Cybercrime News
Forbes Cloud 100 Leader Rubrik Protects Your Data from Ransomware Attacks with Zero Trust Approach
Sourced from Kaspersky With data being increasingly valuable to a company’s organisations, ransomware attacks are surging around the world, including in South Africa. It is becoming incredibly lucrative for attackers to target businesses for their data, and at the same time, the ransomware being used is becoming more sophisticated. This means that more enterprises will feel the need to pay the ransom in the case of a breach. So says Risna Steenkamp, General Manager: ESM Division at Networks Unlimited, which distributes Rubrik solutions throughout Africa. “It is unfortunate,” she explains, “that in the event of a breach, paying the ransom is no guarantee that the threat actors will actually honour the agreement and release the data. This potentially leaves a breached organisation in the une...
NETSCOUT: The Long Tail of Adversary Innovation
Image sourced from Shutterstock. NETSCOUT’s ATLAS Security Engineering and Response Team (ASERT) observed a record-setting 5.4 million attacks in the first half of 2021, further confirmation that their “up and to the right” mantra would continue to hold true. As the findings from the 1H 2021 NETSCOUT Threat Intelligence Report show, the ongoing surge in DDoS activity is just one aspect of the dramatic global impact cyberattacks continue to have on private and public entities. “Cybercriminals are making front-page news launching an unprecedented number of DDoS attacks to take advantage of the pandemic’s remote work shift by undermining vital components of the connectivity supply chain,” stated Richard Hummel, threat intelligence lead, NETSCOUT. “Ransomware gangs added triple-extortion ...
Is South Africa a Playground for Cybercriminals?
The Attacks From All Angles 2021 Mid-year Cybersecurity Report by Trend Micro highlighted a 47% year-on-year increase in email threats as well as malicious files and URLs in the first quarter of 2021 globally. South Africa’s technology landscape is almost identical to that of other countries, which has seen black hat hackers using it as a testing ground for cybersecurity attacks before these are launched on their intended end-users. Ransomware Remains the Prime Threat Globally, ransomware remained the standout threat in the first half of the year. The pandemic has highlighted how easy it is to buy ransomware as a service (Raas) on the dark web. Africa accounted for 1.7% of these attacks, with 1.05% being targeted at South Africa. Our findings show that locally, South Africa was in the top ...
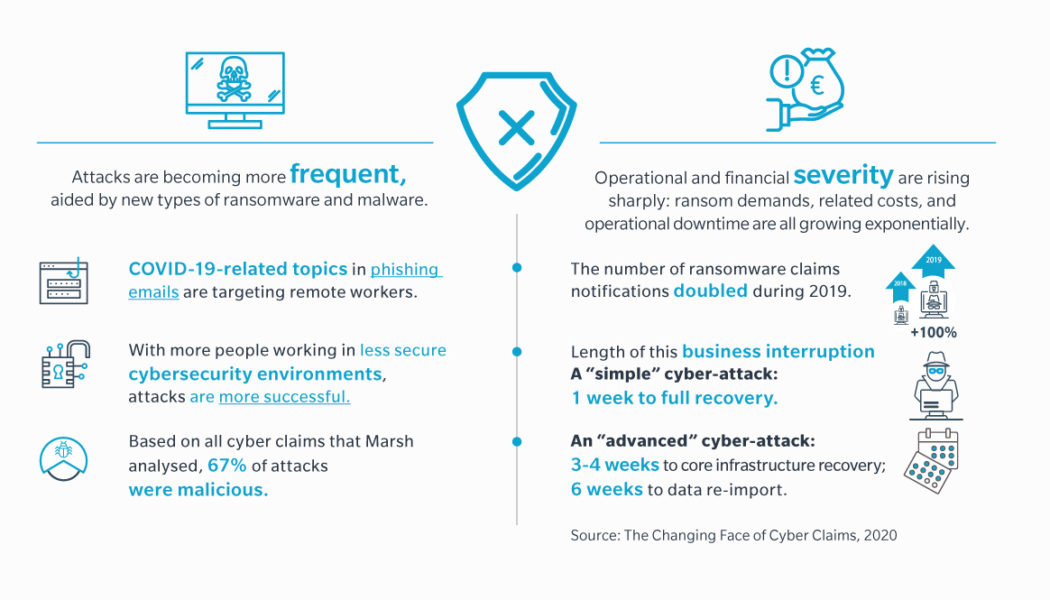
How to Successfully Recover from a Ransomware Attack
Sourced from Kaspersky South Africa is an attractive target for cybercriminals for a number of reasons, and the last few years have seen a sharp rise in high-profile ransomware attacks. One of the key motivations driving this volume of attacks is the fact that data is a de facto currency and an extremely valuable commodity on the black market. While backup is a critical component of data protection, when this backup is also encrypted by malicious software, companies are often left with few options other than to pay the ransom. Therefore, an effective Cyber Recovery strategy, which enables businesses to get back up and running without having to give in to criminal demands, is the key. Ransomware on the Rise The rapid adoption of digital transformation, Artificial Intelligence (AI) and the I...
With IoT in Healthcare on the Rise, Security Must Be A Priority says Fortinet
Image sourced from Alpine Security. South Africa is poised to start benefiting from a plethora of healthcare technologies that could dramatically improve patient care at a lower cost, boost preventative healthcare, and take the best medical practitioners virtually to the most underserved regions of the country. However, exciting new developments in healthcare technology could also put patients at risk in both the cyber and real world. This is according to Fortinet South Africa security experts Doros Hadjizenonos and Matthew Taljaard, who warn that the promise of emerging healthcare technologies could be derailed by security risks. Hadjizenonos, Regional Sales Director SADC at Fortinet, says Internet of Things (IoT) and Internet of Medical Things (IoMT) devices are increasingly being adopte...
Today’s New Business Normal Creates Threat Opportunities
Image sourced from Feed Navigator. The COVID-19 pandemic forced businesses of all shapes and sizes to make rapid changes in how they operated, with employees predominantly working remotely and sensitive data and systems being accessed from outside the office. For many, this triggered an increased reliance on remote-access infrastructure and cloud-delivered services. IT departments rushed to install, expand, or upgrade remote desktop access (RDA) servers, virtual private network (VPN) concentrators, and remote access routers to meet surging workforce demand for remote access to data centres. Moreover, widespread reliance on video conferencing apps forced many businesses to upgrade enterprise wide-area network and local-area network capacity, as well as to re-evaluate routing and DNS re...