cybersecurity
Can You Hack-Proof the Cloud?
The cost and impact of cybercrime are climbing by around 15% every year, according to a 2020 report in Cybercrime Magazine, and is expected to cost $10,5 trillion globally by 2025. This makes cybercrime, they argue, more profitable than the global illegal drug trade. The real costs are far greater though, both broadly and to individual companies, as these funds represent lost investment and innovation, and companies increasingly face stringent fines for personal data losses under regulations such as the General Data Protection Regulation (EU GDPR) and Protection of Personal Information (PoPI) Act. The human layer All it takes is a chink in the armour, warns John Ward, SME of Cloud Business for Africa at Fortinet, and this can be through human error, misconfiguration, permissions-...
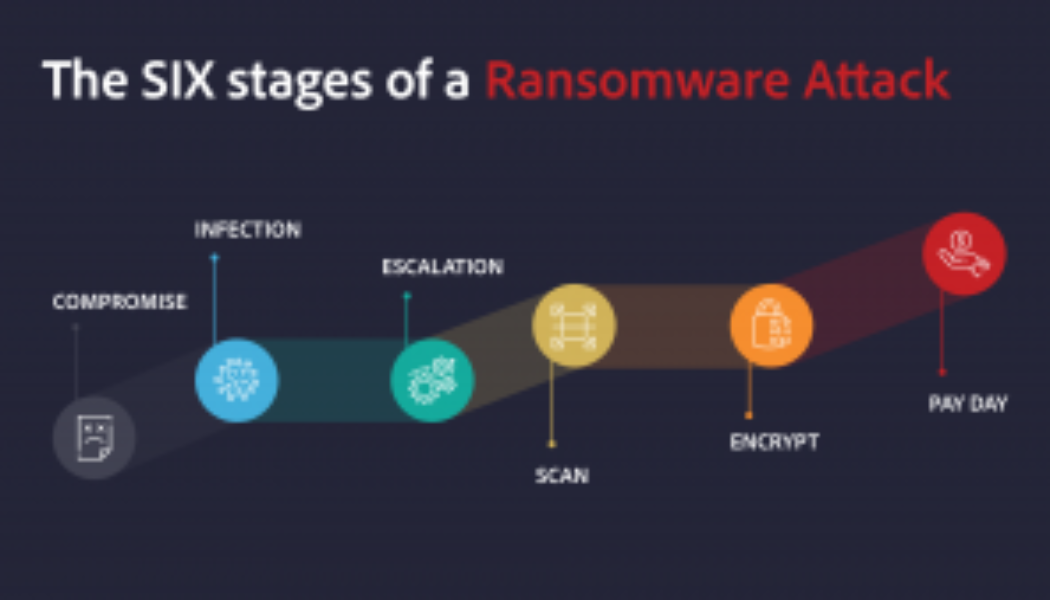
Unpacking Lessons from Ransomeware Attacks in 2021
It’s nearly impossible to read the news without seeing at least one headline blaring about a breach, hack or attack. In the USA, the Colonial Pipeline experienced a Darkside ransomware attack that affected more than 10, 000 gas stations. Virgin Active was hit by a hack in early May 2021 and took weeks to re-establish its systems. Vastaamo, a platform that provided therapy to thousands of patients, lost its data to hackers thanks to an unexpected security flaw. The hackers sent ransom demands to patients – pay up, or your personal information is public knowledge. As Stephen Osler, Co-Founder and Business Development Director at Nclose, points out, the criminal networks and masterminds behind digital attacks are doing their jobs and have every motivation to do these jobs extremely well. “The...
