Cybercrime South Africa
Banking Malware Attacks Are “Becoming Increasingly Corporate” says Kaspersky
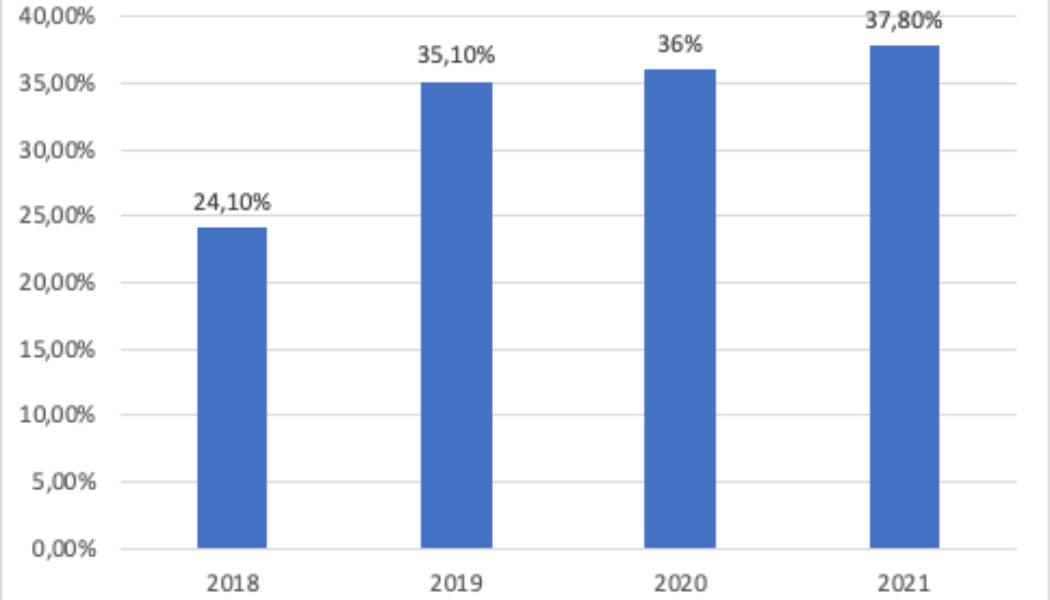
Image sourced from Finance Times. In 2021, the financial threats landscape witnessed positive changes where the overall number of users affected by malware reduced significantly, including a 35% drop in PC malware. Still, financial organisations, as cybercriminals’ most lucrative targets, continue to face massive threats. According to Kaspersky’s new Financial cyberthreats in 2021 report, attacks are becoming increasingly corporate rather than consumer-focused. In 2021, every third (37.8%) PC banking malware attack targeted corporate users, representing a growth of almost 14% since 2018. While 2021 saw an expansion in threats to financial organisations on a global scale, there was a continuation of the downward trend of PC and mobile malware previously seen in 2020. In fact, the numbe...
The State of Cyber Extortion Crime in South Africa
Sourced from Kaspersky The KnowBe4 and ITWeb Ransomware Survey took a deep look into the South African organisation, finding that ransomware and cybercrime are increasingly impacting organisations on the continent. While many companies (32%) were attacked in 2021, some multiple times (12%), 64% of organisations believe they are prepared, and 67% would not pay the ransom. According to Anna Collard, SVP Content Strategy & Evangelist at KnowBe4 Africa, the South African market with its growing economy and cyber dependence, is becoming increasingly tasty as a cyber extortion snack. Anna Collard, SVP Content Strategy & Evangelist at KnowBe4 Africa. “It is natural for cybercriminal organisations to look at emerging economies for future attacks, as they are often not as prepared as the re...
Is South Africa a Playground for Cybercriminals?
The Attacks From All Angles 2021 Mid-year Cybersecurity Report by Trend Micro highlighted a 47% year-on-year increase in email threats as well as malicious files and URLs in the first quarter of 2021 globally. South Africa’s technology landscape is almost identical to that of other countries, which has seen black hat hackers using it as a testing ground for cybersecurity attacks before these are launched on their intended end-users. Ransomware Remains the Prime Threat Globally, ransomware remained the standout threat in the first half of the year. The pandemic has highlighted how easy it is to buy ransomware as a service (Raas) on the dark web. Africa accounted for 1.7% of these attacks, with 1.05% being targeted at South Africa. Our findings show that locally, South Africa was in the top ...
UN Calls on Nigeria, Others to Tighten Cybersecurity Regulations
Sourced from UN The International Telecommunications Union (ITU), the global telecommunications arm of the United Nations (UN) has called on the government of Nigeria, and other governments across Africa to strengthen their Internet safety regulations. Because of the COVID-19 pandemic, and general shift online, many African countries are now more exposed to cybersecurity threats than before, necessitating renewed efforts into protecting these spaces. According to the Guardian Nigeria, the UN noted that in Africa, many countries have seen a rise in reports of digital threats and other malicious cyber activities. The results include sabotaged public infrastructure, large-scale monetary theft from digital fraud, and national security breaches. The UN says that addressing these vulnerabilities...
Today’s New Business Normal Creates Threat Opportunities
Image sourced from Feed Navigator. The COVID-19 pandemic forced businesses of all shapes and sizes to make rapid changes in how they operated, with employees predominantly working remotely and sensitive data and systems being accessed from outside the office. For many, this triggered an increased reliance on remote-access infrastructure and cloud-delivered services. IT departments rushed to install, expand, or upgrade remote desktop access (RDA) servers, virtual private network (VPN) concentrators, and remote access routers to meet surging workforce demand for remote access to data centres. Moreover, widespread reliance on video conferencing apps forced many businesses to upgrade enterprise wide-area network and local-area network capacity, as well as to re-evaluate routing and DNS re...
When Ransomware Strikes, Can You Recover Fast Enough?
Sourced from Kaspersky Ransomware attacks have become increasingly common, and they are even available on the dark Web to purchase as a service. There have been many incidents in the news, where major companies have been left with little choice other than to pay the ransom to get their data back, often amounting to hundreds of thousands of dollars. The reality is that ransomware and other cyberattacks have become a question of when not if. The ability to respond and recover quickly has therefore become an essential part of successful ransomware defence, but it is something many organisations, especially in South Africa, struggle with. Consider Some Statistics The State of Ransomware report from security firm Sophos reveals that, over the last year, the average cost of remediating a ransomw...
A Cyberattack Happens Every 11 Seconds, Choose Your Cloud Wisely
Sourced from International IDEA Cybersecurity experts predict that there is currently a cyberattack incident approximately every 11 seconds worldwide. This is almost double what it was in 2019 (every 19 seconds), and four times more than five years ago (every 40 seconds in 2016). Aside from these concerning statistics, what is even more alarming is the degree to which the sophistication of these attacks has grown. We are just over a year and a half into the pandemic and the way organisations approach cybersecurity has been embraced at an accelerated pace. With the vast majority of companies adopting fully remote or hybrid working arrangements, there has been a firm focus on the implementation of additional cybersecurity measures to keep critical operations secure. But, despite all efforts ...