Cybersecurity news
Cyber Threats on the Rise in Mining & Manufacturing Industries
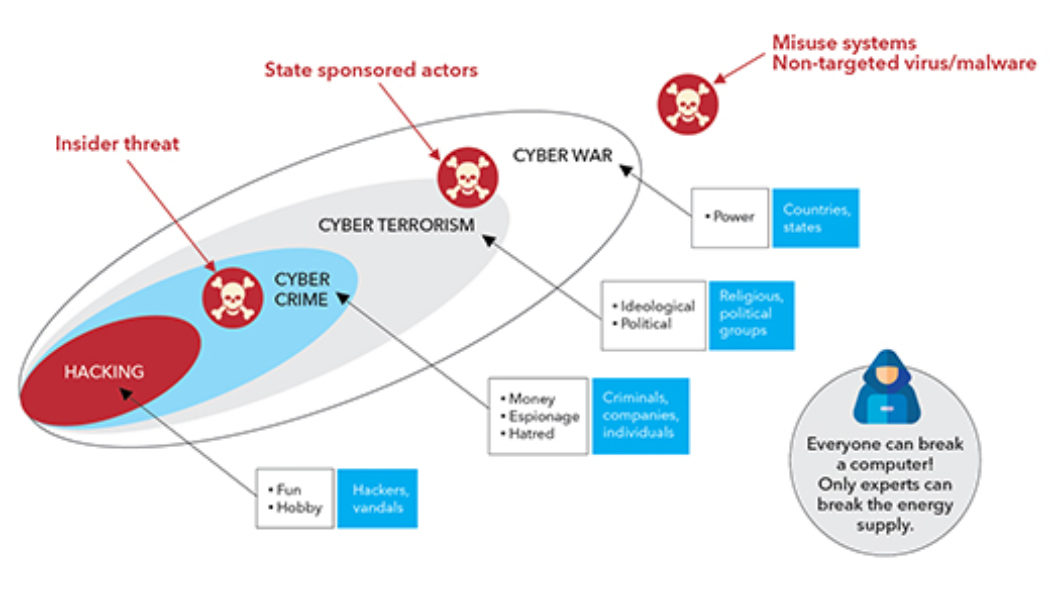
Image sourced from Software ONE. Increasingly companies are looking to adopt smart technologies to optimise production and decision-making in order to create businesses of the future. However, as reliance on autonomous and digital technology grows, so too does the risk of cyber-attacks. As technologies become more interconnected, the potential cybersecurity threats and attack vectors are growing. The consequences of these threats can be severe, resulting in production and revenue losses, regulatory fines, reputational damage, as well as the shutdown of critical infrastructures. This has been further compounded by the complexities and uptake of smart systems that use advanced technologies such as machine learning and the Internet of Things (IoT). Mining, Manufacturing Under Threat Termed ‘S...
Surging DDoS Attacks Drive Growing Demand for Third Party Protection Services
Image sourced from Shutterstock. As the global workforce largely shifted to work-from-home in response to the COVID-19 pandemic, reliance on online services soared. Many businesses were able to successfully pivot to this new normal as remote connectivity allowed access to vital systems and data. But as is often the case, no good deed goes unpunished. As the latest NETSCOUT Threat Intelligence Report shows, cybercriminals have exploited new vulnerabilities created by remote work across a wide variety of vertical industries. Making matters worse, perpetrators no longer have to be particularly technology-savvy in order to pull off attacks. Today, it is easy and relatively inexpensive to access sophisticated attack tools via for-hire services: A cottage industry has sprung ...
Recent Increases in Cyberattacks Could Be Due to Leaked Cyber “Superweapons”
Sourced from Forbes Check Point Research (CPR), the Threat Intelligence arm of Check Point Software Technologies Ltd., a leading provider of cybersecurity solutions globally, warns of a further increase in cyberattacks and thinks it could be partly down to major powers leaking, what they refer to as, ‘cyber superweapons’. “We have long warned that organisations of all sizes are being bombarded by a global fifth generation of cyber threats (Gen V). These are multi-vector cyber threats that can cause fatal damage and irreparable harm to the reputation of the compromised company,” said Pankaj Bhula, Regional Spokesperson at Check Point Software. “However, most companies are only secured against what we call third-generation threats (Gen III), which are threats that we’ve known about since the...
Broken Endpoints in Your Organisation’s Cybersecurity: The Role of Superior Endpoint Detection
Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited. Networks Unlimited is applying a ‘broken window, broken business’ principle when looking at an organisation’s internal cybersecurity posture, in order to have a positive effect on its business processes. The moral of the ‘broken window’ story, which has been studied by psychologists, is that once a window in a building is broken, people then feel that they are able to damage the property even further, and ultimately loot and steal from it, with impunity. “When we put this into a cybersecurity context,” says Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited, “this means, in essence, making sure that you have no ‘broken windows’ or gaps in your security through which uninvited elements coul...
Is Cybersecurity as Necessary as Electricity?
Sourced from Travellers Cybersecurity has become as much a business necessity as having electricity says South African financial services and insurance company, Sanlam. Threat actors are constantly evolving and relentlessly hunting for vulnerabilities, cybercrime has become so profitable that exploitation is their business priority, and regulation is increasingly complex to navigate and manage. For Sanlam, cybersecurity has always been more than plugging holes and filling gaps, it’s a priority that has to be embedded within business foundations while managing cost, growth, customer experience, data analytics and regulatory controls. “Developing a comprehensive and holistic cybersecurity solution is a mandate for us, one that we must meet to ensure customer, stakeholder and industry trust. ...