cybersecurity
Solana Foundation warns about security incident with Mailchimp
Solana Foundation, the non-profit organization of the Solana Network, disclosed on Jan. 14 a security incident involving its email service provider Mailchimp. According to an email sent to users and seen by Cointelegraph, the Foundation was informed by Mailchimp on Jan. 12 that “an unauthorized actor accessed and exported certain user data from the Solana Foundation’s Mailchimp instance.” Among the information accessed and exported in the incident were user’s names and Telegram usernames. The Solana Foundation stated: “Based on the information we have received from Mailchimp, the affected information may have included, inter alia, email addresses, names, and Telegram usernames, in each case only to the extent users provided any such information. Mailchimp advi...
Solana Foundation warns about security incident with Mailchimp
Solana Foundation, the non-profit organization of the Solana Network, disclosed on Jan. 14 a security incident involving its email service provider Mailchimp. According to an email sent to users and seen by Cointelegraph, the Foundation was informed by Mailchimp on Jan. 12 that “an unauthorized actor accessed and exported certain user data from the Solana Foundation’s Mailchimp instance.” Among the information accessed and exported in the incident were user’s names and Telegram usernames. The Solana Foundation stated: “Based on the information we have received from Mailchimp, the affected information may have included, inter alia, email addresses, names, and Telegram usernames, in each case only to the extent users provided any such information. Mailchimp advi...
App-specific blockchains remain a promising solution for scalability
App-specific blockchains, or appchains, are specifically designed to support the creation and deployment of decentralized applications (DApps). In an appchain, each app runs on its separate blockchain, linked to the main chain. This allows for greater scalability and flexibility, as each app can be customized and optimized for its specific use case. Appchains are also an alternative solution for scalability to modular blockchains or layer-2 protocols. Appchains present similar characteristics to modular blockchains, as it is a type of blockchain architecture that separates the data, transaction processing and consensus processing elements into distinct modules that can be combined in various ways. These can be thought of as “pluggable modules” that can be swapped out or combined depending ...
DeFi-type projects received the highest number of attacks in 2022: Report
It’s no secret that in 2022 the world of Web3 and decentralized finance (DeFi) experienced a slew of major exploits and attacks. From the Ronin bridge attack to the Nomad hack, the top 10 exploits alone saw over $2 billion lost. In the Beosin Global Web3 Security Report 2022, it revealed that of 167 major security incidents over the last year those rooted in DeFi were the most vulnerable. DeFi projects were attacked 113 times, which accounted for approx. 67.6% of recorded attacks. This is followed by attacks on exchanges, nonfungible token (NFT) projects, cross-chain bridges and wallets in that order. According to the report, DeFi projects came in second in terms of monetary losses with a total of $950 million in losses. This follows the $1.89 billion lost in cross-chain bridge exploits in...
BitKeep exploiter used phishing sites to lure in users: Report
The Bitkeep exploit that occurred on Dec. 26 used phishing sites to fool users into downloading fake wallets, according to a report by blockchain analytics provider OKLink. The report stated that the attacker set up several fake Bitkeep websites which contained an APK file that looked like version 7.2.9 of the Bitkeep wallet. When users “updated” their wallets by downloading the malicious file, their private keys or seed words were stolen and sent to the attacker. 【12-26 #BitKeep Hack Event Summary】1/n According to OKLink data, the bitkeep theft involved 4 chains BSC, ETH, TRX, Polygon, OKLink included 50 hacker addresses and total Txns volume reached $31M. — OKLink (@OKLink) December 26, 2022 The report did not say how the malicious file stole the users’ keys in an unencrypted form. Howev...
