Cybersecurity Tips
Is Hacking Humans Easier Than Machines?
Anna Collard, SVP Content Strategy & Evangelist at KnowBe4 Africa. When it comes to cybersecurity, technology is not enough. Yes, it is the foundation. But it is not enough to mitigate the growing threat of cybercrime. The reality is that, even with best-in-class security systems, firewalls, endpoint protections and zero-trust frameworks, without a robust and agile culture of security, the business is at risk. The Dark Reading 2021 Strategic Security Survey found that around 48% of security professionals believe that users breaking policy are likely to be the single biggest cause of a major breach in the future. This sentiment is echoed in a ITWeb and KnowBe4 study that examined cybersecurity culture and the impact of this on the South African organisation. “Having a robust cyber...
Why Ransomware is the Greatest Threat to Your Organisation
Ransomware is getting nastier and more expensive all the time and it has affected almost every industry and geography. No one is immune from the threat. In a global ransomware survey conducted by Fortinet, 67% of organizations report suffering a ransomware attack. Even worse, almost half said they had been targeted more than once, and nearly one in six said they had been attacked three or more times. Renee Tarun, Deputy CISO/ Vice President Information Security, Fortinet Inc. The US Treasury’s Financial Crimes Enforcement Network (FinCEN) reported that organizations paid out almost $600 million in ransomware in the first half of 2021, which puts the US on track to surpass the combined payouts of the previous decade in a single year. Last year’s attacks on the suppl...
1 in 4 People Use Fitness Devices – Is Your Tracking Data Secure from Hackers?
Image sourced from Reuters. A recent study by the virtual private network provider NordVPN revealed that 1 in 4 (24.6%) people use some kind of fitness or well-being device, such as a smartwatch, fitness tracker, etc. However, these devices may be tracking a lot more than your fitness activities, and 25% do nothing to protect them, which may pose a serious risk to people’s privacy. Among the data collected by fitness wearables and the mobile apps connected to them, there are basic activities such as steps, heart rate, the time you go to sleep or wake up, as well as your consumed calories, weight, or even running routes, which are all of great interest to stalkers or attackers. For example, Clario research has revealed that Strava collects 41.18% of users’ personal data, and MyFitnessPal — ...
Cybersecurity Should Be a Top Priority for Africa’s Digital Transformation
Sourced from Travellers Cloud adoption in South Africa and many other African countries is accelerating, helped along by the COVID-19 workplace disruption, and the need to reduce costs, manage risk and scale, and become more competitive. There are many drivers behind digital transformation strategies and many decisions that need to be made, such as which public cloud to consume. However, this should be less urgent than addressing security concerns. As we continue to work with organisations in different industries spread across our diverse continent, cybersecurity and cyber risk are increasingly important considerations for the C-suite. Against the backdrop of high-profile security breaches and ransomware, addressing security weaknesses are a key part of the success of digital transformatio...
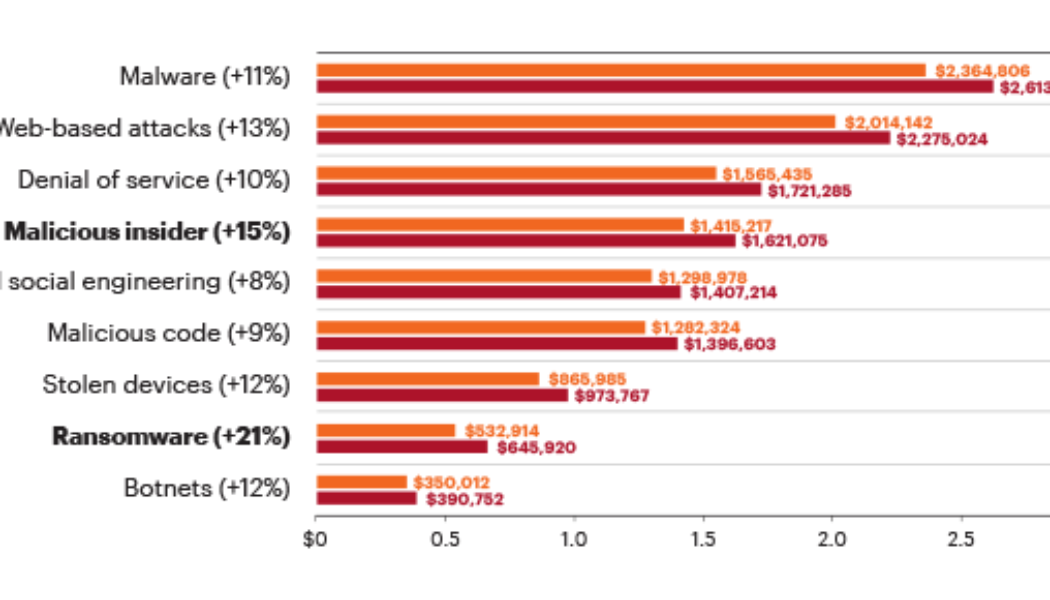
The High Cost of Cybercrime is Getting Higher
Image sourced from Finance Times. If cybercrime organizations could be publicly traded, we’d have an instant new multibillion-dollar industry sector. Indeed, cyber threats have become so pervasive that U.S. President Joe Biden recently signed an executive order aimed at improving federal cybersecurity in the wake of multiple significant cyberattacks, including the ransomware attack that shut down the Colonial Pipeline. Meanwhile, a broad coalition of experts in the industry, government, law enforcement, civil society, and international organizations have joined together in the Ransomware Task Force to build a framework for combatting ransomware. Ransomware attacks are only one method, however. Threat actors also use distributed denial-of-service (DDoS) attacks to ratchet up the p...
33% of Companies Undergo Cyberattacks Twice a Month on Average, per Report
Sourced from International IDEA The Hiscox Cyber Readiness Report 2021 provided some concerning statistics and facts about the impact of cyber-crime. It is a game, and it is one that Hiscox fundamentally believes no business should leave to chance. Multiple threat vectors and variable threat actors, and, perhaps most worrying – repeated attacks on companies by cyber-crime pose a serious risk to organisations small and large alike. One-in-six of all firms attacked this year (17%) said the impact was serious enough to ‘materially threaten the solvency or viability of the company’. According to Anna Collard, SVP Content Strategy & Evangelist at KnowBe4 AFRICA, the report underscores the immense challenge that organisations face when it comes to securing the business and the people within ...
Why Immutable Architecture is Key to Protecting Backup Data
Ransomware and other malware are a constant threat, and data backup is critical to safeguard a business’ most important asset. However, cybercriminals are increasingly targeting and encrypting backup data copies as well, a strategy that leaves organisations unable to recover unless they pay the ransom. Keeping an immutable copy of backup data is a best practice for data protection and is the solution in the event of a successful two-pronged ransomware attack. What is an immutable architecture? For data to be immutable means that it is unable to be changed over a period of time. With an immutable architecture, when retention policies are set for data backup and recovery, data will be secured, locked and unchangeable for that retention period. This in turn means that it cannot be encrypted b...