cybercrime
Take Steps Now to Protect Your Organisation as Ransomware-as-a-Service Ramps Up DDoS Attack Offerings
Image sourced from Ben Kerckx, Pixabay. The services industry has traditionally included sectors ranging from social assistance and health care to transportation and scientific services. However, it doesn’t end there, because the human talent for innovation can turn almost anything into a service. We also find – rather less top-of-mind for most people – the offer of hitmen-as-a-service, usually associated, at least in Hollywood, with large and well-muscled men in expensive suits and sunglasses. A few years ago, this area of business moved into the cyber arena as well. And so we present: ransomware-as-a-service. Today, one of its latest offerings is a ‘triple threat’ that turns Distributed Denial of Service (DDoS) attacks into an even more lethal cyber weapon against organisations. Carole H...
A Cyberattack Happens Every 11 Seconds, Choose Your Cloud Wisely
Sourced from International IDEA Cybersecurity experts predict that there is currently a cyberattack incident approximately every 11 seconds worldwide. This is almost double what it was in 2019 (every 19 seconds), and four times more than five years ago (every 40 seconds in 2016). Aside from these concerning statistics, what is even more alarming is the degree to which the sophistication of these attacks has grown. We are just over a year and a half into the pandemic and the way organisations approach cybersecurity has been embraced at an accelerated pace. With the vast majority of companies adopting fully remote or hybrid working arrangements, there has been a firm focus on the implementation of additional cybersecurity measures to keep critical operations secure. But, despite all efforts ...
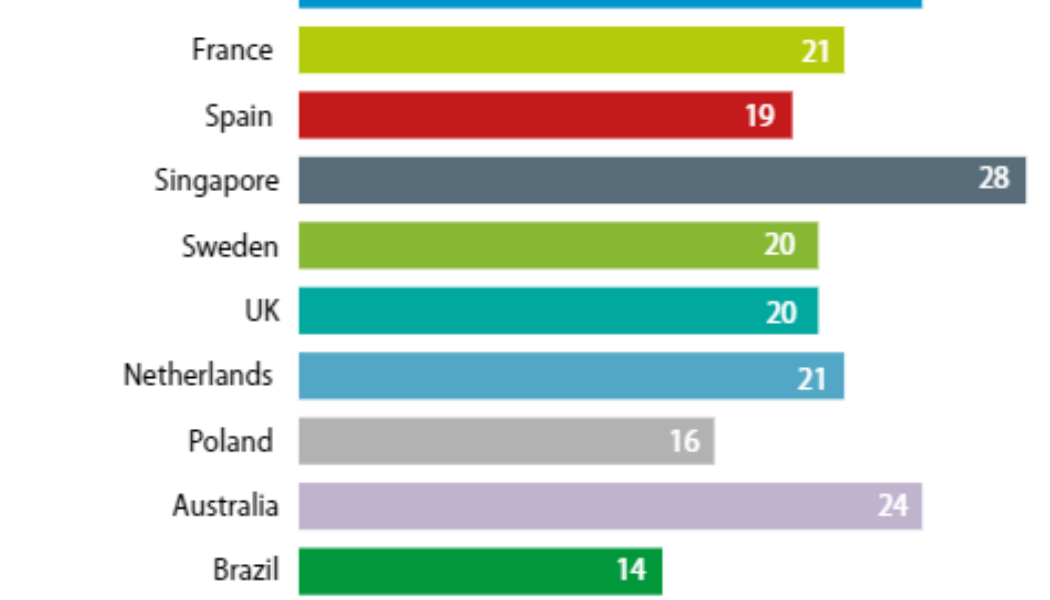
Only 20% of Cybersecurity Workforce Are Women Despite Industry Skills Deficit
Image sourced from OpportunitiesNB. “Diversity is more than gender. It is race, culture, ability and country. It is mixing up the talent pool and adding in the unique insights and perspectives that different people from different walks of life bring to create teams that are more engaging and innovative,” opines Anna Collard, SVP Content Strategy & Evangelist at KnowBe4 AFRICA. “It will also go a very long way towards filling the very real and very large security skills hole that is growing wider every day.” According to Collard, diversity is a critical and strategic step that the cybersecurity industry depends on to ensure longevity and ongoing security capability. “Women only make up about 20% of the current cybersecurity workforce and yet one of the top pain points for the CISO is th...