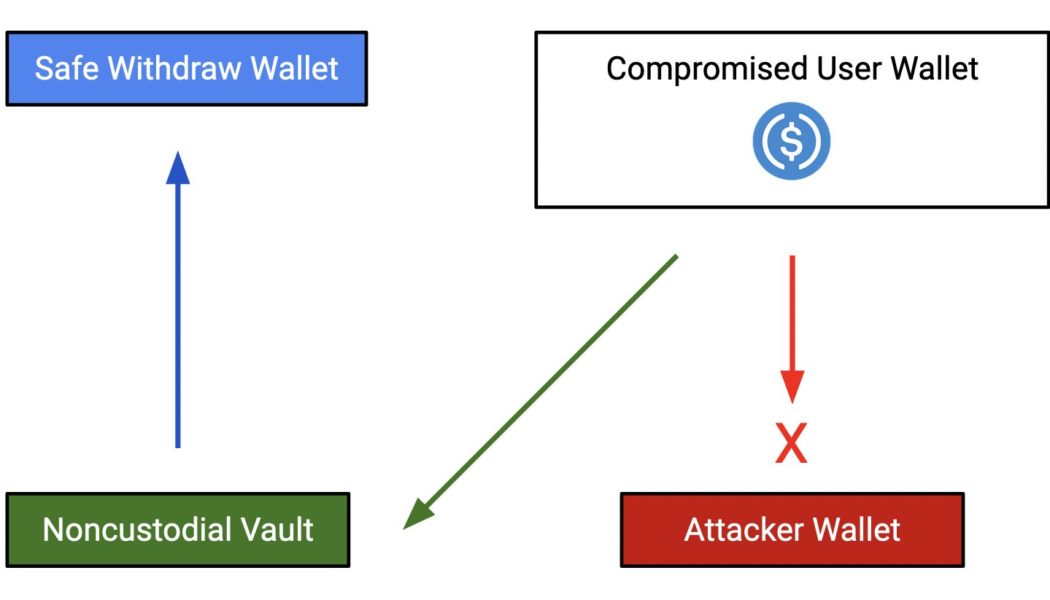
Crypto on-chain crime drama sees the good guys finally win
The stories about people getting their private keys hacked or stolen are nothing new, with a number losing their life savings because of these thefts. However, in quite an anti-climax scene, a crypto user managed to save their crypto holdings despite losing their private keys. Harpie, an on-chain security firm, revealed an instance of on-chain crime drama where the good guys eventually won. One of the users in their Discord group reportedly raised concerns about the suspected theft of their private keys. When the firm looked into said customer’s wallet, someone was indeed trying to transfer funds from the victim’s accounts. How did we do this? About a month ago, this user protected their tokens with Harpie. By approving and protecting their tokens with Harpie, this user gave us permis...
Developers need to stop crypto hackers — or face regulation in 2023
Third-party data breaches have exploded. The problem? Companies, including cryptocurrency exchanges, don’t know how to protect against them. When exchanges sign new vendors, most just innately expect that their vendors employ the same level of scrutiny as they do. Others don’t consider it at all. In today’s age, it isn’t just a good practice to test for vulnerabilities down the supply chain — it is absolutely necessary. Many exchanges are backed by international financiers and those new to financial technologies. Many are even new to technology altogether, instead backed by venture capitalists looking to get their feet wet in a burgeoning industry. In and of itself, that isn’t necessarily a problem. However, firms that haven’t grown up in the fintech arena often don’t fully grasp the exten...
Web3 is the solution to Uber’s problem with hackers
Uber is a staple of the gig economy, for better or worse, and a disruptor that once sent shockwaves throughout the mobility space. Now, however, Uber is being taken for a ride. The company is handling a reportedly far-reaching cybersecurity breach. According to the ride-hailing giant, the attacker has not been able to access sensitive user data, or at least, there is no evidence to suggest otherwise. Whether or not sensitive user data was exposed, this case points to a persistent issue with today’s apps. Can we continue to sacrifice our data — and thereby our privacy and security — for convenience? Web2, the land of hackable honeypots Uber’s track record for data breaches is not exactly spotless. Just in July, the ride-hailing giant acknowledged hushing up a massive breach in 2016 that lea...
US lawmakers propose amending cybersecurity bill to include crypto firms reporting potential threats
United States Senators Marsha Blackburn and Cynthia Lummis have introduced proposed changes to a 2015 bill that would allow “voluntary information sharing of cyber threat indicators among cryptocurrency companies.” According to a draft bill on amending the Cybersecurity Information Sharing Act of 2015, Blackburn and Lummis suggested U.S. lawmakers allow companies involved with distributed ledger technology or digital assets to report network damage, data breaches, ransomware attacks, and related cybersecurity threats to government officials for possible assistance. Should the bill be signed into law, agencies including the Financial Crimes Enforcement Network and the Cybersecurity and Infrastructure Security Agency would issue policies and procedures for crypto firms facing potential cyber...
SA’s Cybersecurity Professionals Feel They’re “Losing Ground” Against Cybercriminals – Study
Image sourced from Pixabay Less than 40% of South African security operations (SecOps) professionals are very confident in their ability to adapt to new online threats, with 34% only somewhat confident. While 18% are not confident in their ability to deal with continuously evolving threats, over 10% are undecided. This was part of a global research study released today by Trellix, the cybersecurity company delivering the future of extended detection and response (XDR), revealing the cost of siloed security, weak spots in protection and lack of confidence amongst SecOps teams. “Although South Africa is slightly ahead of the curve (relative to the global average) in its preparedness to deal with attacks, the number of threats is fast increasing, along with the stakes that attackers are playi...