cyber-threats
How a Data Breach Can Impact a Business Even Years After
Image sourced from Forbes. Modern enterprises face an onslaught of cyberattacks from many quarters and must not only be prepared to contend with the direct costs of potential breaches but also with spiralling indirect costs, such as compliance fines and reputational damage. As the threat landscape continues to evolve, so do the frequency and sophistication of attacks, with companies facing anything from denial of service attacks and phishing attempts to payment card skimming, identity theft, and account takeover threats. At the same time, ransomware attacks have gained prominence over the last few years, forcing companies to continually test their data protection plans to understand the risks associated with having sensitive data released to the public. In its State of Ransomware 2021 repo...
Omnis Security from NETSCOUT: Protect Your Network from the Threats You Can’t See
On 09 December 2021, the world was alerted to the Log4j vulnerability [CVE-2021-44228 aka Log4Shell]. It is likely that threat actors already knew about the vulnerability before this date, says Tom Bienkowski, NETSCOUT Product Marketing Director, because it’s been reported that the vulnerability had been exposed much earlier in Minecraft chat forums. How does Log4j work – and what lessons does it bring? Log4j, which is open-source software provided by the Apache Software Foundation, records errors and routine system operations and sends diagnostic messages about them to system administrators and users. A common example of Log4j is when a user types in or clicks on a bad weblink and they receive a 404 error message. The web server running the domain of the attempted weblink sends a message ...
Recent Increases in Cyberattacks Could Be Due to Leaked Cyber “Superweapons”
Sourced from Forbes Check Point Research (CPR), the Threat Intelligence arm of Check Point Software Technologies Ltd., a leading provider of cybersecurity solutions globally, warns of a further increase in cyberattacks and thinks it could be partly down to major powers leaking, what they refer to as, ‘cyber superweapons’. “We have long warned that organisations of all sizes are being bombarded by a global fifth generation of cyber threats (Gen V). These are multi-vector cyber threats that can cause fatal damage and irreparable harm to the reputation of the compromised company,” said Pankaj Bhula, Regional Spokesperson at Check Point Software. “However, most companies are only secured against what we call third-generation threats (Gen III), which are threats that we’ve known about since the...
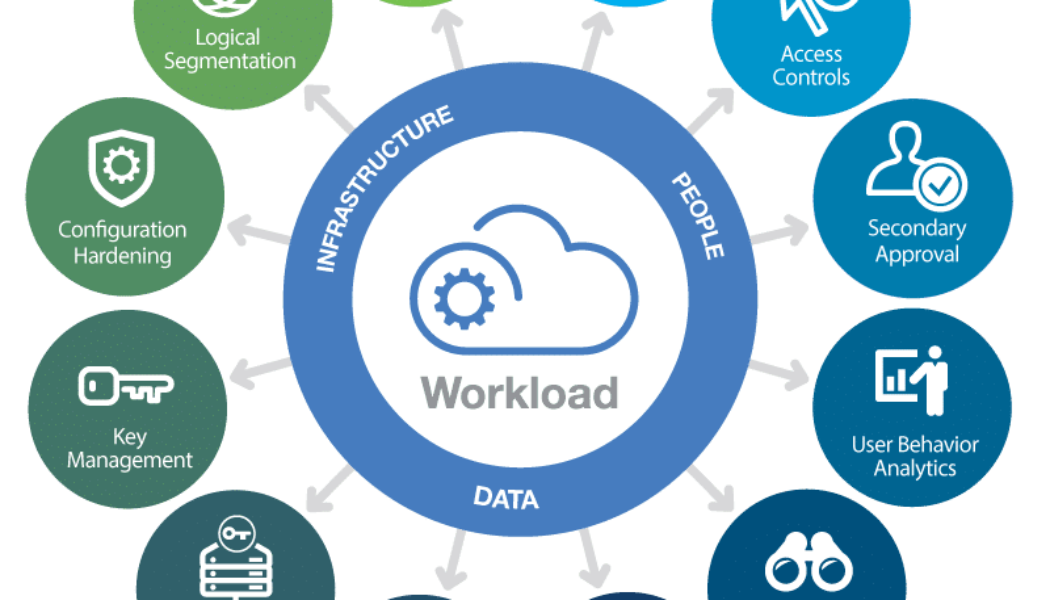
Hybrid Cloud Environments Provide Cheap Security for Financial Service Organisations
Sourced from ZDNet. Worldwide, financial services organisations are turning to the cloud as the means to transform outdated legacy systems and commit to disruptive technologies. The size of the public cloud market is expected to top $354 billion by the end of 2022, a significant jump from the less than $197 billion of 2018. But instead of going the all-or-nothing route, the hybrid cloud is positioned to provide companies with a more secure way of leveraging their data. Yunus Scheepers, CTO at SilverBridge, discusses these security benefits at a time when Microsoft Azure data centres in the country are attracting attention from financial services organisations as a safer alternative to what their current on-premise offerings can provide. A hybrid cloud environment also provides risk-averse ...