Cybersecurity news
How a Data Breach Could Sink an SME
Sourced from CSO. When it comes to reporting on cybercrime, we tend to only come across stories impacting major companies or industries. Apart from the obvious reputational damage, we don’t really grasp the consequences of something like a data breach on a company and its customers. There are no headline articles about the troubles that emerge in the wake of a data breach, some of which literally grind small and medium enterprises (SMEs) into the ground. The media focuses on corporate giants as the only victims of cybercrime and lulls us into a false reality where data breaches seem to happen mostly to corporate behemoths but not the small or medium size business owners. Cybercriminals, who are often well-organised and well-resourced, launch constant attacks on data targets, probing for th...
SA’s Cybersecurity Professionals Feel They’re “Losing Ground” Against Cybercriminals – Study
Image sourced from Pixabay Less than 40% of South African security operations (SecOps) professionals are very confident in their ability to adapt to new online threats, with 34% only somewhat confident. While 18% are not confident in their ability to deal with continuously evolving threats, over 10% are undecided. This was part of a global research study released today by Trellix, the cybersecurity company delivering the future of extended detection and response (XDR), revealing the cost of siloed security, weak spots in protection and lack of confidence amongst SecOps teams. “Although South Africa is slightly ahead of the curve (relative to the global average) in its preparedness to deal with attacks, the number of threats is fast increasing, along with the stakes that attackers are playi...
Infoblox Global Survey Sheds Light on Protecting the Network from Blind Spots
A 2022 global state of security survey from Infoblox, the leader in cloud-first networking and security services, highlights the security concerns, fears, and costs from 1,100 IT respondents in the United States, Mexico, Brazil, United Kingdom, Germany, France, the Netherlands, Spain, United Arab Emirates, Australia, and Singapore. “The hybrid workplace is more reliant than ever on cloud-first technologies, but blind spots have emerged,” says Aric Ault, Senior Director of Channel for Infoblox EMEA. “The explosion of employee-owned technologies on the corporate network feeds IT teams’ growing fears over losing direct security controls and network visibility. This has become all the more concerning as breach costs top 1 million USD for 43 percent of surveyed organisations.” Ruan du Preez, Ve...
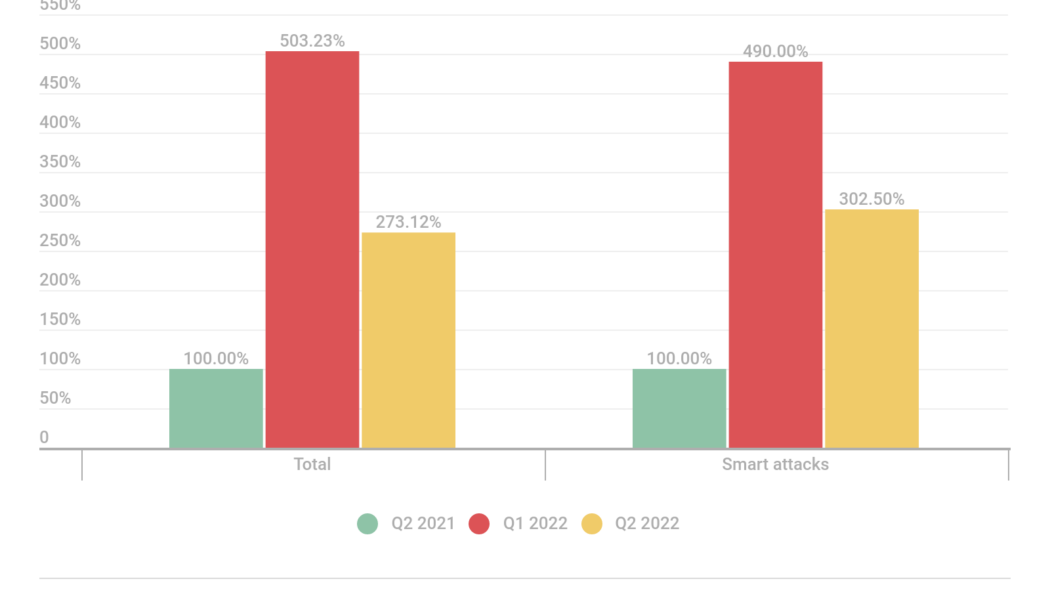
The Crypto Collapse & Rising DDoS Smart Attacks
Image sourced from Shutterstock. During Q2 2022, Distributed Denial of Service (DDoS) attacks reached a new level as the share of smart attacks and average duration saw steep increases. Compared to the previous year, the average duration of a DDoS attack rose 100 times, reaching 3,000 minutes. The share of smart attacks almost broke the four-year record, accounting for nearly 50% of the total. Experts also expect an increase in overall DDoS activity, especially with the recent collapse of cryptocurrency. These and other findings are part of a quarterly DDoS report issued by Kaspersky. A Distributed Denial of Service (DDoS) attack is designed to hinder the normal functioning of a website or crash it completely. During an attack (which usually targets government institutions, retail or ...