Cybercrime South Africa
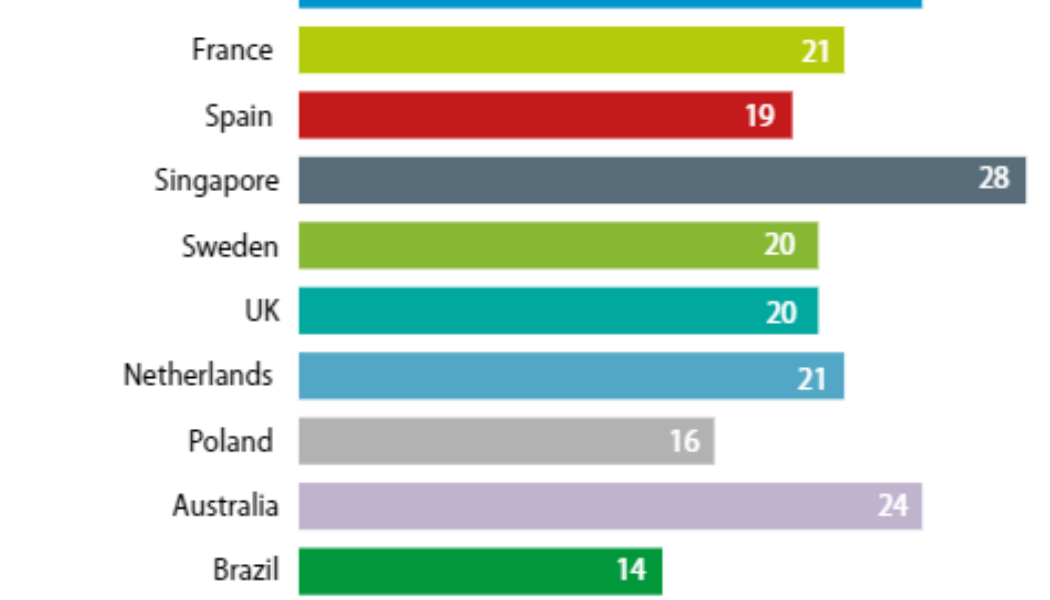
Only 20% of Cybersecurity Workforce Are Women Despite Industry Skills Deficit
Image sourced from OpportunitiesNB. “Diversity is more than gender. It is race, culture, ability and country. It is mixing up the talent pool and adding in the unique insights and perspectives that different people from different walks of life bring to create teams that are more engaging and innovative,” opines Anna Collard, SVP Content Strategy & Evangelist at KnowBe4 AFRICA. “It will also go a very long way towards filling the very real and very large security skills hole that is growing wider every day.” According to Collard, diversity is a critical and strategic step that the cybersecurity industry depends on to ensure longevity and ongoing security capability. “Women only make up about 20% of the current cybersecurity workforce and yet one of the top pain points for the CISO is th...
Awareness and Training Are Key in Defending Your Company from Blended Cyber-Threats
Image sourced from Finance Times. While blended cybersecurity threats are not new, they are fairly sophisticated and multi-staged in nature, meaning that they are difficult to protect against and can pose a considerable threat to organisations’ IT environments. A blended threat typically uses and exploits multiple vulnerabilities in an attack chain, says Brian Pinnock, Senior Director of Sales Engineering (EMEA) at Mimecast, adding that the severity of a blended threat will depend on the specific vulnerabilities that are targeted. “For example, a threat actor or cybercriminal will launch a phishing campaign against an organisation by sending emails with infected links that redirect to malicious websites. When a user clicks on these links, they could download a piece of malware like a Troja...
