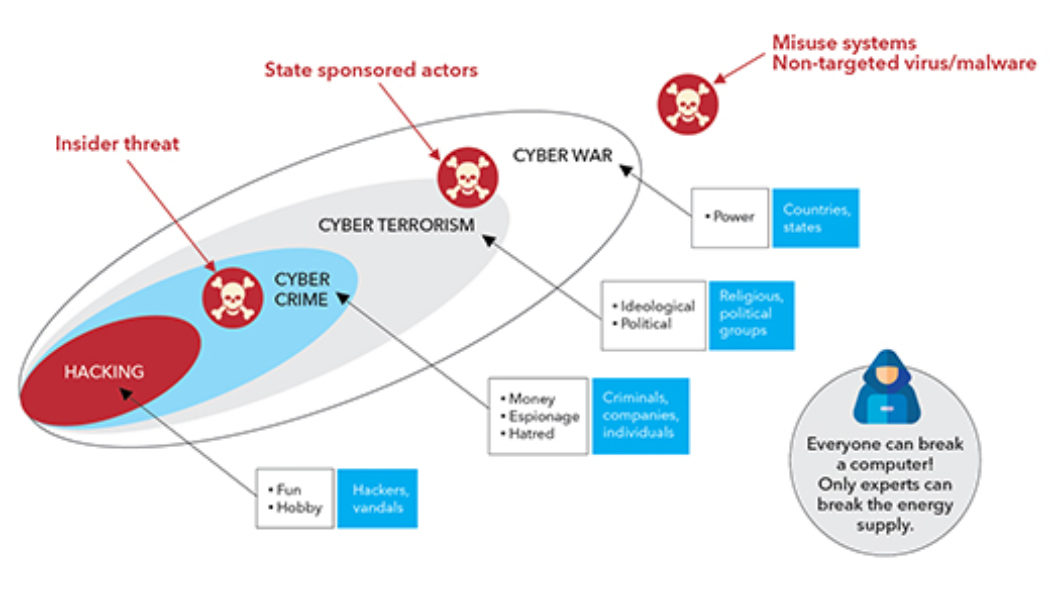
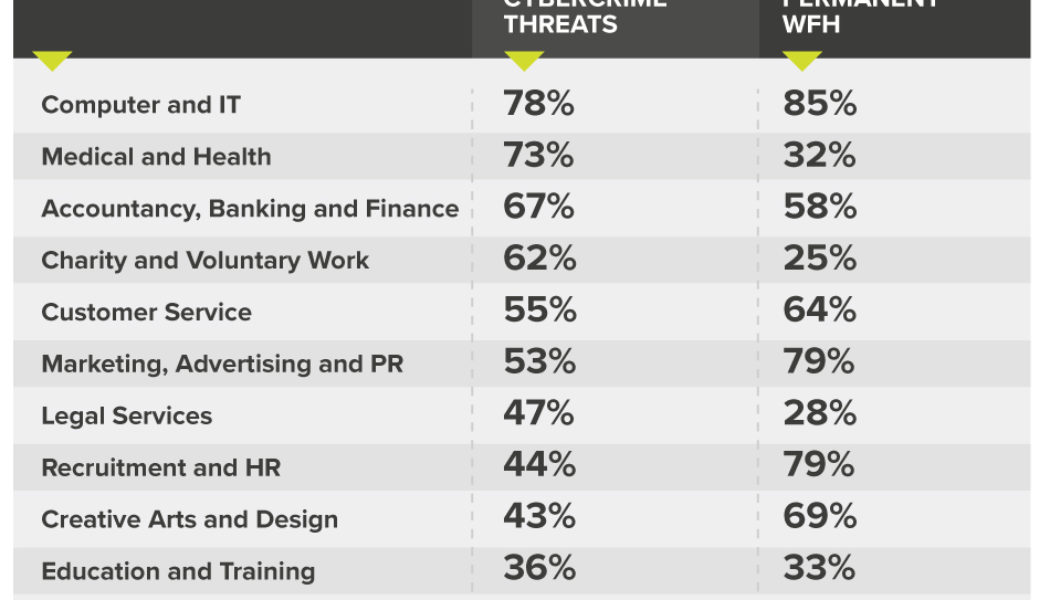
Cybercrime News
Cyber Threats on the Rise in Mining & Manufacturing Industries
Image sourced from Software ONE. Increasingly companies are looking to adopt smart technologies to optimise production and decision-making in order to create businesses of the future. However, as reliance on autonomous and digital technology grows, so too does the risk of cyber-attacks. As technologies become more interconnected, the potential cybersecurity threats and attack vectors are growing. The consequences of these threats can be severe, resulting in production and revenue losses, regulatory fines, reputational damage, as well as the shutdown of critical infrastructures. This has been further compounded by the complexities and uptake of smart systems that use advanced technologies such as machine learning and the Internet of Things (IoT). Mining, Manufacturing Under Threat Termed ‘S...
Broken Endpoints in Your Organisation’s Cybersecurity: The Role of Superior Endpoint Detection
Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited. Networks Unlimited is applying a ‘broken window, broken business’ principle when looking at an organisation’s internal cybersecurity posture, in order to have a positive effect on its business processes. The moral of the ‘broken window’ story, which has been studied by psychologists, is that once a window in a building is broken, people then feel that they are able to damage the property even further, and ultimately loot and steal from it, with impunity. “When we put this into a cybersecurity context,” says Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited, “this means, in essence, making sure that you have no ‘broken windows’ or gaps in your security through which uninvited elements coul...
IoT is One of Medicine’s Biggest Tools – Also Its Weakest Security Link
Image sourced from HP Consultant. /* custom css */ .tdi_4_0e2.td-a-rec-img{ text-align: left; }.tdi_4_0e2.td-a-rec-img img{ margin: 0 auto 0 0; } Healthcare has always been on the cutting edge, with hospitals and healthcare providers typically quick to embrace any innovation that will translate into better, more efficient, more affordable care. From microscopic pill cameras and implantable devices to laser surgery and advanced monitoring techniques, medical technology is all about creating the best possible patient outcome. But when it comes to the latest wave of innovative products, powered by always-on, always-connected internet of things (IoT) technology, there are growing concerns that security issues may eventually harm medical institutions or the patients themselves. /* custom css */...
Is Cybersecurity as Necessary as Electricity?
Sourced from Travellers Cybersecurity has become as much a business necessity as having electricity says South African financial services and insurance company, Sanlam. Threat actors are constantly evolving and relentlessly hunting for vulnerabilities, cybercrime has become so profitable that exploitation is their business priority, and regulation is increasingly complex to navigate and manage. For Sanlam, cybersecurity has always been more than plugging holes and filling gaps, it’s a priority that has to be embedded within business foundations while managing cost, growth, customer experience, data analytics and regulatory controls. “Developing a comprehensive and holistic cybersecurity solution is a mandate for us, one that we must meet to ensure customer, stakeholder and industry trust. ...