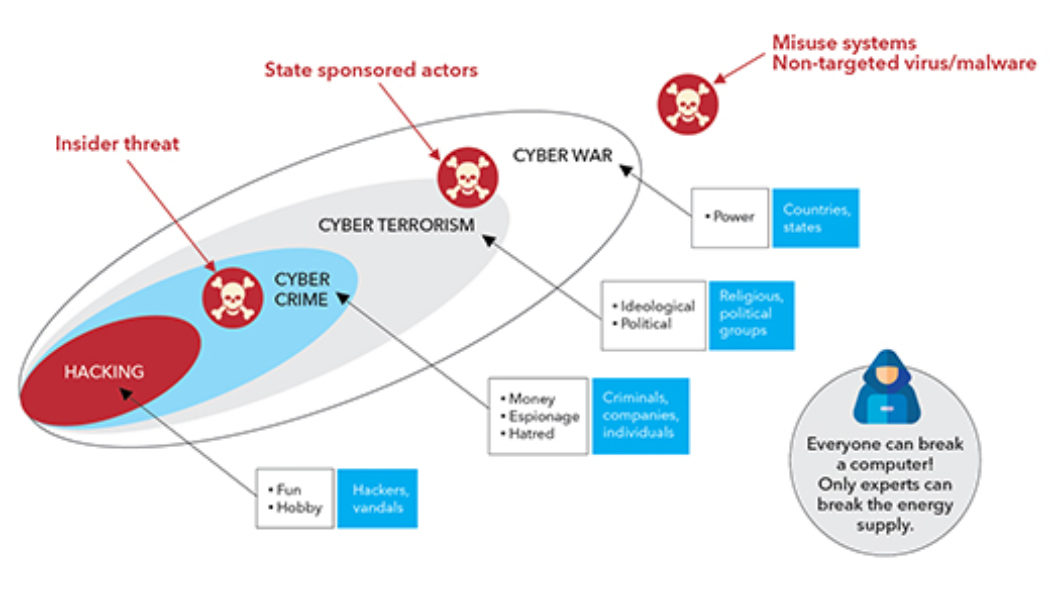
cybersecurity
IoT is One of Medicine’s Biggest Tools – Also Its Weakest Security Link
Image sourced from HP Consultant. /* custom css */ .tdi_4_0e2.td-a-rec-img{ text-align: left; }.tdi_4_0e2.td-a-rec-img img{ margin: 0 auto 0 0; } Healthcare has always been on the cutting edge, with hospitals and healthcare providers typically quick to embrace any innovation that will translate into better, more efficient, more affordable care. From microscopic pill cameras and implantable devices to laser surgery and advanced monitoring techniques, medical technology is all about creating the best possible patient outcome. But when it comes to the latest wave of innovative products, powered by always-on, always-connected internet of things (IoT) technology, there are growing concerns that security issues may eventually harm medical institutions or the patients themselves. /* custom css */...
Is Cybersecurity as Necessary as Electricity?
Sourced from Travellers Cybersecurity has become as much a business necessity as having electricity says South African financial services and insurance company, Sanlam. Threat actors are constantly evolving and relentlessly hunting for vulnerabilities, cybercrime has become so profitable that exploitation is their business priority, and regulation is increasingly complex to navigate and manage. For Sanlam, cybersecurity has always been more than plugging holes and filling gaps, it’s a priority that has to be embedded within business foundations while managing cost, growth, customer experience, data analytics and regulatory controls. “Developing a comprehensive and holistic cybersecurity solution is a mandate for us, one that we must meet to ensure customer, stakeholder and industry trust. ...
Kaspersky Discovers Various Malicious Apps Disguising as Bestselling Game Minecraft
Sourced from Stuff. Recognised as the world’s top-selling game of all time, Minecraft attracts the attention of enthusiastic players around the world but also draws the interest of fraudsters. Earlier, Kaspersky researchers discovered more than 20 applications advertised on app stores offering additional Minecraft features. Though these malicious apps were deleted from official stores, Kaspersky experts have found newly developed ones, which exploit the game to further fraudster’s objectives. Malware on Google Play Store Kaspersky researchers analysed various apps, including those which are available for download on the Google Play store and claimed to be modpacks (user-created packages with additional gameplay elements) for the game. As a result, the company’s experts found various malici...
Confidential Computing – Why Privacy Should be the Heart of Digital Experiences
Image sourced from Intel. In this past year, the consumer experience came to the forefront. As we faced various stages of lockdowns, we turned to online banking, seeing our doctors remotely, running our businesses using technology and socialising through a screen. Digital interactions became a part of our lives – ever-present and normalised as we navigated changes swept in by this pandemic. As our digital interaction became seamless and permeated through every aspect of our lives, privacy continued to be top of mind. We carried out our lives predominantly online – making many of us more vulnerable to fraudsters. As we navigated living our lives digitally, data theft dominated 2020 as the most common attack in the Middle East and Africa. Across the region, data theft and leaks accounted for...
Why Immutable Architecture is Key to Protecting Backup Data
Ransomware and other malware are a constant threat, and data backup is critical to safeguard a business’ most important asset. However, cybercriminals are increasingly targeting and encrypting backup data copies as well, a strategy that leaves organisations unable to recover unless they pay the ransom. Keeping an immutable copy of backup data is a best practice for data protection and is the solution in the event of a successful two-pronged ransomware attack. What is an immutable architecture? For data to be immutable means that it is unable to be changed over a period of time. With an immutable architecture, when retention policies are set for data backup and recovery, data will be secured, locked and unchangeable for that retention period. This in turn means that it cannot be encrypted b...