cybercrimes
Awareness and Training Are Key in Defending Your Company from Blended Cyber-Threats
Image sourced from Finance Times. While blended cybersecurity threats are not new, they are fairly sophisticated and multi-staged in nature, meaning that they are difficult to protect against and can pose a considerable threat to organisations’ IT environments. A blended threat typically uses and exploits multiple vulnerabilities in an attack chain, says Brian Pinnock, Senior Director of Sales Engineering (EMEA) at Mimecast, adding that the severity of a blended threat will depend on the specific vulnerabilities that are targeted. “For example, a threat actor or cybercriminal will launch a phishing campaign against an organisation by sending emails with infected links that redirect to malicious websites. When a user clicks on these links, they could download a piece of malware like a Troja...
Recent Increases in Cyberattacks Could Be Due to Leaked Cyber “Superweapons”
Sourced from Forbes Check Point Research (CPR), the Threat Intelligence arm of Check Point Software Technologies Ltd., a leading provider of cybersecurity solutions globally, warns of a further increase in cyberattacks and thinks it could be partly down to major powers leaking, what they refer to as, ‘cyber superweapons’. “We have long warned that organisations of all sizes are being bombarded by a global fifth generation of cyber threats (Gen V). These are multi-vector cyber threats that can cause fatal damage and irreparable harm to the reputation of the compromised company,” said Pankaj Bhula, Regional Spokesperson at Check Point Software. “However, most companies are only secured against what we call third-generation threats (Gen III), which are threats that we’ve known about since the...
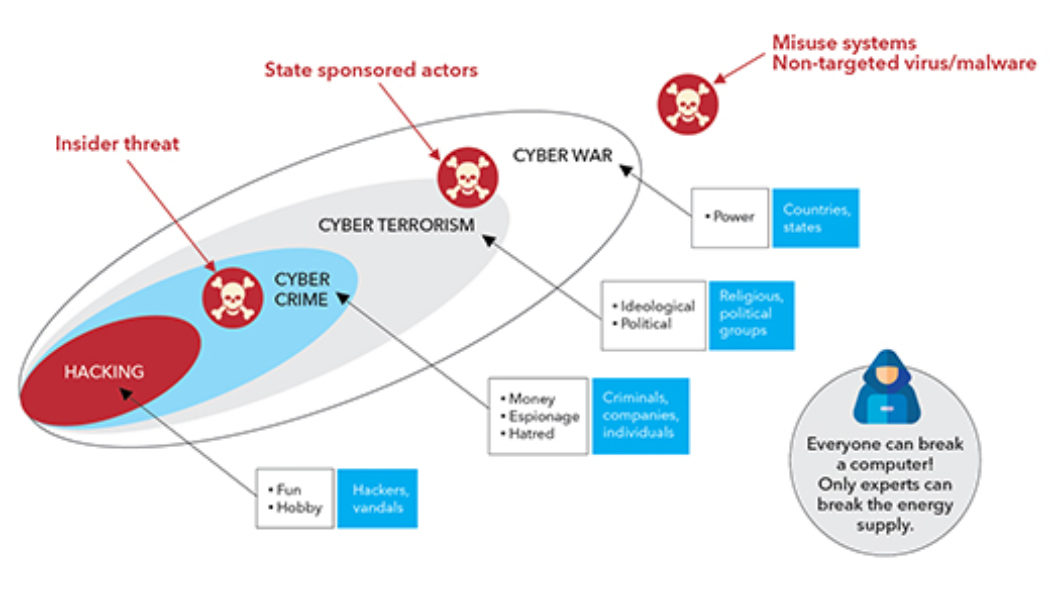
Is Cybersecurity as Necessary as Electricity?
Sourced from Travellers Cybersecurity has become as much a business necessity as having electricity says South African financial services and insurance company, Sanlam. Threat actors are constantly evolving and relentlessly hunting for vulnerabilities, cybercrime has become so profitable that exploitation is their business priority, and regulation is increasingly complex to navigate and manage. For Sanlam, cybersecurity has always been more than plugging holes and filling gaps, it’s a priority that has to be embedded within business foundations while managing cost, growth, customer experience, data analytics and regulatory controls. “Developing a comprehensive and holistic cybersecurity solution is a mandate for us, one that we must meet to ensure customer, stakeholder and industry trust. ...