Cybercrime Africa
How AI & Machine Learning Can Provide Defense Against Cybercrime
Nowadays, threat actors are leaning on new tools and techniques to improve the efficiency of their attacks. Only artificial intelligence (AI) and machine learning move quickly enough to defend organisations in this evolving cyber threat landscape. “In the past three months, we’ve been seeing more speed and speed can kill,” says Derek Manky, Chief Security Strategist & VP Global Threat Intelligence at FortiGuard Labs. Threats have been getting into a system, hitting the targets, exfiltrating data, demanding ransom, and getting out of a system, much quicker than normal. This includes attackers capitalizing on new vulnerabilities, zero-days and n-days. They also appear to have become more aggressive, with double extortion, triple extortion and targeted attacks. “Their approaches are more ...
Rubrik Security Cloud Secures Data Across Enterprise, Cloud, & SaaS
Image: Geralt, Pixabay. Rubrik, the zero trust data security company, has announced Rubrik Security Cloud to secure customers’ data, wherever it lives, across enterprise, cloud, and SaaS. Despite investments in infrastructure security tools, cybercriminals are still getting through to the data. ‘It’s time for a new approach,’ says Rubrik, clarifying that ‘The next frontier in cybersecurity pairs the investments in infrastructure security with data security giving companies security from the point of data.’ Russell Daly, Vendor Alliance Manager: Rubrik at Exclusive Networks Africa, which distributes Rubrik throughout Sub-Saharan Africa, adds: “Data is the most important aspect of your computing systems and the ultimate reason for their existence. With the rise of ransomware, the need ...
Update Your Security Strategy Based on Key Information Learned About Threat Actors, Advises Netskope
The reality of the cyber threats posed today is that many threat actors are not rogue operators acting on their own but are, instead, working as part of sophisticated and organised groups, collaborating with other groups within a wider ecosystem of specialists. These groups build significant financial resources over time, derived from the proceeds of commercially-driven attacks, or gathered as payment from states sponsoring or directly commissioning their activities. This is according to Yaroslav Rosomakho, Field CTO of Netskope, a global cybersecurity leader which is redefining cloud, data, and network security to help organisations apply Zero Trust principles to protect data. He explains: “Threat actors use these resources to improve their subsequent attacks, paying for infrastructure or...
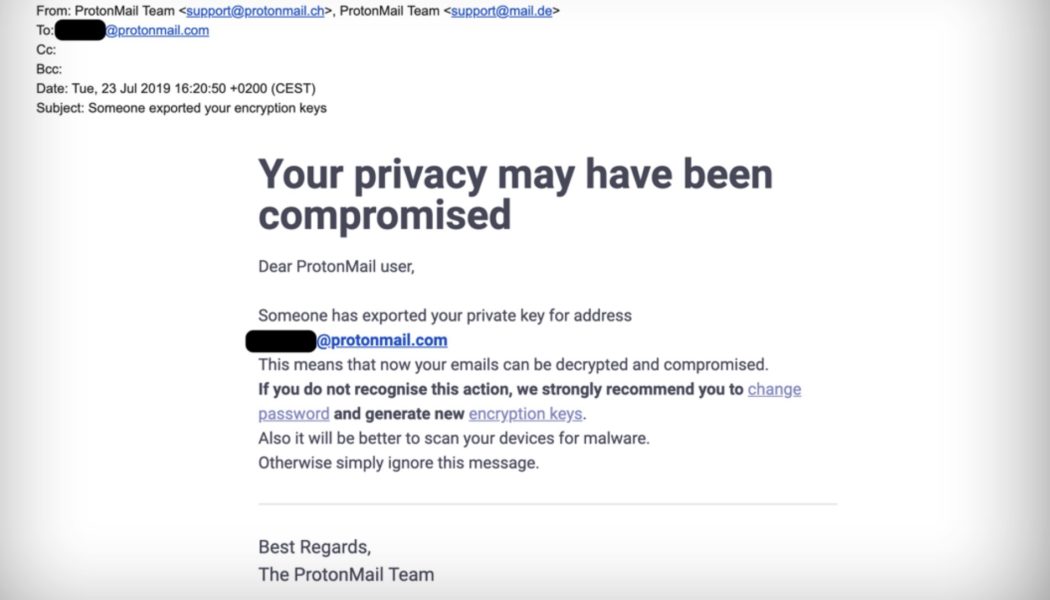
The Great Phishing Fail
Anna Collard, SVP Content Strategy & Evangelist at KnowBe4 Africa. In 2021, phishing attacks increased by 7.3% according to the ESET Threat Report, and the Cisco 2021 Cybersecurity threat trends report revealed that around 86% of organisations had at least one person click a phishing link. This echoes the findings of recent KnowBe4 Security Awareness Research that found people keep clicking – on fake emails from HR, the business and IT. As Anna Collard, SVP Content Strategy & Evangelist at KnowBe4 Africa, points out, the majority of top email categories that people fall for are those that fit in to everyday life – invoices, purchase orders, shared files, and COVID-19 related topics. “As our quarterly report on the top-clicked phishing tests shows, the emails that catch people are t...
How the Russia-Ukraine War Could Affect Cybercrime
Image sourced from Packetlabs. Russia’s war on Ukraine and its increasingly isolated internet environment could drive Russian cybercriminals to think outside the box and launch new forms of cyber attacks. This is according to Nclose’s Co-Founder & Technical Director, Martin Potgieter, who says speculation and concern is mounting around the world, over what Russia’s cyber crime syndicates’ next moves will be. “Currently, the cybercrime focus appears to be predominantly between Russia and Ukraine cybercrime groups and governments. While this is strictly speaking cyber warfare, it could quickly spread elsewhere. “What we are seeing is that a few of these cybercrime groups are either taking sides or imploding amongst themselves due to their Eastern European links with one another,” says Po...