cybercrime
Most SAns Would Stop Trusting Brands Involved in Phishing Attacks – Survey
Image sourced from Kaspersky. According to the global Brand Trust survey by cybersecurity company Mimecast, almost three-quarters (74%) of South African consumers would stop buying from a brand if they fell victim to a phishing attack involving that brand, with 93% of South African consumers expecting their favourite brands to ensure their services, such as websites, emails and other communication, are safe to use. Heino Gevers, cybersecurity expert at Mimecast, says brands need to do more to protect their customers from cybercriminals. “South Africans are incredibly trusting with 69% of consumers not hesitating to open an email from brands they use regularly, and 56% readily clicking on links from their favourite brands. However, with cyber threats- including impersonation attacks and phi...
1 in 4 People Use Fitness Devices – Is Your Tracking Data Secure from Hackers?
Image sourced from Reuters. A recent study by the virtual private network provider NordVPN revealed that 1 in 4 (24.6%) people use some kind of fitness or well-being device, such as a smartwatch, fitness tracker, etc. However, these devices may be tracking a lot more than your fitness activities, and 25% do nothing to protect them, which may pose a serious risk to people’s privacy. Among the data collected by fitness wearables and the mobile apps connected to them, there are basic activities such as steps, heart rate, the time you go to sleep or wake up, as well as your consumed calories, weight, or even running routes, which are all of great interest to stalkers or attackers. For example, Clario research has revealed that Strava collects 41.18% of users’ personal data, and MyFitnessPal — ...
How to Successfully Recover from a Ransomware Attack
Sourced from Kaspersky South Africa is an attractive target for cybercriminals for a number of reasons, and the last few years have seen a sharp rise in high-profile ransomware attacks. One of the key motivations driving this volume of attacks is the fact that data is a de facto currency and an extremely valuable commodity on the black market. While backup is a critical component of data protection, when this backup is also encrypted by malicious software, companies are often left with few options other than to pay the ransom. Therefore, an effective Cyber Recovery strategy, which enables businesses to get back up and running without having to give in to criminal demands, is the key. Ransomware on the Rise The rapid adoption of digital transformation, Artificial Intelligence (AI) and the I...
The New DDoS ‘Normal’ is Not Normal in Any Way
Image sourced from Shutterstock. Threat actors will never turn down an opportunity for innovation, and the COVID-19 pandemic has provided an enormous such opportunity. We are seeing this quite clearly in the numbers coming through – and the new ‘normal’ around distributed denial of service (DDoS) attacks is not normal at all. So says Carole Hildebrand, Senior Strategic Marketing Writer at NETSCOUT, a leading global provider of service assurance, security and business analytics. Writing in a recent blog, she explains, “After an astonishingly active first quarter of DDoS attack activity, things calmed down a bit for the second quarter of 2021. Unfortunately, ‘calmed down’ is a relative term.” NETSCOUT decided to compare the numbers of DDoS attacks during the COVID-19 era of 2020 and 2021 thu...
Today’s New Business Normal Creates Threat Opportunities
Image sourced from Feed Navigator. The COVID-19 pandemic forced businesses of all shapes and sizes to make rapid changes in how they operated, with employees predominantly working remotely and sensitive data and systems being accessed from outside the office. For many, this triggered an increased reliance on remote-access infrastructure and cloud-delivered services. IT departments rushed to install, expand, or upgrade remote desktop access (RDA) servers, virtual private network (VPN) concentrators, and remote access routers to meet surging workforce demand for remote access to data centres. Moreover, widespread reliance on video conferencing apps forced many businesses to upgrade enterprise wide-area network and local-area network capacity, as well as to re-evaluate routing and DNS re...
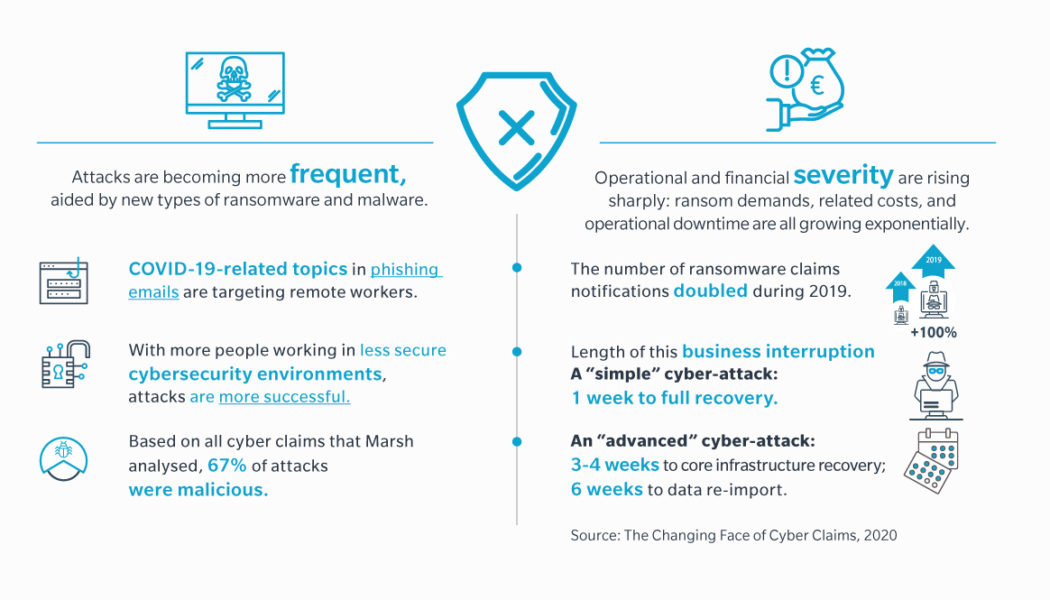
When Ransomware Strikes, Can You Recover Fast Enough?
Sourced from Kaspersky Ransomware attacks have become increasingly common, and they are even available on the dark Web to purchase as a service. There have been many incidents in the news, where major companies have been left with little choice other than to pay the ransom to get their data back, often amounting to hundreds of thousands of dollars. The reality is that ransomware and other cyberattacks have become a question of when not if. The ability to respond and recover quickly has therefore become an essential part of successful ransomware defence, but it is something many organisations, especially in South Africa, struggle with. Consider Some Statistics The State of Ransomware report from security firm Sophos reveals that, over the last year, the average cost of remediating a ransomw...