Cybersecurity Awareness
Awareness and Training Are Key in Defending Your Company from Blended Cyber-Threats
Image sourced from Finance Times. While blended cybersecurity threats are not new, they are fairly sophisticated and multi-staged in nature, meaning that they are difficult to protect against and can pose a considerable threat to organisations’ IT environments. A blended threat typically uses and exploits multiple vulnerabilities in an attack chain, says Brian Pinnock, Senior Director of Sales Engineering (EMEA) at Mimecast, adding that the severity of a blended threat will depend on the specific vulnerabilities that are targeted. “For example, a threat actor or cybercriminal will launch a phishing campaign against an organisation by sending emails with infected links that redirect to malicious websites. When a user clicks on these links, they could download a piece of malware like a Troja...
Can You Hack-Proof the Cloud?
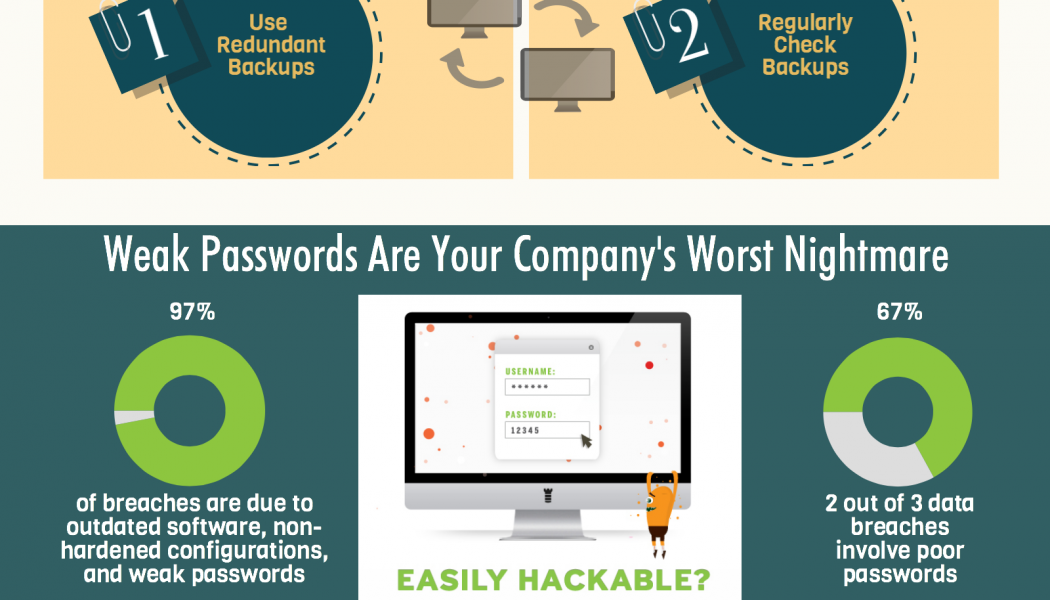
The cost and impact of cybercrime are climbing by around 15% every year, according to a 2020 report in Cybercrime Magazine, and is expected to cost $10,5 trillion globally by 2025. This makes cybercrime, they argue, more profitable than the global illegal drug trade. The real costs are far greater though, both broadly and to individual companies, as these funds represent lost investment and innovation, and companies increasingly face stringent fines for personal data losses under regulations such as the General Data Protection Regulation (EU GDPR) and Protection of Personal Information (PoPI) Act. The human layer All it takes is a chink in the armour, warns John Ward, SME of Cloud Business for Africa at Fortinet, and this can be through human error, misconfiguration, permissions-...
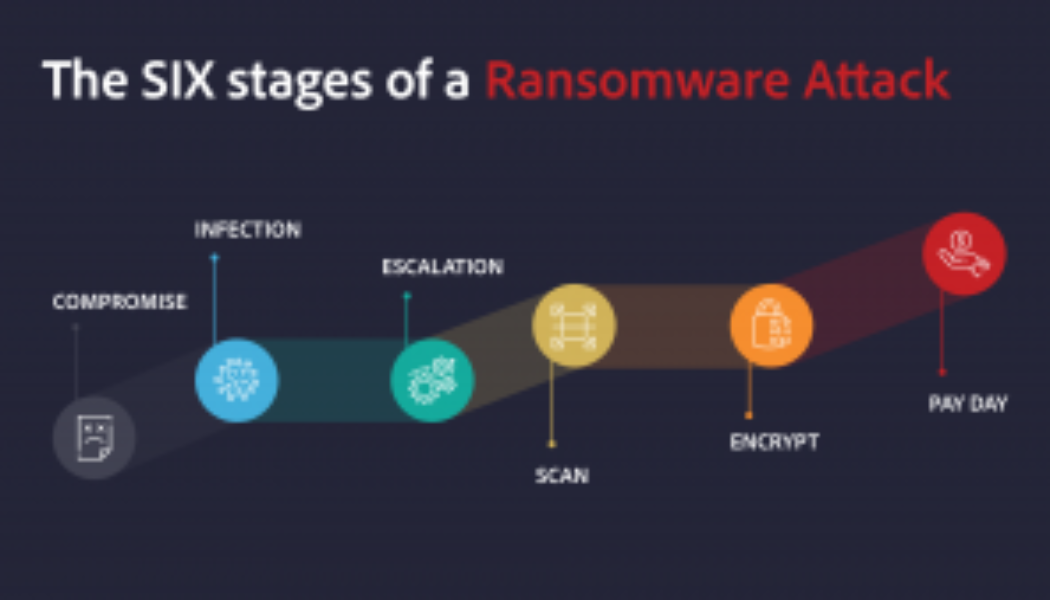
Unpacking Lessons from Ransomeware Attacks in 2021
It’s nearly impossible to read the news without seeing at least one headline blaring about a breach, hack or attack. In the USA, the Colonial Pipeline experienced a Darkside ransomware attack that affected more than 10, 000 gas stations. Virgin Active was hit by a hack in early May 2021 and took weeks to re-establish its systems. Vastaamo, a platform that provided therapy to thousands of patients, lost its data to hackers thanks to an unexpected security flaw. The hackers sent ransom demands to patients – pay up, or your personal information is public knowledge. As Stephen Osler, Co-Founder and Business Development Director at Nclose, points out, the criminal networks and masterminds behind digital attacks are doing their jobs and have every motivation to do these jobs extremely well. “The...
