Cloud Computing
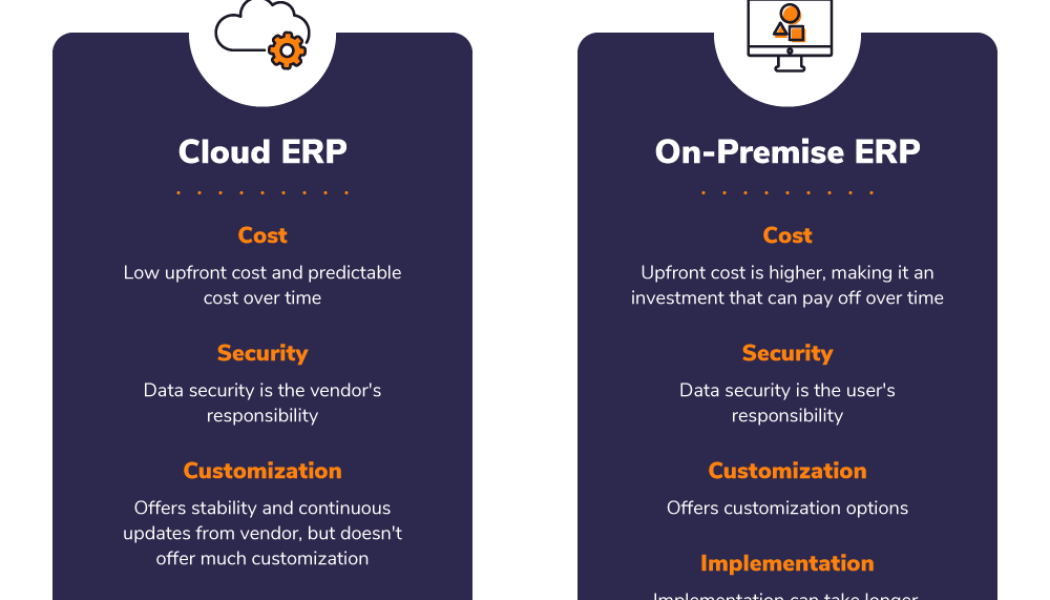
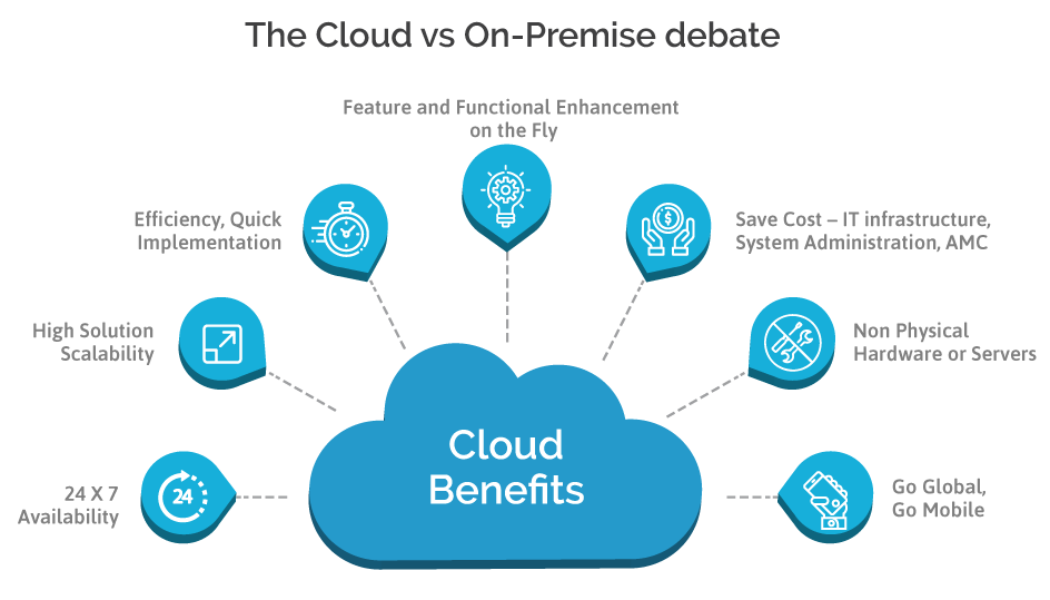
On-Prem ERP & the Cloud: How Do They Compare?