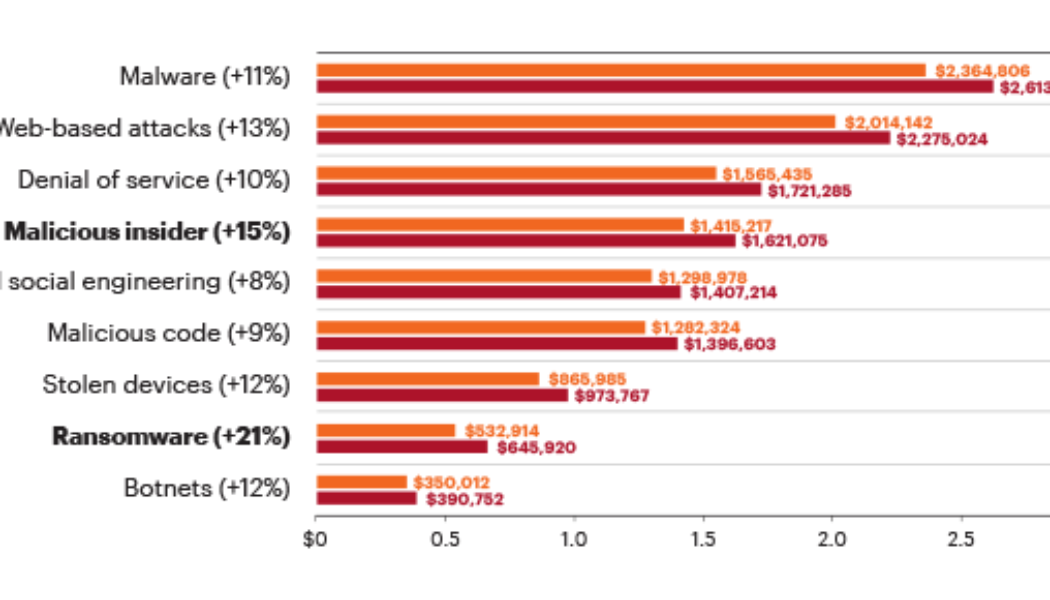
The High Cost of Cybercrime is Getting Higher
Image sourced from Finance Times. If cybercrime organizations could be publicly traded, we’d have an instant new multibillion-dollar industry sector. Indeed, cyber threats have become so pervasive that U.S. President Joe Biden recently signed an executive order aimed at improving federal cybersecurity in the wake of multiple significant cyberattacks, including the ransomware attack that shut down the Colonial Pipeline. Meanwhile, a broad coalition of experts in the industry, government, law enforcement, civil society, and international organizations have joined together in the Ransomware Task Force to build a framework for combatting ransomware. Ransomware attacks are only one method, however. Threat actors also use distributed denial-of-service (DDoS) attacks to ratchet up the p...
Using AI to Beat Cybercriminals at their Own Game
Artificial intelligence (AI) technology is a powerful technology, and because of this, it holds great potential for exploitation by cybercriminals. Considering this, the only way that security leaders can stay ahead of bad actors is by gaining a true understanding of how this technology can be weaponised. Then, they can begin to develop effective strategies for confronting AI threats head-on. Malicious Uses of AI Technology As AI grows in adoption and sophistication, cybercriminals are looking for ways to seize upon its potential. The Electronic Frontier Foundation was already warning about potential malicious uses of AI back in 2018, including threats to digital, physical, and political security. And now, AI precursors combined with swarm technology can be used to infiltrate a networ...
The Shift to Remote Working Has Led to Bad Online Security Habits
More than 50% of IT teams believe that employees have bad security habits. Habits they’ve developed since moving their offices into the home and that put their information, systems and employers at risk. The statistic comes from the Tessian Back to Work Security Behaviors Report that also found an age discrepancy when it came to who practised the best security from home. Around 51% of 16–24-year-olds and 46% of 25–34-year-olds reported that they used security workarounds, while two in five people said that the security behaviours they adopted at home were very different from those they used in the office. Training A Top Priority For Anna Collard, SVP Content Strategy & Evangelist at KnowBe4 AFRICA, this draws a thick red marker around the need to ensure that people and security trainin...
Cryptocurrency and Cybercrime: 3 Insights You Need to Know
Image sourced from Shutterstock. Criminals have kept pace with changing technologies by no longer wanting their crimes to generate hard cash – bitcoin has become the currency of choice. That’s particularly true for cybercrime, where ransomware is booming as criminals infiltrate organisations’ IT systems and threaten to publish or destroy crucial data unless a ransom is paid in Bitcoin. Here are 3 insights you need to know about the links between cybercrime and cryptocurrency: 1. Cryptocurrency is Fuelling Cybercrime Ransomware payments have become so huge that attacks are mounting daily. A recent high-profile case was an attack on the US Colonial Pipeline, causing the system that carries 2.5 million barrels of oil a day to be shut off. It’s become such a lucrative business that some syndic...