Surging DDoS Attacks Drive Growing Demand for Third Party Protection Services
Image sourced from Shutterstock. As the global workforce largely shifted to work-from-home in response to the COVID-19 pandemic, reliance on online services soared. Many businesses were able to successfully pivot to this new normal as remote connectivity allowed access to vital systems and data. But as is often the case, no good deed goes unpunished. As the latest NETSCOUT Threat Intelligence Report shows, cybercriminals have exploited new vulnerabilities created by remote work across a wide variety of vertical industries. Making matters worse, perpetrators no longer have to be particularly technology-savvy in order to pull off attacks. Today, it is easy and relatively inexpensive to access sophisticated attack tools via for-hire services: A cottage industry has sprung ...
Confidential Computing – Why Privacy Should be the Heart of Digital Experiences
Image sourced from Intel. In this past year, the consumer experience came to the forefront. As we faced various stages of lockdowns, we turned to online banking, seeing our doctors remotely, running our businesses using technology and socialising through a screen. Digital interactions became a part of our lives – ever-present and normalised as we navigated changes swept in by this pandemic. As our digital interaction became seamless and permeated through every aspect of our lives, privacy continued to be top of mind. We carried out our lives predominantly online – making many of us more vulnerable to fraudsters. As we navigated living our lives digitally, data theft dominated 2020 as the most common attack in the Middle East and Africa. Across the region, data theft and leaks accounted for...
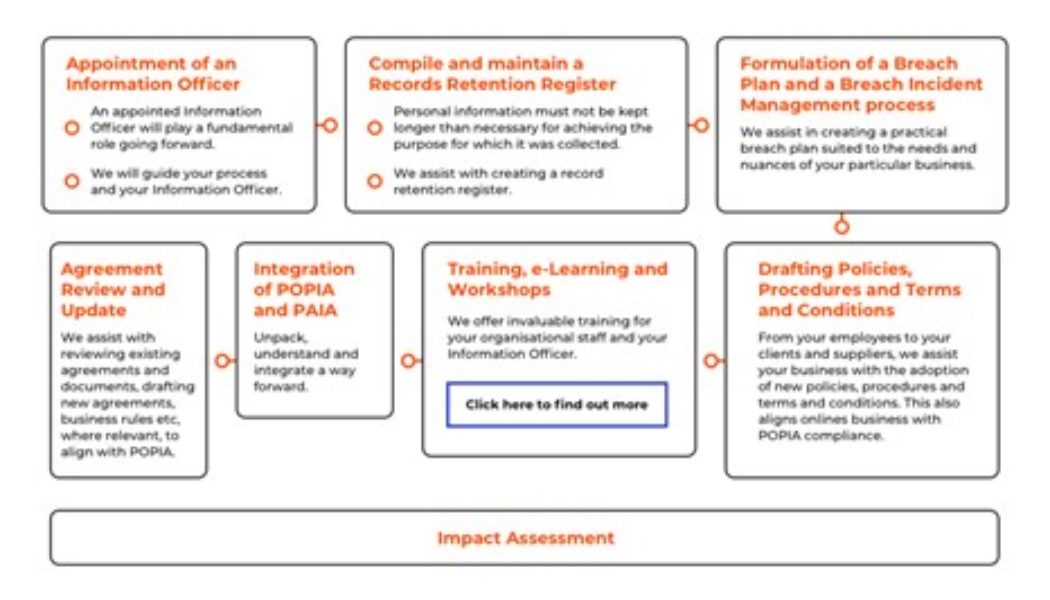
What is POPIA and What Does it Mean for Cybersecurity
With an inundation of information from all angles regarding The Protection of Personal Information Act (POPIA), and the 1 July commencement date quickly approaching, organisations could be forgiven for feeling more than a little overwhelmed. Emmanuel Tzingakis, Technical Lead for Trend Micro Sub-Saharan Africa, contemplates how POPIA can assist organisations to secure their data and be better enabled to handle any potential cyber threats. What is POPIA? With personal information becoming a hot commodity on the dark web it is critical to understand exactly how to protect data from cybercriminals. A recent global survey revealed that 79% of organisations experienced disruptions, financial loss or other setbacks due to a lack of cyber preparedness in 2020. As work from home strateg...