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
3 Things to Consider When Deploying Data Protection for Your Small Business
Small businesses are the backbone of every growing economy, bringing growth and innovation to the communities in which they are established. However, these businesses are often vulnerable when conforming to the new standards of remote work. Today, one of the greatest threats to small businesses is a cyberattack. According to the Wall Street Journal, companies with less than $10 million in annual revenue are less likely to be prepared for cyberattacks. Fireeye also reports that while 77% of all cybercrimes are directed toward small businesses, only 42% of small business owners are concerned with cyber security. The National Small Business Association reports that as many as 60% of small businesses will fail within six months of experiencing a significant cyber breach. These findings clearly...
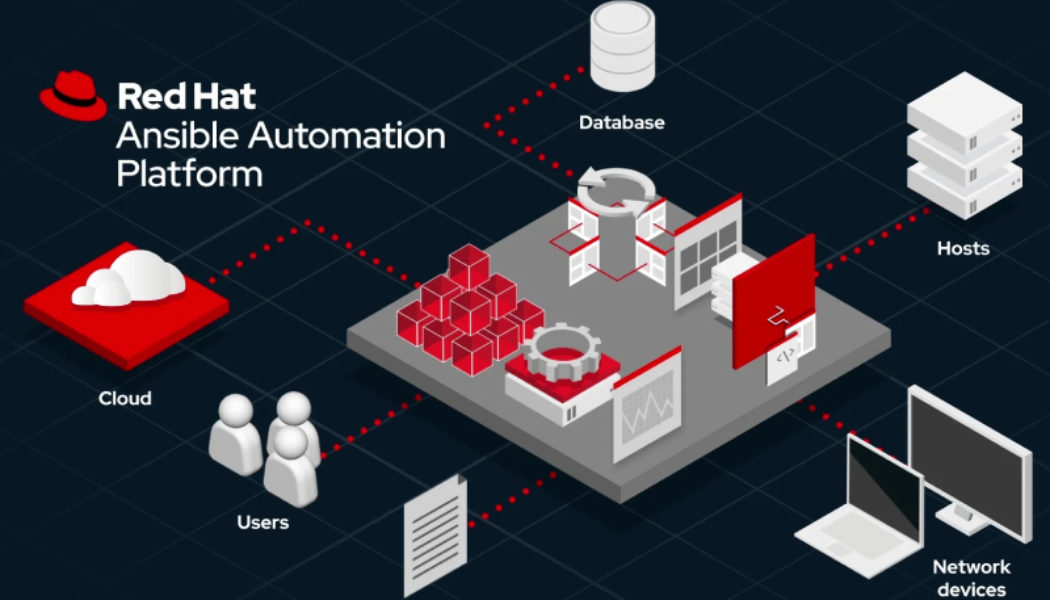
Red Hat Ansible Automation Platform Now Available on Microsoft Azure
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
A Step By Step Guide: 10 Key Steps to Build a Private Hosted Cloud
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
aYo looks to the cloud to power the future of microinsurance
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
Distributed Cloud WAAP Evolves F5’s Security-As-A-Service Offering Further for Securing Enterprise Apps
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
Sophos Acquires SOC.OS to Bolster its Cloud Security Offerings
Image sourced from Australian Reseller News. Sophos, the global cybersecurity firm, today announced that it has acquired SOC.OS, an innovator of a cloud-based security alert investigation and triage automation solution. SOC.OS consolidates and prioritizes high volumes of security alerts from multiple products and platforms across an organization’s estate, allowing security operations teams to quickly understand and respond to the most urgent cases flagged. The solution launched in 2020 and is a spinout of BAE Systems Digital Intelligence. The company is privately held and based in Milton Keynes, U.K. Sophos Bolsters its Cybersecurity Offerings with SOC.OS With SOC.OS, Sophos plans to advance its Managed Threat Response (MTR) and Extended Detection and Response (XDR) solutions for organizat...
Sophos Launches New Features for its Cloud Workload Protection
Image sourced from Australian Reseller News. Sophos, a global leader in next-generation cybersecurity, today unveiled new advancements to Sophos Cloud Workload Protection, including new Linux host and container security capabilities. These enhancements accelerate the detection and response of in-progress attacks and security incidents within Linux operating systems, improve security operations and bolster application performance. According to new SophosLabs research, distributed denial-of-service (DDoS) tools, cryptocurrency miners and various types of backdoors were the top three types of Linux threats detected by Sophos in a dataset from January through March 2022. DDoS tools accounted for nearly half of all Linux malware detections during this time, likely due to automate...
How Digital Thinking is Unlocking 4IR Revolution
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.