Cybersecurity news
Kaspersky Discovers Various Malicious Apps Disguising as Bestselling Game Minecraft
Sourced from Stuff. Recognised as the world’s top-selling game of all time, Minecraft attracts the attention of enthusiastic players around the world but also draws the interest of fraudsters. Earlier, Kaspersky researchers discovered more than 20 applications advertised on app stores offering additional Minecraft features. Though these malicious apps were deleted from official stores, Kaspersky experts have found newly developed ones, which exploit the game to further fraudster’s objectives. Malware on Google Play Store Kaspersky researchers analysed various apps, including those which are available for download on the Google Play store and claimed to be modpacks (user-created packages with additional gameplay elements) for the game. As a result, the company’s experts found various malici...
Confidential Computing – Why Privacy Should be the Heart of Digital Experiences
Image sourced from Intel. In this past year, the consumer experience came to the forefront. As we faced various stages of lockdowns, we turned to online banking, seeing our doctors remotely, running our businesses using technology and socialising through a screen. Digital interactions became a part of our lives – ever-present and normalised as we navigated changes swept in by this pandemic. As our digital interaction became seamless and permeated through every aspect of our lives, privacy continued to be top of mind. We carried out our lives predominantly online – making many of us more vulnerable to fraudsters. As we navigated living our lives digitally, data theft dominated 2020 as the most common attack in the Middle East and Africa. Across the region, data theft and leaks accounted for...
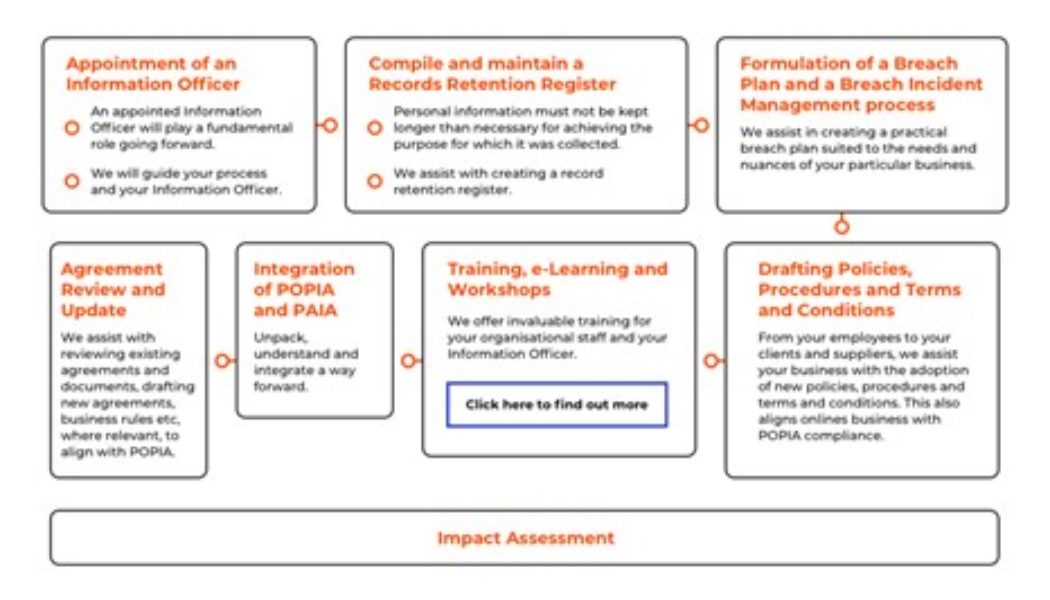
What is POPIA and What Does it Mean for Cybersecurity
With an inundation of information from all angles regarding The Protection of Personal Information Act (POPIA), and the 1 July commencement date quickly approaching, organisations could be forgiven for feeling more than a little overwhelmed. Emmanuel Tzingakis, Technical Lead for Trend Micro Sub-Saharan Africa, contemplates how POPIA can assist organisations to secure their data and be better enabled to handle any potential cyber threats. What is POPIA? With personal information becoming a hot commodity on the dark web it is critical to understand exactly how to protect data from cybercriminals. A recent global survey revealed that 79% of organisations experienced disruptions, financial loss or other setbacks due to a lack of cyber preparedness in 2020. As work from home strateg...
Why Immutable Architecture is Key to Protecting Backup Data
Ransomware and other malware are a constant threat, and data backup is critical to safeguard a business’ most important asset. However, cybercriminals are increasingly targeting and encrypting backup data copies as well, a strategy that leaves organisations unable to recover unless they pay the ransom. Keeping an immutable copy of backup data is a best practice for data protection and is the solution in the event of a successful two-pronged ransomware attack. What is an immutable architecture? For data to be immutable means that it is unable to be changed over a period of time. With an immutable architecture, when retention policies are set for data backup and recovery, data will be secured, locked and unchangeable for that retention period. This in turn means that it cannot be encrypted b...