cybersecurity trends
Is South Africa a Playground for Cybercriminals?
The Attacks From All Angles 2021 Mid-year Cybersecurity Report by Trend Micro highlighted a 47% year-on-year increase in email threats as well as malicious files and URLs in the first quarter of 2021 globally. South Africa’s technology landscape is almost identical to that of other countries, which has seen black hat hackers using it as a testing ground for cybersecurity attacks before these are launched on their intended end-users. Ransomware Remains the Prime Threat Globally, ransomware remained the standout threat in the first half of the year. The pandemic has highlighted how easy it is to buy ransomware as a service (Raas) on the dark web. Africa accounted for 1.7% of these attacks, with 1.05% being targeted at South Africa. Our findings show that locally, South Africa was in the top ...
How to Successfully Recover from a Ransomware Attack
Sourced from Kaspersky South Africa is an attractive target for cybercriminals for a number of reasons, and the last few years have seen a sharp rise in high-profile ransomware attacks. One of the key motivations driving this volume of attacks is the fact that data is a de facto currency and an extremely valuable commodity on the black market. While backup is a critical component of data protection, when this backup is also encrypted by malicious software, companies are often left with few options other than to pay the ransom. Therefore, an effective Cyber Recovery strategy, which enables businesses to get back up and running without having to give in to criminal demands, is the key. Ransomware on the Rise The rapid adoption of digital transformation, Artificial Intelligence (AI) and the I...
When Ransomware Strikes, Can You Recover Fast Enough?
Sourced from Kaspersky Ransomware attacks have become increasingly common, and they are even available on the dark Web to purchase as a service. There have been many incidents in the news, where major companies have been left with little choice other than to pay the ransom to get their data back, often amounting to hundreds of thousands of dollars. The reality is that ransomware and other cyberattacks have become a question of when not if. The ability to respond and recover quickly has therefore become an essential part of successful ransomware defence, but it is something many organisations, especially in South Africa, struggle with. Consider Some Statistics The State of Ransomware report from security firm Sophos reveals that, over the last year, the average cost of remediating a ransomw...
Cybersecurity Should Be a Top Priority for Africa’s Digital Transformation
