Check Point Security
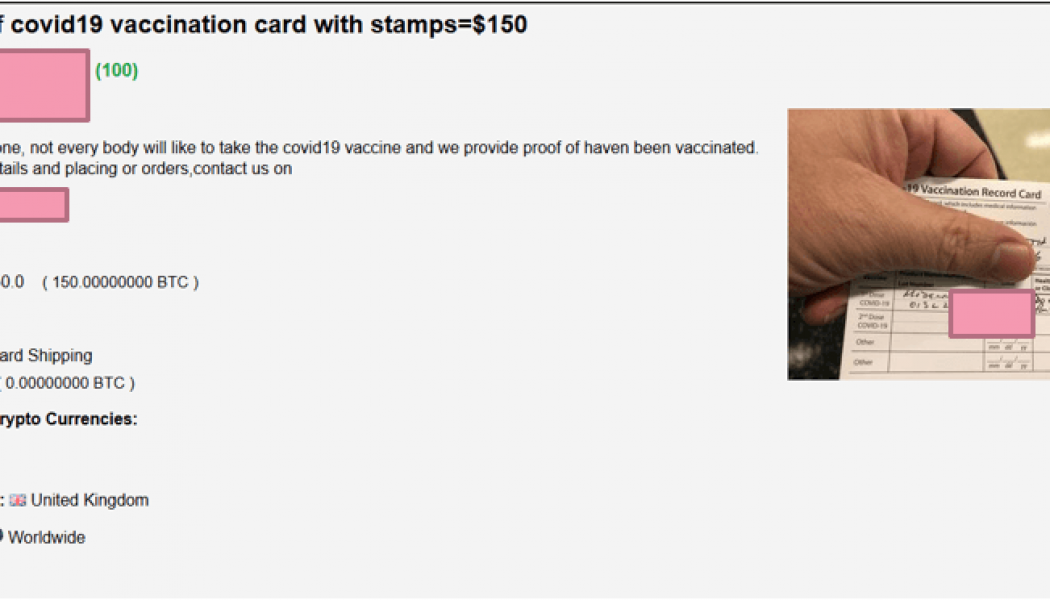
Fake COVID-19 Vaccination Certificates for Sale on the Dark Net
While the global roll-out of COVID-19 vaccinations continues to accelerate, it’s worth remembering that only around 1% of the world’s population have received their full course of injections. Billions are still waiting for their first dose, which inevitably leads those people to question exactly when they will get it. Especially as plans are being made internationally to allow those that have been vaccinated, or can prove they have had a recent negative test, the freedom to travel to other countries, attend large-scale events, take a new job, and more. So there’s a strong and growing demand for vaccinations and test results because of the greater freedoms they will give to people. And of course, there will always be people who don’t want to wait for their official vaccination, or for an of...