Why People Should Invest in a Culture of Zero Trust Security
Sourced from International IDEA During a preview of this year’s RSA conference, a team from Orange Cyberdefense demonstrated a range of pretty scary scenarios of what can happen when malicious actors take control over a user’s home router. These range from duping users into downloading payloads dressed up as fake VPN software updates, capturing user’s credentials or redirecting traffic that should be going over the VPN to the threat actor. Typically, home routers are outside of the enterprise security control and often not very well protected. The majority of people trust their ISP to set up their home access points for them, frequently resulting in default settings such as admin/admin credentials. Home routers are frequently attacked by criminal and state actors alike. Despite the easing ...
How to Create a Culture of Cybersecurity
Sourced from IDG Connect Security. This is a word that can make a grown CFO tremble and an entire SOC crumble. It is the word that captures a complex landscape littered with complexity, cybercriminals and technology. It defines how well an organisation adheres to a growing body of legislation – GDPR, POPIA and other data protection regulations – and how its reputation fares when a breach is revealed and information exposed. Security should be on every boardroom agenda, in ongoing employee training, and an investment into the right tools and solutions. But, perhaps most importantly, security should be an inherent part of the company’s culture because it is this factor that ultimately determines its security risk and posture. “There is a clear link between security culture and secure behavio...
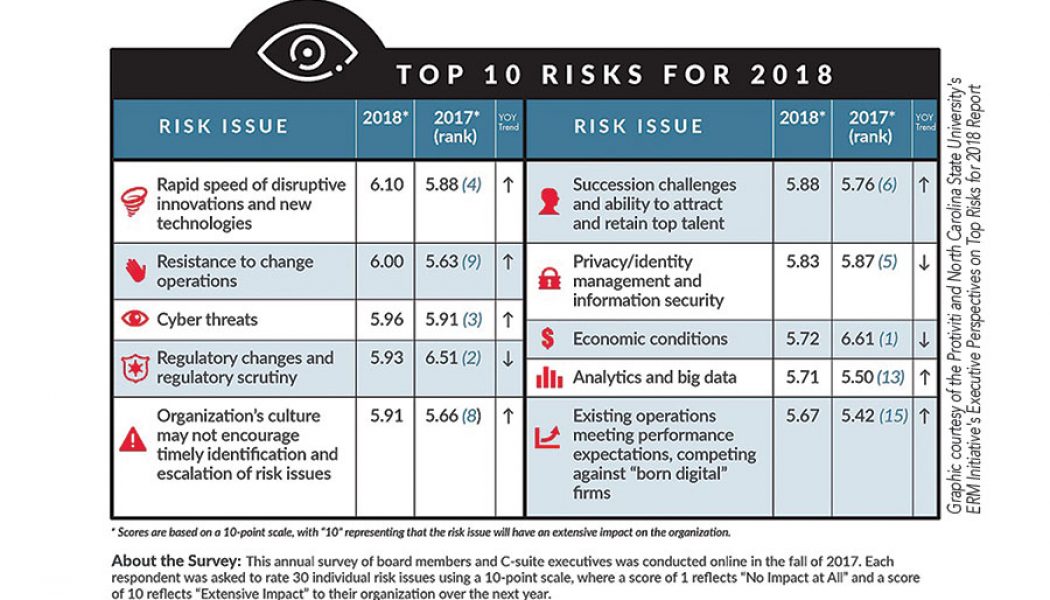
Why Cyber Attacks are Technology’s ‘Natural’ Disasters
Sourced from Forbes The SolarWinds attack was stunning in its scope and scale. If it were an earthquake, it would be 9.9 on the Richter scale. As digital transformation accelerates in 2021 and beyond—and applications accelerate as central enablers of business and all manner of digital life—cyberattacks have become technology’s natural disasters. Both have the power for profound devastation, threaten our sense of safety, and are (sadly) the reality of our world today. There is, however, one notable difference between a natural disaster and cybercrime. It is within our control to reduce the devastating impact of cybercrime. We can learn from the weaknesses the SolarWinds attack exposed and use this event as a catalyst for behaviour changes that will materially reduce the impact of future att...