisor for Kaspersky in Africa. “So, unlike general malware that is distributed on a massive scale, stalkerware is a more personal crime that has life and death consequences for the individual affected, for example, a perpetrator can track down their estranged partner with ill intentions, or human trafficking rings targeting children.” Amongst other things, stalkerware can enab...
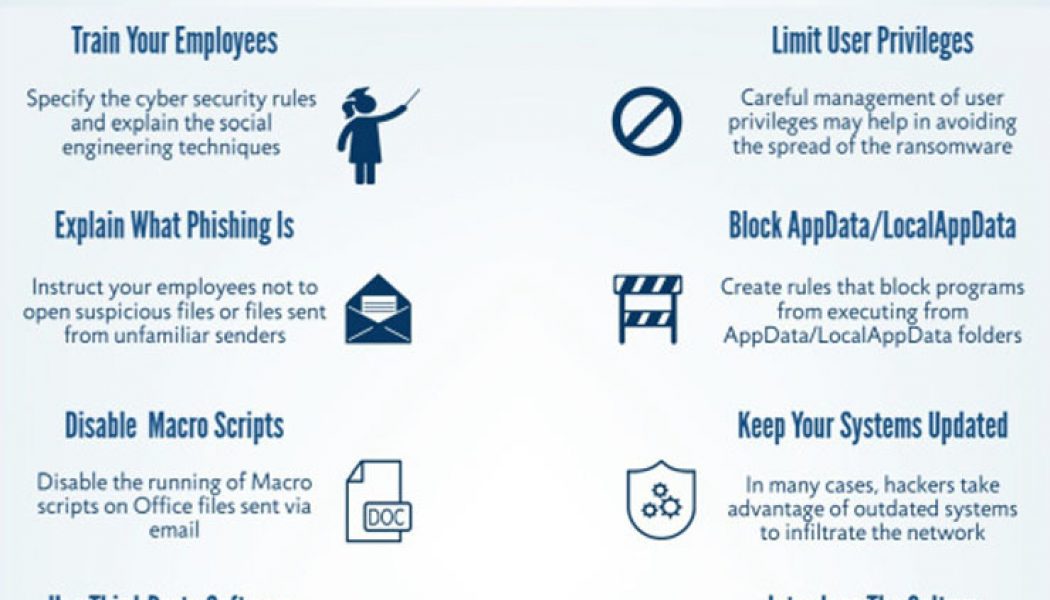
Why Cybersecurity Patches are only Part of a Plan
Patches are undoubtedly an essential component of a cybersecurity strategy. They can be used to address vulnerabilities, resolve issues or improve solutions. However, a patchwork approach alone is simply no longer sufficient. The current digital landscape, with many employees continuing to work from home, means most organisations’ attack surfaces are so much wider and less contained than before. Businesses need a plan that includes patch management and vulnerability management as part of an overarching strategy aimed at mitigating and managing cybersecurity risk. A place for patches Patches are useful tools, ensuring that updates can be pushed out, vulnerabilities addressed and recommended configuration changes made across an organisation. Patches are typically a retrospective development ...
How Hackers are Taking Advantage of the COVID-19 Vaccine Rollout
Image sourced from TimesLIVE Cybercriminals are well known for taking advantage of any opportunity. The largest vaccine rollout in history is no exception, with hackers now finding ways to target the supply chain. Understanding why the COVID-19 vaccine supply chain being targeted and how to protect against such attacks is vital for IT leaders who understand that healthcare and cybersecurity must now go hand in hand. Understanding the impact of the COVID-19 vaccine supply chain on healthcare cybersecurity The healthcare sector underwent several significant shifts during the pandemic. These shifts included a move toward offering telehealth services on a large scale, setting up remote, temporary COVID-19 testing and vaccination sites, and large-scale development, manufacturing, and distr...
How Companies Should Deal with the Threat of Cybercrime
Sourced from International IDEA Cybercrime is on the rise and South African C-suites would do well to ensure that they have up-to-date and appropriately resourced strategies to deal with its threat. The pandemic showed us that while land and sea borders can be shut, in the digital village this is not possible, and more importantly, in many instances, it is unclear where these attacks originate. The definition of cybercrime perhaps holds the key to who should take it seriously. Cybercrime is defined as criminal activities that are carried out by means of a computer or the internet. Anyone who uses a computer that is connected to the internet should have a cybercrime strategy in place. No matter where you are in the world, if you let your guard down you are at risk. Everyone needs to be resp...
Are BaaS Solutions the Answer to Spike in Ransomware Attacks?
With an ever-growing number of people working from home, primarily due to the global COVID-19 pandemic, cybersecurity attacks are on the rise, meaning that dealing with security risks is an ongoing journey for enterprises. IDC predicts that by 2023, 60% of data will be generated at the edge by people working from home and from devices outside of the corporate firewall. While at the same time, many corporate cloud services are already being rendered from locations outside the data centre. This has given rise to ransomware attacks as many employees who are working remotely have their firewalls and access points configured to allow remote access. This has also seen an increase in ransomware attacks against Software-as-a-Service (SaaS) applications. While SaaS applications are generally secure...
Are You Prepared to Prevent Data Loss?
Losing valuable data is one of the worst things that can happen to anyone – digitally, at least. Imagine losing critical data that you need to deliver a time-sensitive project with a deadline looming, like a school assignment – or documents needed when you’re applying for a grant, or even a freelance job you’ve taken on. The team at ESET, global leaders in cybersecurity, dissect the various aspects of not having a backup when experiencing data loss, and what to do in case that happens to you. What are the impacts of data loss? The impact of data loss may vary depending on what kind of data is lost, and when during your process it happens. And of course, the amount of time spent trying to recover it or trying to recreate it. Had you regularly backed up all the important data during yo...
Research Shows an Increase in Ransomware Attacks on South African Companies
South Africa is firmly in the sights of international cybercrime syndicates, who have been ramping up their attacks on local companies in the past six months – reveals cybersecurity defence, offence and protection specialist, Nclose. Martin Potgieter, Co-Founder of Nclose, says the Nview MDR team have detected a significant uptick in the number of attempts made against local customers in recent months. “We, and our colleagues in the cybersecurity sector, are seeing a surge in cybercrime activity – in particular ransomware attacks,” he says. “There has definitely been an increase in syndicates that make use of humans to launch and coordinate their attacks, they are not just relying on automated ransomware attacks.” Stephen Osler, Co-Founder at Nclose, says South African companies typical...
What is Cyber Doxxing and How to Protect Against It
Since the beginning of internet errors, a lot of personal details is revealed. Publishing personal data online may be very dangerous. The internet is a pool where you will find all sorts of people including hackers, cyberbullies, and other people with defamatory intentions. Such people collect and publish personal information with a bad intention. When this is done, it is known as Doxxing. Doxxing comes from the word “documents” with the act of documenting another person’s information. Criminals dig up personal details of an individual who wants to remain anonymous and expose them to the public. The main aim is to harass or shame the person. Although details like email addresses, phone numbers, and social security numbers are available online, there are other details like pictures, financi...