Beware of this New SMS Phishing Scheme Spreading Worldwide
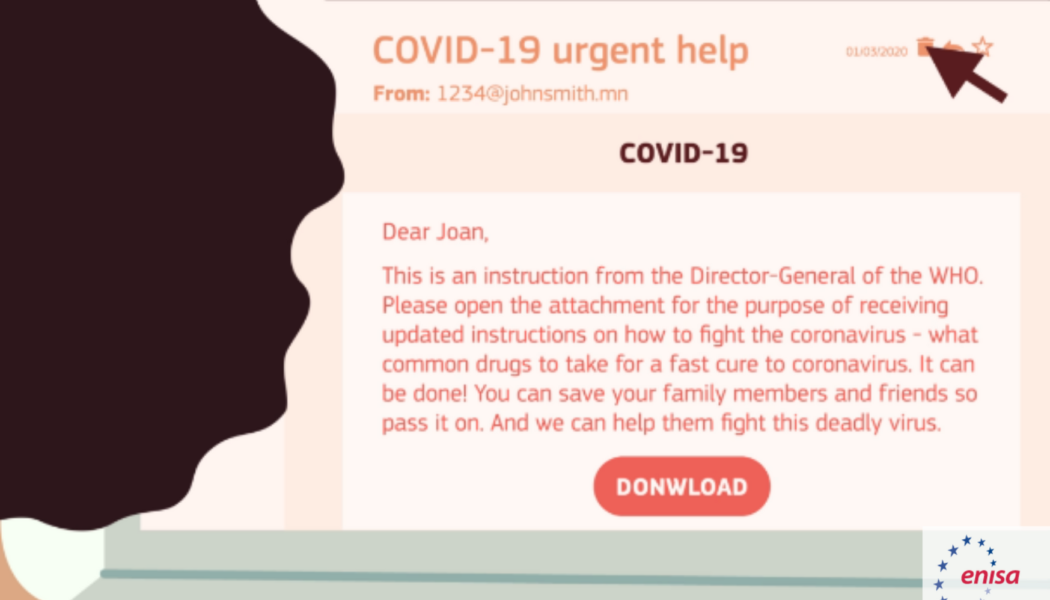
A new, and viral, phishing scheme has seen fraudsters putting mobile users’ financial information at risk, according to Kaspersky. The cybersecurity company revealed that attackers, typically under the guise of a postal service, request a small sum of money for the shipping costs of a package. Once a user clicks on an SMS authentication code for the money transfer, the device is compromised thereby enabling increasingly larger amounts of money to be stolen. “Because it is not a complex phishing attack, it has already gained traction in other parts of the world with fraudsters able to pose as virtually any service provider from prepaid electricity to airtime, naming just a few examples,” says Bethwel Opil, Enterprise Sales Manager at Kaspersky in Africa. Phishing, regardless of the scheme u...
Should West African Businesses Embrace Mobile Authentication for Security?
Sourced from International IDEA Digital technology has not only profoundly altered the way we live our lives, but also changed the pace of communication and commerce, allowing us to do everything, immediately. While this has effectively impacted every aspect of our lives, it also inevitably changed the way we are targeted by fraudsters. Along with the world transforming to digital, so has crime. According to an Accenture report published in 2019, the total value at risk of cybercrime over the next five years is an estimated $5.2 trillion. The average cyberattack costs $13 million, according to the same report, with phishing, social engineering and stolen device crime making up $2.4 million of the cost of an average attack. In West Africa, cybercrime is on the increase, with a recent analys...
Ireland’s health service IT systems shut down by ransomware attack
Ireland’s health service said it was under a ransomware attack on Friday that forced it to shut down its computer systems. A ransomware attack locks users out of their computer systems until they pay a fee to the intruder. There were few details, but the attack was described as significant by Ireland’s Health Service Executive. Motorists line up for fuel at one of the few remaining gas stations that still has fuel in Arlington, Virgina, on May 13, 2021. AFPBiden says oil pipeline back in operation after cyber attack It said it was shutting down all its IT systems to protect them from the attack while it consulted security partners. Covid-19 vaccinations would still go ahead as planned, the agency said. “We apologise for inconvenience caused to patients and to the public and will give furth...
Why People Should Invest in a Culture of Zero Trust Security
Sourced from International IDEA During a preview of this year’s RSA conference, a team from Orange Cyberdefense demonstrated a range of pretty scary scenarios of what can happen when malicious actors take control over a user’s home router. These range from duping users into downloading payloads dressed up as fake VPN software updates, capturing user’s credentials or redirecting traffic that should be going over the VPN to the threat actor. Typically, home routers are outside of the enterprise security control and often not very well protected. The majority of people trust their ISP to set up their home access points for them, frequently resulting in default settings such as admin/admin credentials. Home routers are frequently attacked by criminal and state actors alike. Despite the easing ...
Whitepaper: Protecting Electronic Personal Health Information Through Access Rights Management
Summary The Health Insurance Portability and Accountability Act of 1996 (HIPAA) defines a number of requirements for your organization in order to secure personal health information (PHI). In this paper, you will be introduced to an access rights management service portfolio, the five titles of the HIPPA, and how SolarWinds Access Rights Manager can help you meet central HIPAA requirements. Data Theft in the Health Sector Based on the 2018 Healthcare Cybersecurity Report1 the healthcare industry ranks fifteenth when compared to 17 major U.S. industries. According to the report’s findings, even “top performers” struggle with network security. The U.S Department of Health and Human Services estimates that over 40 percent of privacy violations in the healthcare sector are caused by hacking or...