cybercrime
What is POPIA and What Does it Mean for Cybersecurity
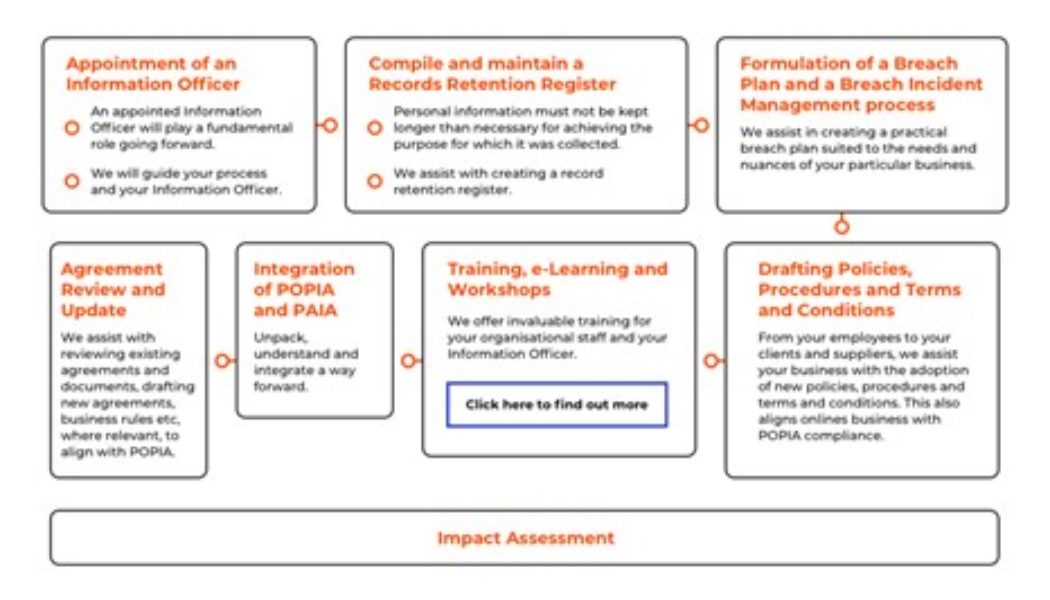
With an inundation of information from all angles regarding The Protection of Personal Information Act (POPIA), and the 1 July commencement date quickly approaching, organisations could be forgiven for feeling more than a little overwhelmed. Emmanuel Tzingakis, Technical Lead for Trend Micro Sub-Saharan Africa, contemplates how POPIA can assist organisations to secure their data and be better enabled to handle any potential cyber threats. What is POPIA? With personal information becoming a hot commodity on the dark web it is critical to understand exactly how to protect data from cybercriminals. A recent global survey revealed that 79% of organisations experienced disruptions, financial loss or other setbacks due to a lack of cyber preparedness in 2020. As work from home strateg...
How to Avoid Digital Fraud Over the Festive Season
With the festive season being synonymous with more transactions, especially as people typically have more money at this time of year, the greater the probability there is of fraud occurring. In fact, according to PwC’s Global Economic Crime and Fraud Survey 2020, South Africa has the third-most incidents of economic crime in the world behind India and China. “This festive season, I believe that there will be an uptick in fraud unless South African consumers and businesses are more security conscious,” says Nicho Bouma, CIO at Pay@. “More people have been forced to enter the digital space this year, due to the COVID-19 crisis. With many being new to the digital experience, they can easily fall prey to schemesters.” To prevent consumers from becoming victims of cybercrime, he urges them to o...
CSCS sensitizes financial market stakeholders on cyber-security
Central Securities Clearing System (CSCS) Plc, Nigeria’s capital market infrastructure, is ramping up its cyber-security advocacy as it sensitizes financial market participants on rising rate of cybercrime. In a webinar organized by CSCS, financial market stakeholders, including bankers and capital market operators dialogued on innovative measures for preventing cybercrimes, dire need for increased campaign and exigency of collaborative investments to reign in the rising rate of cybercrime. The online event themed “Cyber Security and Information During the Pandemic” was lauded for its timeliness, as COVID-19 pandemic and attendant remote connections may have increased cyber-security risks in many organizations, particularly as the crime rate surges globally, with rising exposure of financi...
South African Organisations Lag Behind Global Average of Cybersecurity Resilience
Email and data security company, Mimecast, unveiled its fourth-annual State of Email Security 2020 report. This report summarises details from 1,025 global IT decision-makers on the current state of cybersecurity. The findings in this year’s report demonstrate that despite high levels of confidence in respondents’ cyber resilience strategies, there is a clear need for improvement. While a large majority (77%) of respondents say they have or are actively rolling out a cyber resilience strategy, only 62% of South African organisations are doing the same. Yet an astounding 47% of local organisations – and 60% of global ones – believe it is inevitable or likely they will suffer from an email-borne attack in the coming year. South African respondents cite data loss (35%), a decrease in employee...
Web Skimming – A New Way to Steal Payments from Online Shoppers
Sourced from IOL. Researchers from cybersecurity and antivirus experts, Kaspersky, have uncovered a new technique for stealing users’ payment information on online shopping websites – a type of attack known as web skimming. Web skimming is a popular practice used by attackers to steal users’ credit card details from the payment pages of online stores, whereby attackers inject pieces of code into the source code of the website. This malicious code then collects the data inputted by visitors to the site (i.e. payment account logins or credit card numbers) and sends the harvested data to the address specified by attackers. Often, to conceal the fact that the webpage has been compromised, attackers register domains with names that resemble popular web analytics services, such as Google Analyti...
Google Launches Website to Help People Avoid Online Scams
Sourced from Google. Ever opened your emails and received a poorly-worded message about a payment that you weren’t expecting? What about one proclaiming that you’ve won a competition you never entered. “Congratulations!” it reads, beneath, a sinister attachment that you probably should not open. This is becoming more and more common, and now Google has unveiled a website to teach people how to spot and avoid online scams. Digital hoaxes, malware and cyberattacks have been surging during the ongoing coronavirus pandemic. The website – Scamspotter.org – tries to show users how to identify things such as false stimulus checks, fake vaccine offers, or other fake medical information. The site also attempts to make clear certain patterns that are typical of hoaxes, like a romance scammer asking ...