Sourced from Travellers Cloud adoption in South Africa and many other African countries is accelerating, helped along by the COVID-19 workplace disruption, and the need to reduce costs, manage risk and scale, and become more competitive. There are many drivers behind digital transformation strategies and many decisions that need to be made, such as which public cloud to consume. However, this should be less urgent than addressing security concerns. As we continue to work with organisations in different industries spread across our diverse continent, cybersecurity and cyber risk are increasingly important considerations for the C-suite. Against the backdrop of high-profile security breaches and ransomware, addressing security weaknesses are a key part of the success of digital transformatio...
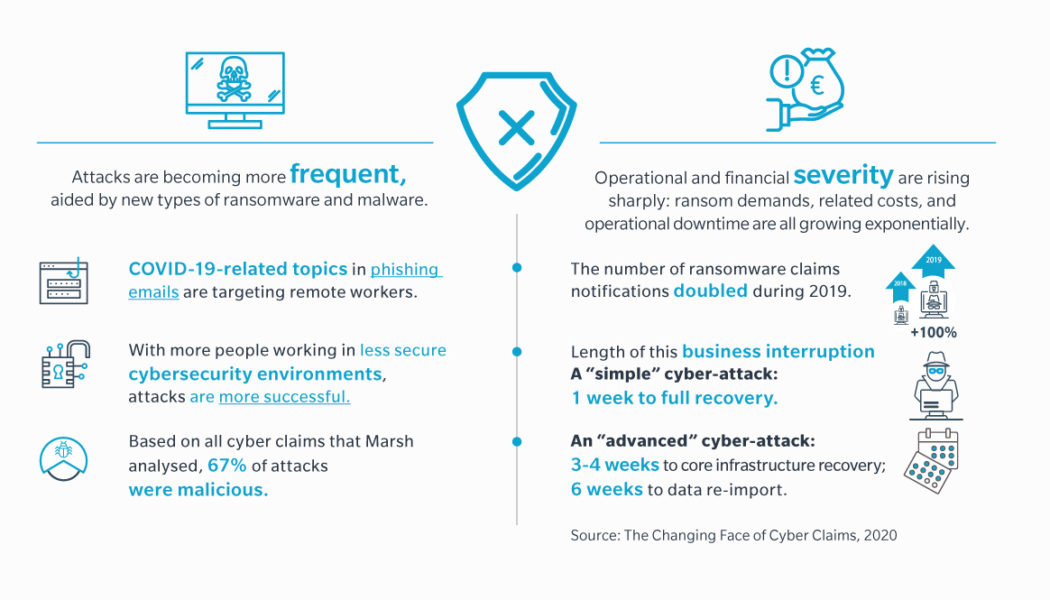
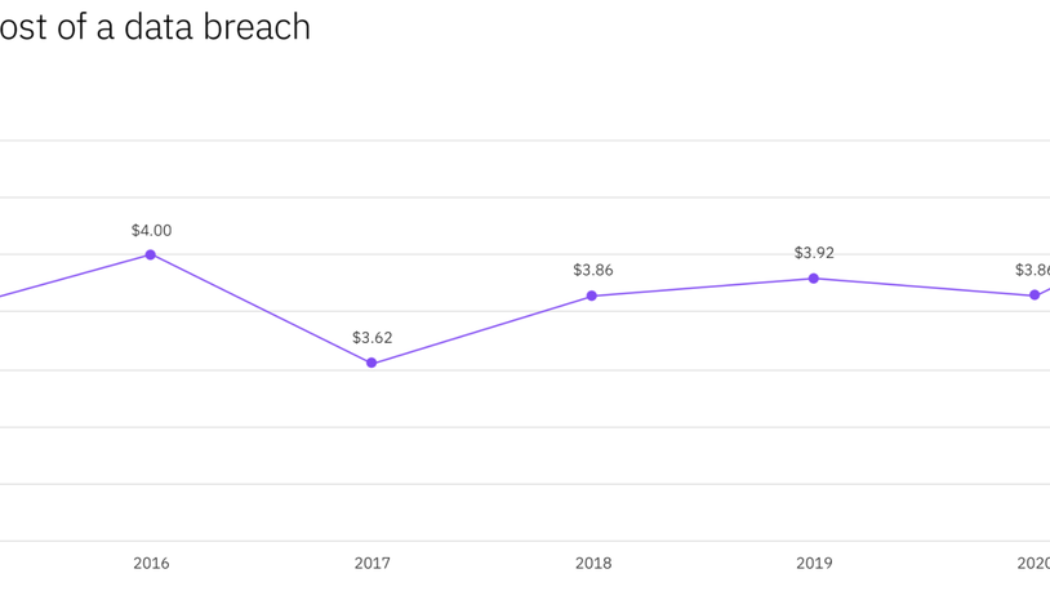
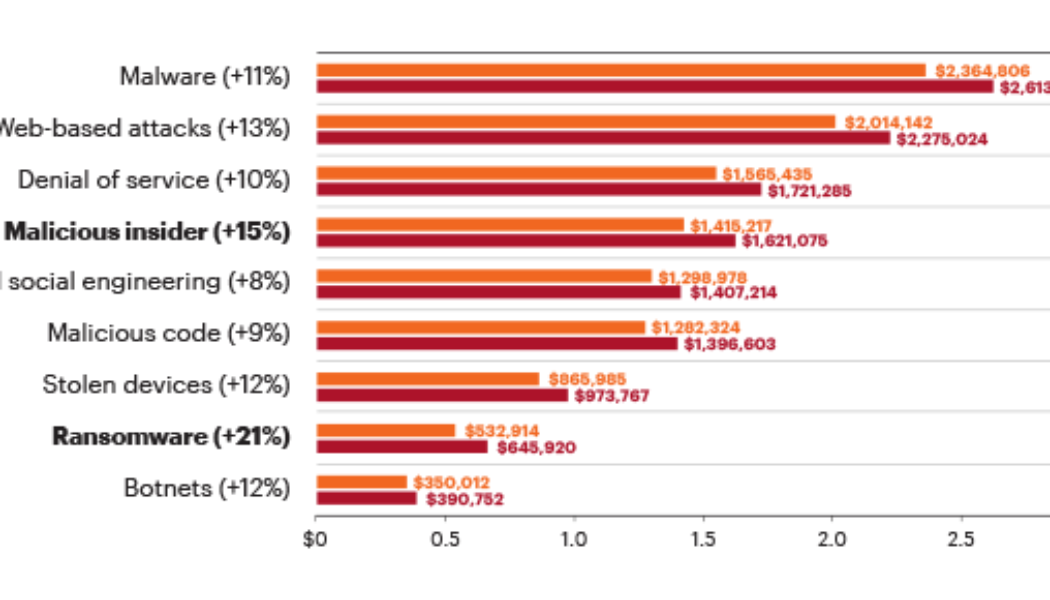
The High Cost of Cybercrime is Getting Higher
Image sourced from Finance Times. If cybercrime organizations could be publicly traded, we’d have an instant new multibillion-dollar industry sector. Indeed, cyber threats have become so pervasive that U.S. President Joe Biden recently signed an executive order aimed at improving federal cybersecurity in the wake of multiple significant cyberattacks, including the ransomware attack that shut down the Colonial Pipeline. Meanwhile, a broad coalition of experts in the industry, government, law enforcement, civil society, and international organizations have joined together in the Ransomware Task Force to build a framework for combatting ransomware. Ransomware attacks are only one method, however. Threat actors also use distributed denial-of-service (DDoS) attacks to ratchet up the p...
33% of Companies Undergo Cyberattacks Twice a Month on Average, per Report
Sourced from International IDEA The Hiscox Cyber Readiness Report 2021 provided some concerning statistics and facts about the impact of cyber-crime. It is a game, and it is one that Hiscox fundamentally believes no business should leave to chance. Multiple threat vectors and variable threat actors, and, perhaps most worrying – repeated attacks on companies by cyber-crime pose a serious risk to organisations small and large alike. One-in-six of all firms attacked this year (17%) said the impact was serious enough to ‘materially threaten the solvency or viability of the company’. According to Anna Collard, SVP Content Strategy & Evangelist at KnowBe4 AFRICA, the report underscores the immense challenge that organisations face when it comes to securing the business and the people within ...
Gijima’s Shubna Harilal Talks Women in Tech, Digital Transformation and Tech’s Next Big Thing
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent. You Deserve to Make Money Even When you are looking for Dates Online. So we reimagined what a dating should be. It begins with giving you back power. Get to meet Beautiful people, chat and make money in the process. Earn rewards by chatting, sharing photos, blogging and help give users back their fair share of Internet revenue.
- 1
- 2